Estimated difficulty: 💜💜🤍🤍🤍
A nice quick read this month as we talk about the Cyber Threat Intelligence model the Pyramid of Pain.
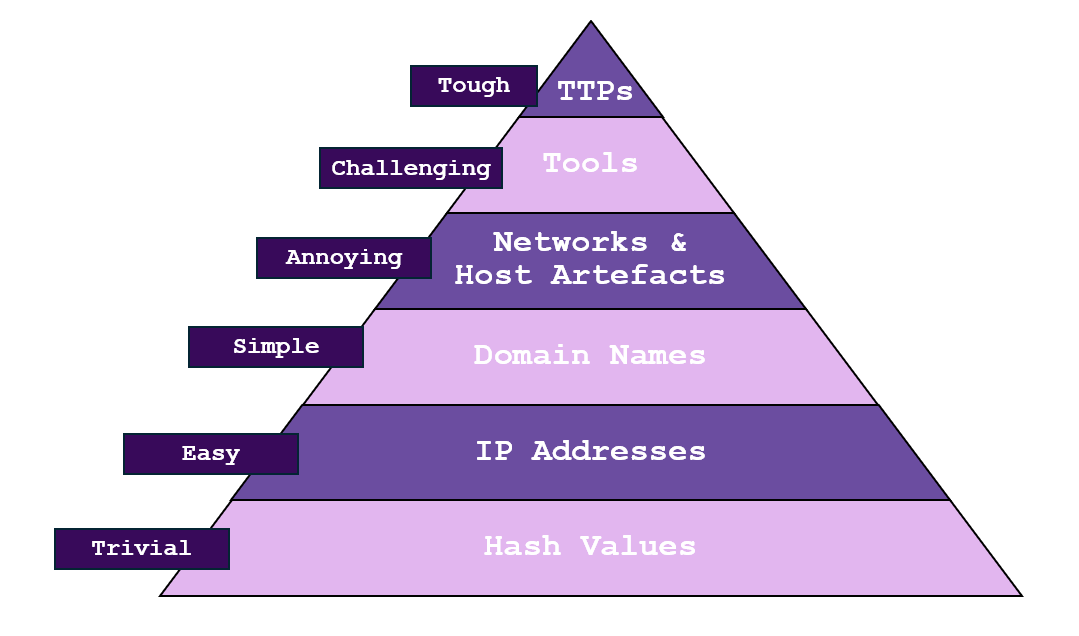
A long, long, time ago (2013) in a land far, far, away (the United States), David J. Bianco developed the Pyramid of Pain as a conceptual model to visually describe the challenges and fallout of identifying and addressing threats using various indications.
“This simple diagram shows the relationship between the types of indicators you might use to detect an adversary’s activities and how much pain it will cause them when you are able to deny those indicators to them.”
David J. Bianco
The pyramid is broken down into multiple layers, each of which stands for a different type of indicator that is used in threat identification and reaction. The higher up the pyramid you are, the harder it is for attackers to alter their behaviours and the greater the impact of identifying and sabotaging these signs.
The Pyramid of Pain emphasises that in order to recognise and respond to threats more effectively and significantly, attention must be paid to higher-level indications authored on the pyramid. By addressing these higher-level indicator tiers, defenders can severely diminish adversary capabilities in comparison to lower-level indicators. Often or not, the higher you go on the pyramid also signifies how difficult it may be for an adversary to alter that indicator during their campaigns.
Hash Values
Hash values signify the hash that corresponds to a specific file. Examples of file hashes include SHA1 or MD5, and usually represent a unique reference to malware files used in an attacker campaign.
Pain for Adversary: Low. Attackers can easily change the hash by modifying the file even slightly.
Detection Difficulty: Low. Hashes are easy to generate and compare.
IP Addresses
Pretty self explanatory… but may also include netblocks.
Pain for Adversary: Low to moderate. Attackers can change IP addresses through different means (e.g., using VPNs or proxies).
Detection Difficulty: Low to moderate. IPs can be monitored and blocked, but attackers can frequently change them.
Domain Names
Again pretty self explanatory… but may also include subdomains (securityqueens.com or secret.securityqueens.com). An example of use is they may be used be adversaries for their command and control (C2) servers.
Pain for Adversary: Moderate. Registering and changing domain names is more cumbersome than changing IPs.
Detection Difficulty: Moderate. Requires monitoring DNS traffic and domain registration.
Network & Host Artefacts
Artefacts are observables that have been caused by an adversary and left on either your network or host. Some examples of network artefacts could include URI patterns, whilst host artefacts could include things like registry keys. Artefacts can be used to distinguish between normal and adversary behaviour.
Pain for Adversary: Moderate to high. Attackers must significantly alter their tactics to avoid detection.
Detection Difficulty: Moderate to high. Involves deeper analysis and correlation of network and host activity.
Tools
Tools are the erm, tools that are used by an attacker during their campaign. Tools can be described as the software or utilities an adversary may use to achieve their objectives, for example the installation of a backdoor to enable C2 communications.
Pain for Adversary: High. Developing or obtaining new tools requires time and resources.
Detection Difficulty: High. Identifying specific tools can be challenging and requires thorough analysis.
TTPs
TTPs, also known as Tactics, Techniques and Procedures, describes the specific behaviours and strategies that attackers employ to accomplish their goals. This could mean anything from reconnaissance to data exfiltration, an example of a well-known TTP can be spearphishing.
Pain for Adversary: Very high. Changing TTPs means fundamentally altering the way they operate, which is resource-intensive.
Detection Difficulty: Very high. Requires deep understanding of the attack methodologies and proactive defense strategies.
Cyber defenders can build a more resilient and robust defence by utilising the Pyramid of Pain, hence increasing the difficulty of an attacker’s success.
Benefits of using the Pyramid of Pain include…
- Improving Prioritisation of Response Efforts: Helps prioritise detection and response efforts based on the impact and difficulty for attackers.
- Better Resource Allocation: Informs the allocation of resources to areas that will disrupt adversaries the most.
- Improved Detection: Enhances the overall detection capabilities of the defence team by focusing on harder-to-change indicators (top of the pyramid).
To test your new-found knowledge on the Pyramid of Pain, you can give TryHackMe’s lab a go.
Alternatively, you can also find David’s original blog post here.
Until next time!
– Sophia x