Estimated difficulty: 💜🤍🤍🤍🤍
First thing’s first! Let’s talk definitions. So, what actually is risk management?
To put it simply, it is the management of the risk within an organisation (doh!). The risk management process involves identifying security risks and creating and implementing plans to mitigate them.
Defining Risk
Risk is defined as a potential event that can happen that has a negative impact to an organisation. Risk is measured by the probability of this event happening, and how severe the risk impacts business assets should the event occur – they usually exploit vulnerabilities in an organisation and are commonly seen as adverse events.
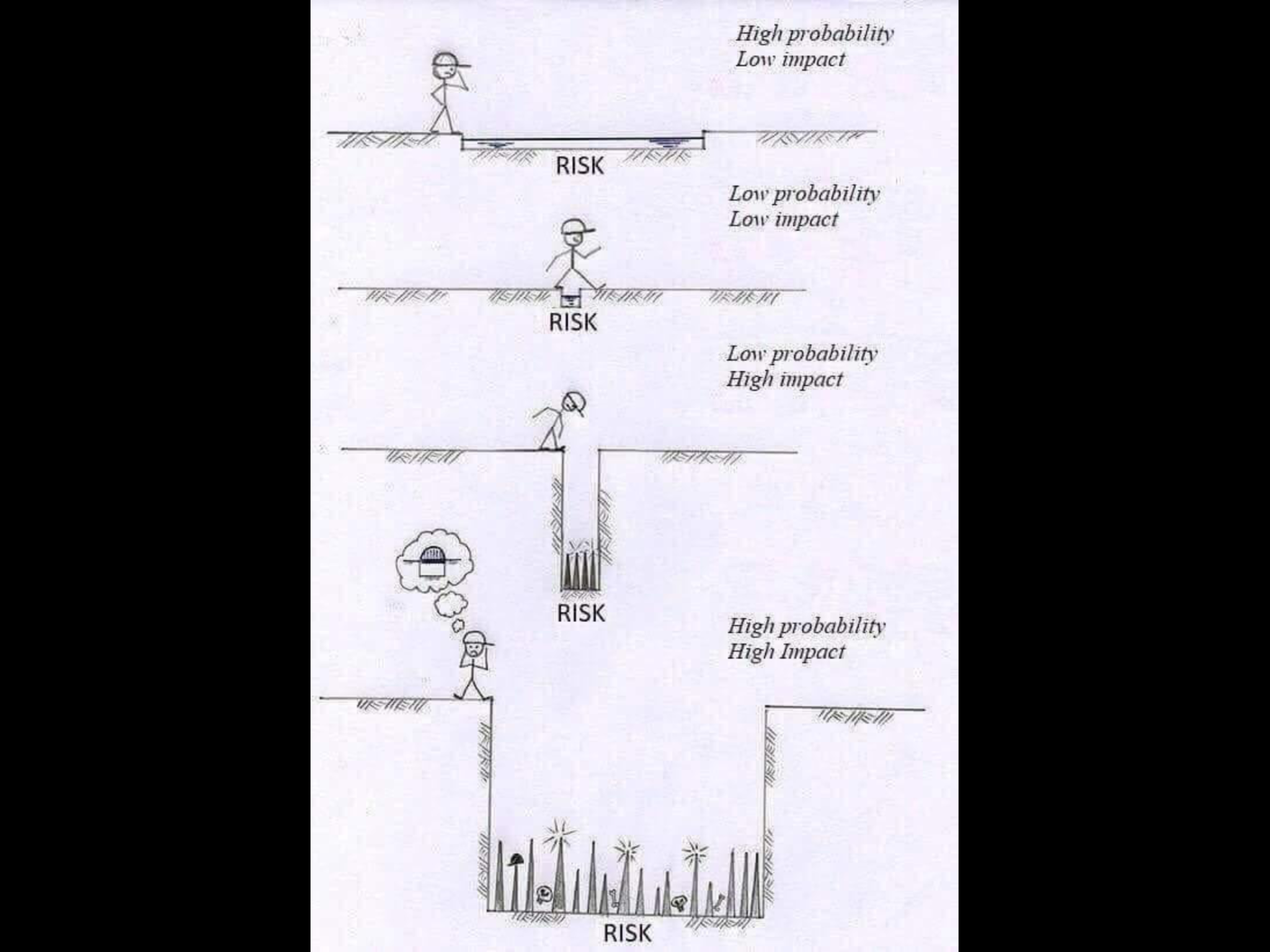
Often or not, the number of assets that are proven to be at risk in an organisation exceeds the resources that are available to help manage them. It is therefore important to mitigate risks in an efficient manner, prioritising risks that could detrimentally damage an organisation or prove critical to everyday business operations. This is done through a series of risk assessments, which help assign different priorities and levels of risks to assets and aid the decision making process in applying mitigation and implementations.
The area of “Risk Management” is made up of different components, including:
- Risk Description (what is the risk?)
- Risk Owner (who manages this risk?)
- Risk Probability (what is the likelihood of this risk happening?)
- Risk Impact (what would the impact be of the risk? e.g. financial, reputation)
- Contingency Plan (what plans do you have to recover from a disaster and/or incident relating to the risk?)
- Risk Appetite (how much risk are you willing to accept?)
- Risk Tolerance (what is the maximum amount of risk that you will accept?)
Risk & Governance; A Match Made in Heaven
Governance, another security “buzzword” that we see and use a lot in the industry. But what is it exactly? And why is it important?
TLDR; Security governance is the way that an organisation controls and manages their approach to security. This may include identifying responsibilities, co-ordinating policies and security activities and most importantly providing strategic direction to successfully obtain security goals in an organisation. If you want to know more about security governance, the NCSC has written an excellent introduction here.
That being said, it’s no wonder risk management and security governance are a “match made in heaven”. Both processes rely on each other, and both strengthen the security posture of an organisation.
Combining risk management and governance in an organisation can focus security objectives to establish a common view of risk as well as successfully integrate risk management into the business operation. This ensures that the organisation makes risk-based security decisions and are cautious to implement controls and operations correctly.
STO(P), Drop and Roll
So hopefully by this point in the post, you’re starting to grasp the mammoth task risk management is in an organisation. As aforementioned, this can be achieved by conducting risk assessments on different assets and areas in a business. One way to simplify the assessment process is to distinguish the different hierarchical levels of risk management in an organisation, this can be plotted to a “STO” triangle.
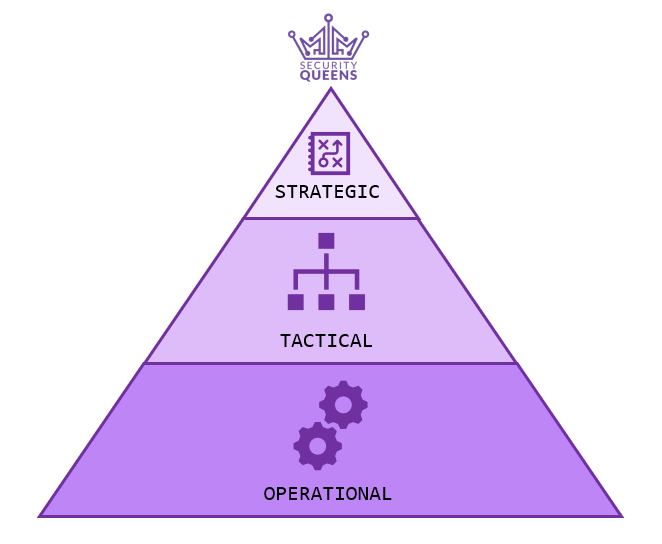
“STO” stands for Strategic, Tactical and Operational. These represent different hierarchical levels within an organisation and can be described (in a risk management context) as the following:
Strategic (Policy): High-level overview, strategy focused, resource allocation decision, definition of organisation goals as a whole.
Tactical (Procedure): Specifying activities and medium to short term objectives to achieve the strategic goal, usually a translation level between strategic and operational outlook.
Operational (Execution): Day-to-day description of decisions and processes to help execute the strategic goal, usually linking tactical processes and goals with strategic level goals.
It’s the (Risk Management) Circle of Life
Another way to simplify the risk management process is to follow the stages of the risk management lifecycle.
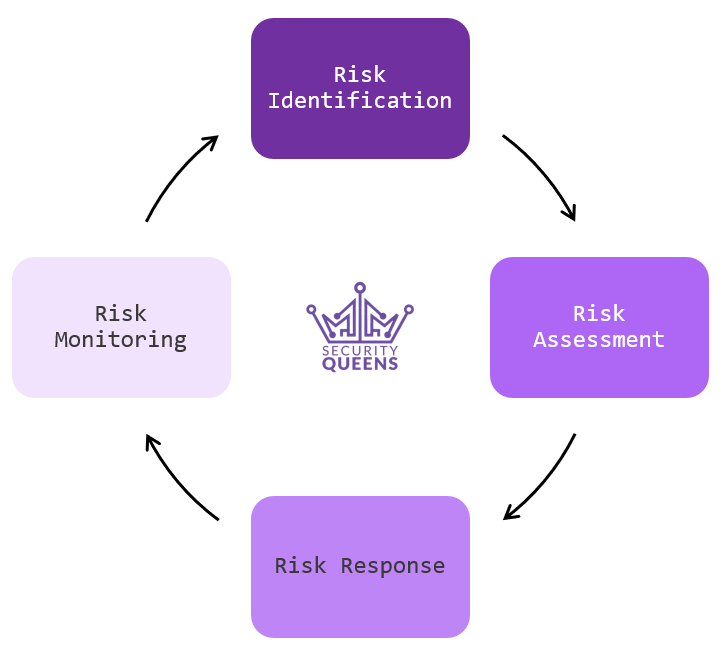
Made up of four different stages, the risk management lifecycle can help breakdown the overall process and make it easier to follow and digest. The four different stages are as follows:
Risk Identification: This stage is quite straight forward, you simply identify the risk!
Risk Assessment: In this stage, once you have identified the risk, you assess the severity and likelihood of the risk. What are the chances of this risk happening? What would the impact be? Is it worth “accepting” the risk? What resources are needed to mitigate this risk?
Risk Response: After the assessment is the response phase of the management lifecycle. In this phase you may consider implementing controls and mitigation measures to reduce the likelihood of the risk occurring. You may also draft contingency plans and recovery response in the event of a risk occurring.
Risk Monitoring: And finally, continually monitor the risk – make sure you look out for changes that may affect the risk!
Risk Management Objectives
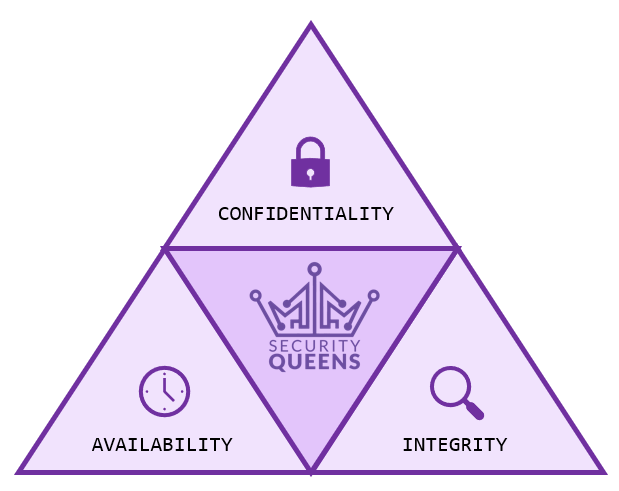
So after all this “faff”, what are the main objectives of risk management? To put it simply, it is to effectively manage your risks. These risks may derive from evolving threats, known vulnerabilities or audit and policy non-compliance. It is important when you are managing risks to protect the CIA triad (see below) and the traceability of information and data at rest, in transit and during modification.
And there we have it! A very quick, bare-bone intro into the basics of risk management. This blog was based off my Cyber Security Management module from my undergraduate degree (thank you Ed/Bournemouth Uni!), and hopefully you now have a more solid understanding of risk management basics 🙂
– Sophia x