Estimated difficulty: 💜💜💜💜🤍

So as my own personal learning journey into the land of mad hax, I thought I would document something Windows-y for a change (something completely out of my comfort zone…). This is the blog no-one necessarily asked for, but I feel would be hugely beneficial to those new to professional pentesting – especially, if like me, Windows is definitely not your forte.
The following blog will give a rundown of the attack method Kerberoasting, what it is, and how to do it. Simplez!
What is Kerberos?
So let’s start with the basics. What is Kerberos? Developed in the late 80s, Kerberos is essentially a network authentication protocol currently used as default in Microsoft Active Directory environments. Based on a client-server model, Kerberos uses symmetric key cryptography that requires a trusted third party (TTP) to facilitate and review all interactions between nodes. Kerberos has traditionally been considered as fairly secure due to the utilisation of encryption protecting passwords, keys and tickets – as well as the use of three stages of authentication.
There are three main components to Kerberos…
- Authentication Server (AS): Performs the initial authentication when a user wants to access the service
- Ticket Granting Server (TGS): Connects the user with a service server (SS)
- Kerberos Database: Stores IDs and passwords of verified users
The combination of these three components is called a Key Distribution Center (KDC) that has the authority to verify users and services within a group of systems (dubbed a realm).
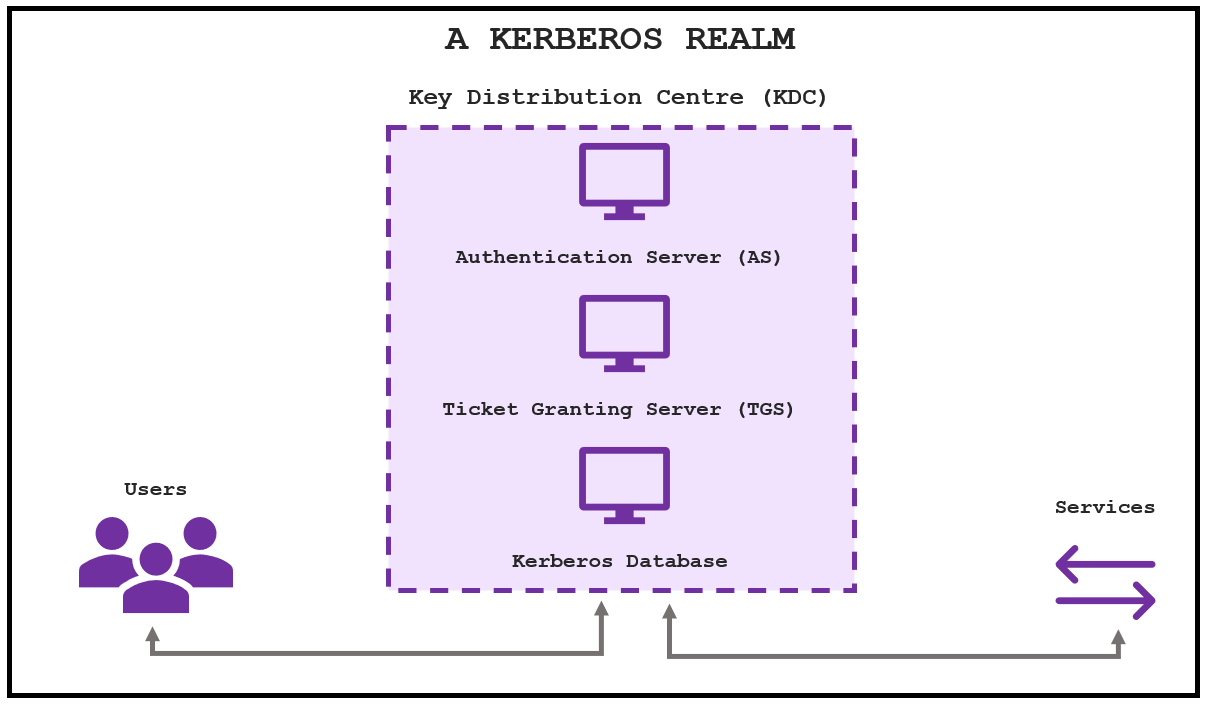
Now we know the components of Kerberos, how does it actually work? For a user to be authenticated via. Kerberos, they have to go through a collection of steps processed by the KDC
- First the user will issue an encrypted request to the AS. Upon this request, the AS will search for the user’s password based on the user’s ID. If the user supplies the correct password, the AS continues to decrypt the request.
- After successful verification, the AS will issue something called a Ticket Granting Ticket (TGT) to the user
- The TGT is encrypted by a secret key from the TGS.
- The TGT is stored until it expires, then the local session manager will request another TGT to maintain authentication
If a user is requesting a resource or access to a service on the network, these steps are then followed upon successful authentication…
- The user uses the TGT and sends it to the TGS, alongside a service request (in the form of a Service Principal Name (SPN)) for the service they wish to access. SPNs are used to identify each Windows service instance.
- The TGS is able to decrypt the ticket using the same secret key shared with the AS
- If the TGT is deemed valid and the user has been verified access, the TGS will therefore issue a service ticket and session key to the user
- The user then sends the service ticket and session key to the service, the service server decrypts the ticket by using a secret key shared with the TGS
- If the secrets keys match, the service will grant access (dependent on the expiry of the access, the user may need to go through the Kerberos process again to access the service at a later date)
Fun Fact: Kerberos was named after the Greek mythological creature Cerberus, the three-headed dog who guarded Hades and the gates of the underworld!
What is Kerberoasting?
Right, so hopefully we now all have the basic knowledge of what Kerberos is and how it works…. Now we can ask ourselves what is kerberoasting?
Kerberoasting is a post-exploitation attack that allows an authenticated normal user to obtain credentials for service accounts. This attack can be used to help achieve domain escalation and privilege escalation as you try to pwn your way to Domain Admin (DA). Service accounts are historically insecurely configured, and this attack only requires valid credentials (that can be for a low-priv user!) for the domain you are attacking and access to the KDC (which is usually the domain controller). Kerberoasting essentially exploits a flaw in the Kerberos architecture, and the assumption that user behaviour is insecure.
Kerberoasting is a fairly straight forward process which can be automated using a variety of tools. Usually, the process follows something along these lines…
- A user with an associated SPN is identified, this identifies a service logon account (an account specifically tasked with running a service)
- The compromised normal user then requests a service ticket from the TGS for the SPN identified in the first step
- The KDC automatically returns the ticket, which is encrypted using the target service logon account’s password
- This hash can be cracked offline to expose the AD user’s credentials
- You can then authenticate as the service logon account user… hacked!
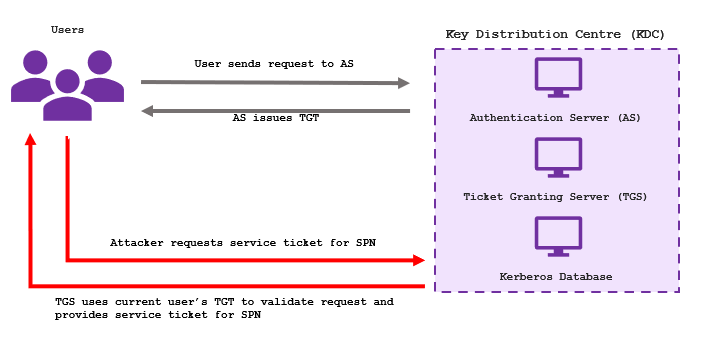
Kerberos typically uses NTLM hashes when encrypting service tickets, which usually means that weak passwords are easy to obtain. Service users tend to also have DA privileges – which is an extra bonus! Mitigations do exist for this attack, but remain difficult to implement due to how Windows domains and Kerberos works. Another great bonus for this attack, is that the network traffic generated will be deemed legitimate by the KDC.
So, How Do I Kerberoast?
There are several tools that you can use, I’ll list my go-to tools below:
Kerberoast (Python)
Find the git repository here
Pre-requisites:
Make sure you know the target domain, domain controller IP address, as well as valid credentials for a normal user. You can also use the “-t” option to specify a username list of SPNs you want to target
How to install (Linux):
pip3 install kerberoast
How to use:
kerberoast spnroast 'kerberos+pw://<TARGET_DOMAIN>\<USERNAME>:<PASSWORD>@<DC_IP_ADDRESS>' -t <SPN_USERNAME_LIST.txt>
The output from the above will give you a hash which you can crack offline.
Rubeus
Pre-requisites:
This tool must be run in a domain-joined environment. Therefore desktop access to a domain workstation (as a compromised user) is recommended. As this tool is provided uncompiled, you must also install something to compile the C# script. I recommend downloading the community version of Visual Studio which you can find here.
How to install (Windows):
- Git clone/download the Rubeus project from here.
- Double click the “Rubeus.sln” file
- In Visual Studio, click the “Start” button to compile the tool
- A compiled .exe executable should be created in Rubeus\bin\Debug
How to use:
Rubeus.exe kerberoast /outfile:<FILE>
Hashes will then be written to the specified file.
Impacket (GetUsersSPNs.py)
Pre-requisites:
Make sure you know the target domain, domain controller IP address, as well as valid credentials for a normal user.
How to install (Linux):
git clone https://github.com/SecureAuthCorp/impacket
cd impacket
python3 -m pip install .
How to use:
GetUserSPNs.py -request <DOMAIN>/<USERNAME>:<PASSWORD> -dc-ip <DC_IP_ADDRESS>
The output from the above will give you a hash which you can crack offline.
The hashes extracted using the above tools can be cracked offline using hashcat mode (-m) 13100
hashcat -m 13100 -a 0 <HASH_FILE>
Or with John using the krb5tgs format…
john --format=krb5tgs <HASH_FILE>
Once the hashes are cracked, you can now authenticate as the privilege serviced user! Enjoy your Domain Admin 😉 #domainpwned

References
- https://phoenixnap.com/blog/kerberos-authentication
- https://www.varonis.com/blog/kerberos-authentication-explained/
- https://attack.mitre.org/techniques/T1558/003/