Estimated difficulty: 💜🤍🤍🤍🤍
As some of you may now know, I’ve recently switched to the (potentially dark?) side of Cyber Threat Intelligence (CTI). Don’t worry, I’ll still be doing car hax – but also have a new found love for all things threat intelligence and open-source (OSINT)!
As I start this new chapter of my cyber journey, I’m currently studying to be a CREST Registered Threat Intelligence Analyst (CRTIA). To help my revision, and also share the knowledge I’m learning on the way, I thought it would be good to start with the basics and talk about the Threat Intelligence Lifecycle.
What is Threat Intelligence?
Threat intelligence allows businesses and organisations to collect, process and analyse data to help understand threat actor motives, targets and behaviours. Embedding threat intelligence into an organisation can also help senior leaders make better informed decisions to proactively fight against threat actors. It is absolutely essential to understand the threats to a business or asset and the types of methodologies used by these adversaries to conduct cyberattacks against a target. We can do this by corroborating the Tactics, Techniques and Procedures (TTPs) associated with threat actors and groups (watch this space for another blog on how to efficiently use TTPs).
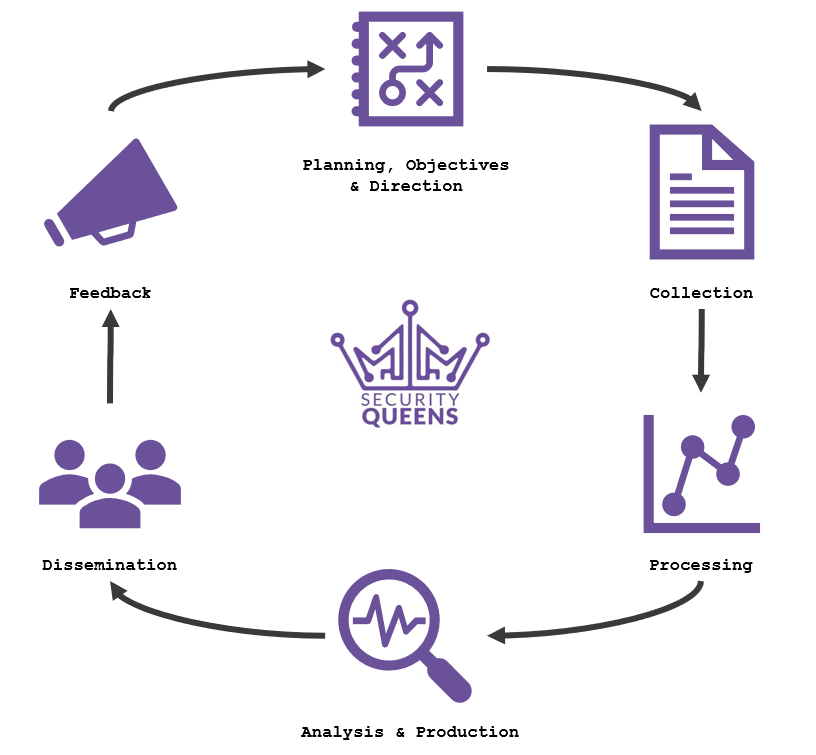
One of the ways to successfully implement threat intelligence into an organisation is by using the threat intelligence lifecycle… which brings us to the start of today’s blog.
Step 1: Planning, Objectives and Direction
The first step of the lifecycle is to (surprise, surprise) plan! Arguably the most important step of the lifecycle, it allows teams to define their intelligence requirements, objectives and strategy for integrating threat intelligence into the organisation.
Typically main CTI objectives include defining preventative measures such as threat monitoring and supporting security operation centre and incident response teams. Whilst supporting operational level threat intelligence, it is also important to define strategic level objectives to support stakeholder decisions at executive functions and levels.
After defining the requirements and objectives for the threat intelligence project, you should also determine the consumer of the results from the threat intelligence activities (if the consumer is an analyst, should the end product be more technical? If the consumer is executive management, should it be higher-level?)
Step 2: Collection
There is no intelligence without data.
And this is hugely critical to understand! Data must be collected to produce actionable intelligence to fulfil the requirements and objectives determined in Step 1 of the lifecycle. Collecting raw data from multiple sources helps strengthen the consumable information and can be divided into both internal and external sources…
- Internal: Internal sources should build the foundation of the data, and could include things such as network logs or evidence from previous incidents.
- External: External sources help bring more visibility to potential threats and my include research through blogs, magazines, and other open-sources.
Step 3: Processing

Once the raw data has been collected, the threat intelligence team would start to process the data which could include structuring and grouping the data as well as removing irrelevant data that is not relevant to the specified objectives. Processing data may include visualising and organising the data into spreadsheets, charts, and matrices depending on the tools, frameworks and platforms a CTI team or analyst has chosen.
Step 4: Analysis & Production
The analysis phase is absolutely critical to any organisation and allows the business to extract actionable and relevant data that can help inform security strategy and decision. Analysts will create actionable intelligence from the raw data that has been collected and processed, ready to be structured in the next phase of the lifecycle.
Data can also be placed into lists which specify Indicators of Compromise (IOCs) such as domain and IP information, file hashes, email content/addresses/links and social media content. This information can therefore be used to populate internal processes to detect and pre-emptively react to potential future incidents or used to produce alerts for any parties that may be relevant to the threats. A rule of thumb, the results should be presented in a way that aligns with the objectives and requirements specified in the first step of the lifecycle, keeping in mind the type of audience which will be consuming the results (should it be a report? or perhaps an alert for the SOC team? what about an annex or appendix?)
Don’t worry, there isn’t necessarily a “wrong” way to produce results – in fact, there is no specific way to provide results as it is case-by-case dependent.
Step 5: Dissemination
Source: RobinOlimb
This step is fairly straight forward… share the intelligence. Make sure that the intelligence is distributed to all the relevant stakeholders and departments: threat intelligence is performed to help secure others.
If an business units were involved in the planning stage of the lifecycle, it is also important to distribute the intelligence to those parties as well. Make sure that all the correct people/teams/departments etc. have the intelligence you have worked so hard to produce! You can do this by tracing when and where intelligence is shared, some organisations use ticketing systems to log requests and receipt of intelligence.
Step 6: Feedback

The final step brings us back to the start of the lifecycle, and bridges the dissemination phase back to the planning phase. The feedback phase is used to evaluate the intelligence exercise: have the intelligence requirements and objectives been met? Was the final intelligence easily consumable for all the teams involved? What actionable business decisions can be made from this? What can be improved for future intelligence exercises?
The feedback is then used to direct the planning stage, as we move through the lifecycle again…
References
- https://flare.io/learn/resources/blog/threat-intelligence-lifecycle/
- Mastering Cyber Intelligence by Jean Nestor M. Dahj, 2022
As a Developer, gathering and utilizing OSINT has become a big part of my life as well. And I also didn’t start off my technology journey with an awareness that I would end up using Open Source Intelligence in my work. But times change, and new opportunities arise. It’s up to us, as the technologists, to take the first step and open the doors we choose to walk through.
Great post. Thank you for the encouragement to study more often.
Hi Bret,
Thank you so much for your comment! We find that learning is a constant journey, and we are glad that you have enjoyed this post 🙂