Estimated difficulty: 💜🤍🤍🤍🤍
New year, new blog post… obviously!
To kick things of in 2023, today we’ll be talking about a commonly used social engineering technique called typo-squatting and how you can identify malicious domains/websites to protect yourself, or how to protect your organisation or brand if you own a website domain.
Typo-squatting is by no means a new technique that attackers may use, but with a sharp increase in domain spoofing attempts since the COVID-19 pandemic (with over 150,000 new COVID-19 themed domains since December 2019) – it is an important technique to be aware of.
What is typo-squatting?
Also known as URL hijacking, sting sites or fake URLs, typo-squatting is a form of social engineering which relies on users mistyping websites addresses when inputting them into a browser (the “typo” of typo-squatting). This could be down to rushed and imprecise typing, spelling errors, alternative spellings (e.g. American English v.s British English) or even using the incorrect domain ending.
Attackers or threat actors will attempt to duplicate legitimate domains for fraudulent purposes, and will register domain names similar to their target so that unknowing users end up visiting the malicious domain instead when inputting a “typo’d” website address.
There are several ways attackers may try to abuse this, and may try to use one of the following to fool users into not knowing they are visiting an illegitimate site:
- Mispelling the target site (e.g. securityyqueens.com instead of securityqueens.com)
- Using a different top-level domain (e.g. .co rather than .com)
- Adding similar words (e.g. cybersecurityqueens.com instead of securityqueens.com)
- Adding extra full-stops (e.g. security.queens.com)
- Using similar letters and characters to hide the illegitimate domain (e.g. séçurïtyqueéns.com)
Attackers may register several variations of the target site at the same time to increase their chances in success, as well as duplicate the branding, content and layouts of their target site to try deceive the user.
Typo-squatting may also be used in conjunction with phishing attacks to continue the narrative of the wider campaign.
But, why?
More often than not, attackers will use this technique to try achieve another goal or exercise another motivation.
- Extortion: Purchasing illegitamate domains to try to sell the typo domain back to the brand or organisation
- Gaining a Competitive Edge: Redirecting users to a competitor site or brand
- Advertising Revenue: Typo-domain owners may host advertisements on their sites to monetise traffic by using pop-ups or adverts
- Affiliate Links: Users are redirected to the original website, via. an affiliate link so that the attacker can earn commission from all purchases on the brand’s website
- Phishing: As mentioned above, directing users to an illegitimate site as part of a wider phishing campaign (to harvest credentials, install malware etc.)
- Malware Installation: To install malware or adware into victim’s devices
- Pranking: To cause irritation or annoyance to the target organisation by ridiculing the target organisation or brand on the typo-domain
- Activism: Using the typo-domain to host negative content about the target organisation to ruin reputation or credence (popular with political domains)
How do we stop it?
Typo-squatting itself can be tricky to prevent, as you are relying on the awareness of a user to identify illegitimate domains. Domain registries and registrars don’t necessarily have the ruling to prevent the malicious registrations of typo-domains, and often it is simple and cheap to purchase key domains that could severely impact or effect an organisation.
You can minimise the risk of falling victim to this technique by increasing awareness around the topic, such as:
- Be aware of clicking links for unexpected emails or messages to unknown websites (such as verifying the sender email address, or contacting the sender through other means, e.g. calling them, to confirm it’s legitimate)
- Ensuring that you have an up-to-date antivirus installed to detect threats and malware that may arise from illegitimate domains
- Hovering over the links before clicking to check the URL for spelling, extra characters, hyphenation etc.
- Navigate to websites using search engines and checking the results page
- Bookmarking your favourite and frequented websites (such as social media, email, banking etc.)
Protecting websites, organisations and brands
Typo-squatting can happen to any of us, organisations or brands can consider purchasing similar domains to their website and implement redirects to ensure users are accessing the correct URL. This is typically a defensive stance organisations take, even Microsoft own over a dozen domains with variations of their own name to prevent such attacks!
In 2006 even the Google domain was typo-squatted when the domain name “goggle.com” was registered to take advantage of users that mistyped when trying to visit the search engine. Goggle.com downloaded viruses and malware to the victim’s computer whilst displaying a huge amount of spam and pop-ups on the victim’s screen. The website was active from 2004 to 2007 and was renowned for downloading a virus disguised as an antivirus, SpySheriff, onto victim’s computers. The combination of all the above forced victim’s to reinstall their operating systems to regain control, which meant an instant loss of all their files and data on their computer.
If you own a website and you are worried about being “typo-squatted” you can also use the following tools to detect what variations of your domain can be created, and if they have been registered (and by which country)
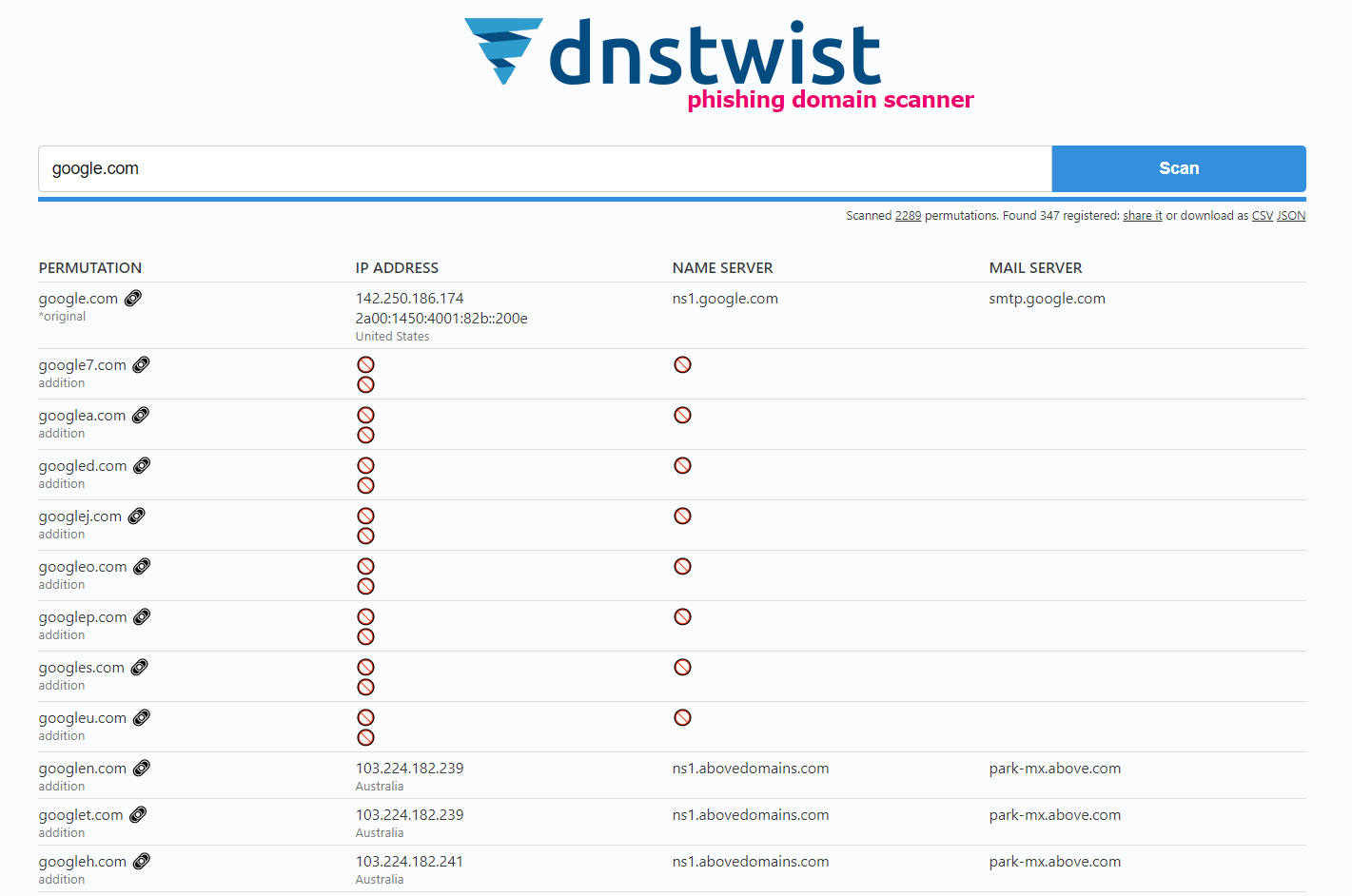
DNSTwist
DNSTwist is a website you can use that checks for typo-squat domains against a primary domain that you provide. It’s a really easy website to use, and by entering the domain you would like to check against DNSTwist provides you with a whole list of “twisted” domains and different permutations, including if they have been registered, which country they have been registered from, as well as other useful DNS information such as nameserver, mail server and IP addresses.
DNSTwist also has a command line tool that you can use that you can install in different environments (including Linux, macOS and docker). You can find more information on the command line version from the DNSTwist Github.
DNSRazzle
DNSRazzle is another tool that can be used to check for typo-squat domains and can also be installed via. Github.
Using some of DNSTwist’s functionality, the tool automates the fuzzing of typo-squat domains and provides information on registered domains (including screenshots!) as well as additional DNS information such as nameservers, mail servers and IP addresses.
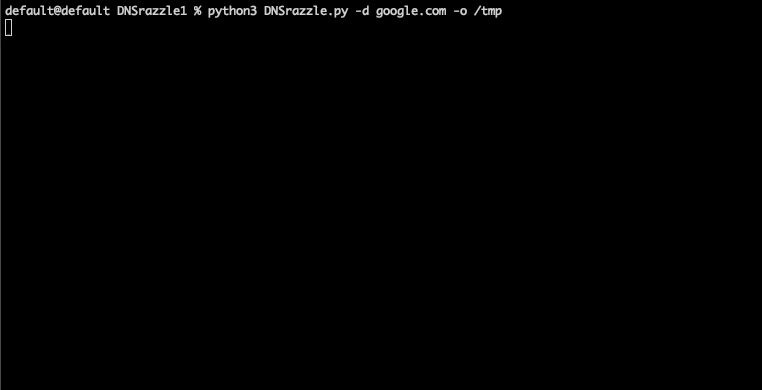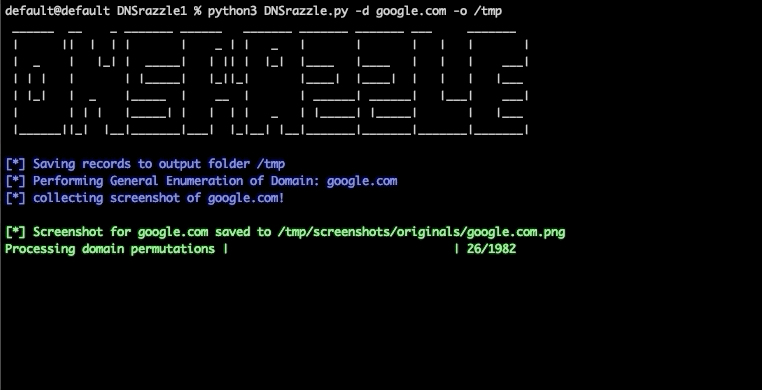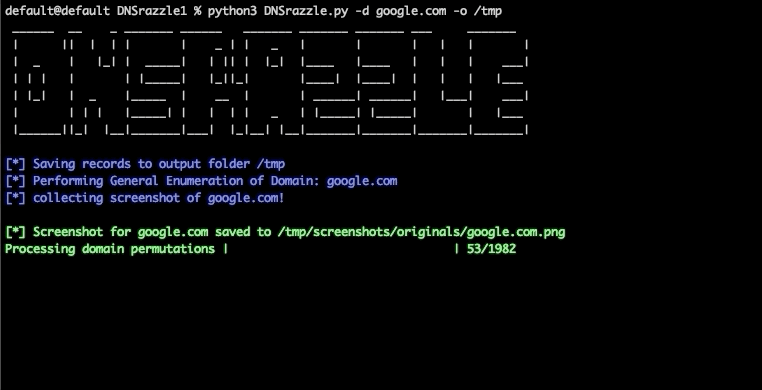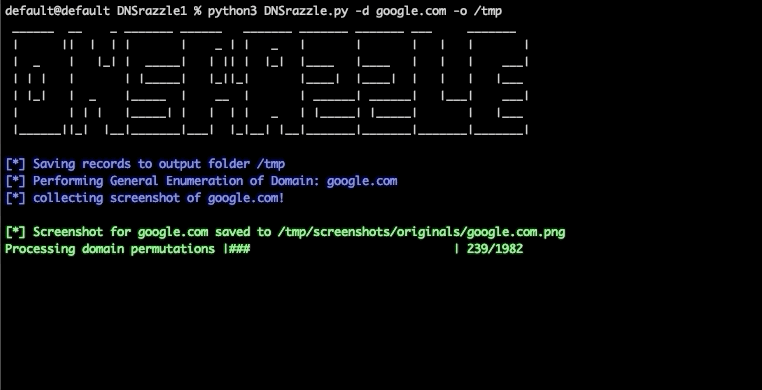
Source: DNSRazzle Github
And that’s a wrap for the first blog post of 2023! Stay vigilant and all the best for the new year…
Sophia x
References
https://www.kaspersky.com/resource-center/definitions/what-is-typosquatting
https://support.microsoft.com/en-us/topic/what-is-typosquatting-54a18872-8459-4d47-b3e3-d84d9a362eb0