Estimated difficulty: 💜💜🤍🤍🤍
Welcome to another blog focusing on my journey into Threat Intelligence, this time introducing the MITRE ATT&CK framework and the concept of Tactic, Techniques and Procedures (TTPs).

Phishing is one of many techniques used by adversaries!
What are TTPs?
Tactics, Techniques and Procedures are used to identify the methods or patterns of activity that are used by a threat actor or group.
TACTICS: Tactics describes (at a high-level) the overall goal of the attacker (why is the attacker doing it?)
TECHNIQUES: Technique identification may be used to understand how an attacker has compromised a system or network
PROCEDURES: Procedures describe the specific implementation of a technique that an adversary uses to executive a tactic and/or goal (such as tooling) (in relevance to MITRE ATT&CK, this could be one or several sub-techniques used together)
Using TTPs allows analysts to corroborate intelligence and identify potential threats or areas of risk for a target organisation or system. The MITRE ATT&CK framework comprises of a list of common TTPs used by known actors and attackers, and centralises intelligence that is free and accessible to anyone and everyone to use.
For the purpose of this blog, we will be focusing on MITRE ATT&CK Enterprise, which provides specific guidance for adversarial behaviours in Mac, Windows, Linux and Cloud environments.
MITRE ATT&CK for Enterprise
MITRE ATT&ACK stands for MITRE Adversarial Tactics, Techniques and Common Knowledge (ATT&CK). The framework was created to collate knowledge specific to adversary behaviour and allow the ability to identify the different phases of an adversary attack lifecycle. MITRE ATT&CK is commonly used for threat hunting and profiling, as well as another framework to use in parallel with the Cyber Kill Chain. Created in 2013, the framework was created to help understand and analyse common tactics used by adversaries when they attack or compromise a system.
The framework consist of a set of techniques used by adversaries, split into categories represented as tactics in the MITRE ATT&CK matrix.

There are 14 tactics specified in MITRE ATT&CK for Enterprise:
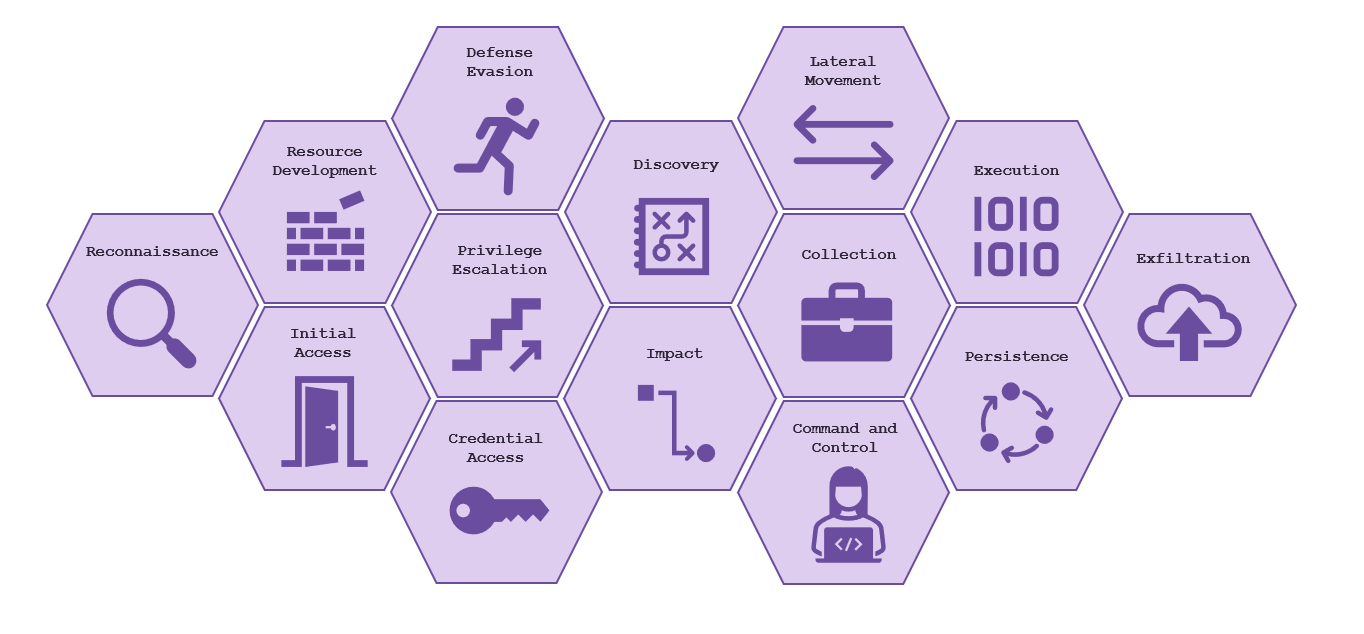
- Reconnaissance: Gathering information about a target to plan the attack or campaign
- Resource Development: Establishing the resources to support the attack e.g. setting up infrastructure, obtaining stolen accounts
- Initial Access: Compromising a network to gain access
- Execution: Executing malicious code to help obtain the attacker goal
- Persistence: Maintain access in the network to ensure a continuous foothold
- Privilege Escalation: Gain higher level permissions or privilege in a network e.g. administrator
- Defense Evasion: Avoid being detected
- Credential Access: Obtain access or control over accounts (stealing passwords and account names)
- Discovery: Mapping out the environment of the compromised network
- Lateral Movement: Moving between systems on the network e.g. using stolen credentials to access other computers or systems
- Collection: Collecting any stolen data that may aid the adversary in its goal
- Command and Control: Establishing communications between the attacker and the victim to maintain control over compromised systems
- Exfiltration: Stealing data and exfiltrating it to the attacker
- Impact: “manipulate, interrupt, or destroy the systems and data”
Within each tactic column of the matrices you can also find specific adversary techniques which describe the type of action an adversary may undertake. Many techniques also have “sub-techniques” which describe the different methods used by an attacker to execute that technique.
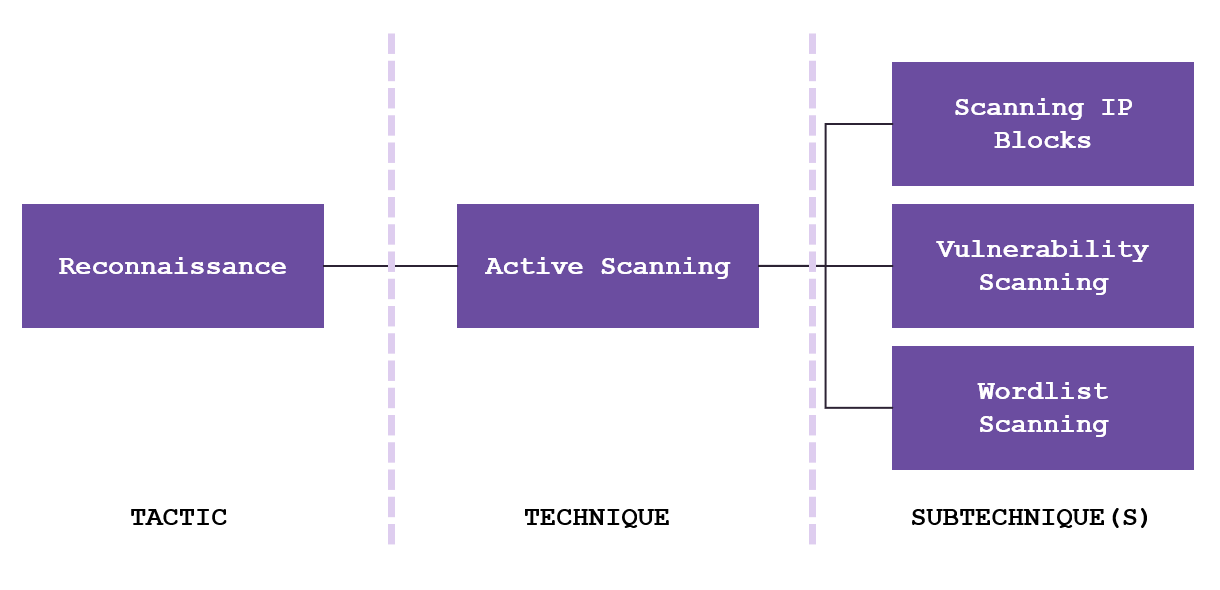
MITRE ATT&CK is often used by analysts to map scenarios to understand the attack in greater detail.
Let’s consider the following scenario!
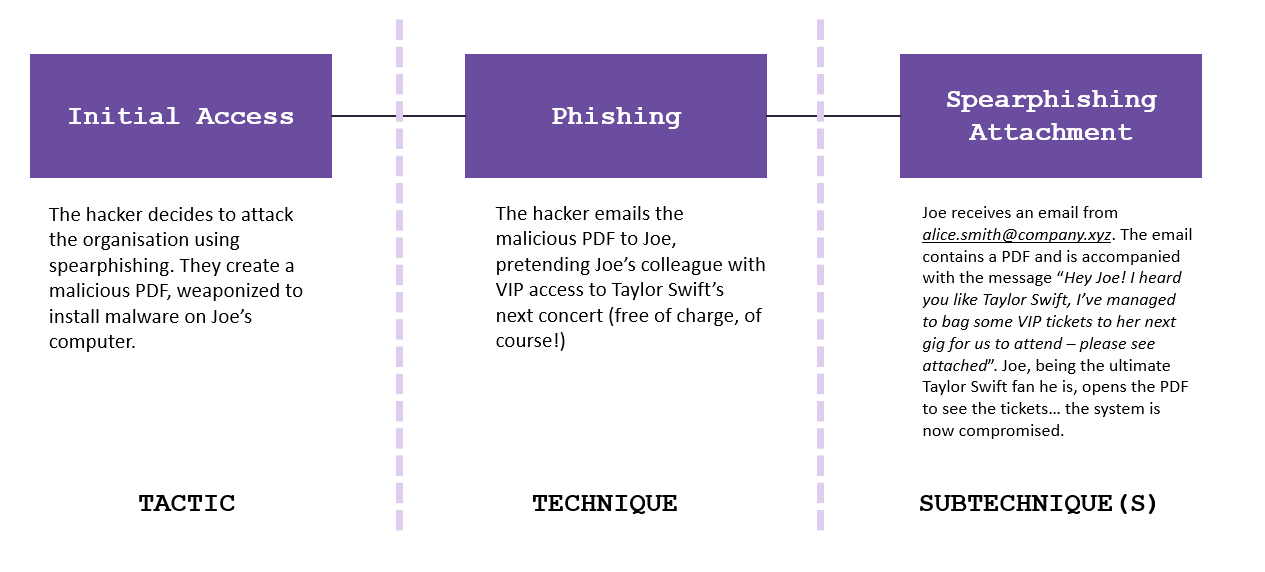
A hacker has been hired by a company to steal proprietary information from a competitor. During the reconnaissance phase, the hacker identifies an employee named Joe Bloggs. Joe Bloggs also has a Twitter account, where he regularly tweets about his love of Taylor Swift. On Joe’s LinkedIn it is also possible to find out his work email, joe.bloggs@company.xyz…
An analyst can map the tactics and technique used in an attack, similar to the figure above, to understand how Joe got compromised:
You can also use the ATT&CK navigator to explore an map different tactics and techniques from the matrices. You can have a play around with the navigator here.

I found this cartoon series online, and just had to throw in a few more to this blog…
Why choose MITRE ATT&CK?
Not only can MITRE ATT&CK be useful in analysing compromises in hindsight, it can also be integrated into an organisation to improve security awareness and posture by…
- Emulating adversary behaviour (how would an adversary attack us? would our system be able to withstand their tactics and techniques?)
- Performing red team operations (can we try to simulate our own attack on our systems? can we assess the impact of tactics and techniques on our system through a penetration test?)
- Performing analytics (can we continue to analyse and keep track of threat activities and insights?)
- Assessing the gap in security defense (what holes do we have in our defenses? what tactics can we identify that could potentially compromise our systems?)
- Evaluating SOC operations (how quick and effective would the SOC be to respond to an attack? could we test the SOC by deploying tactics and techniques against our systems?)
- Enriching intelligence (how can we continue to keep informed on adversary tactics and techniques? have we checked the MITRE ATT&CK framework recently, as it is continuously updated by the community?)
MITRE ATT&CK truly is for everyone and anyone in an organisation. The framework is continually updated to reflect the current threat trends and landscape, and not only is useful in a threat intelligence environment but can be utilised by cross-IT operations too.
MITRE ATT&CK provides a centralised environment to create, collect, share and manage information and continues to be one of the most widely used frameworks in the cyber security space… and hopefully after this blog, you can start to use it too!
References
- Mastering Cyber Intelligence by Jean Nestor M. Dahj, 2022
- https://attack.mitre.org/
- nhttps://www.balbix.com/insights/tactics-techniques-and-procedures-ttps-in-cyber-security/