Estimated difficulty: 💜💜💜🤍🤍
What is Frida? Frida is a potent tool used by reverse engineers to perform several different tasks. It is open source and once downloaded includes an extensive tool suite. These tools are:
- frida-trace
- frida-ps
- frida-discover
- frida-ls-devices
- etc
Dynamic instrumentation toolkit for developers, reverse-engineers, and security researchers.
https://frida.re/
For this post, I wanted to walk through some basic examples of how Frida can hook into Android application functions and change the logic to provide different outputs. This post will also go through how to set Frida up.
This walkthrough is being carried out with a Google Pixel 4a running Android version 13. This can work with other Android devices, however, software packages needing to be installed may vary slightly.
Prerequisites
For this post, I had a number of items ready to go. This includes:
- Frida-server software installed on my device.
- Frida-tools installed on my laptop.
- 1x Rooted Android device.
- Note, make sure the Frida software versions are the same on your device and laptop.
How to Install Frida
If this is the first time that you have played around with Frida, then we need to get that software installed! When I was installing Frida, an installation guide. The docs can sometimes be a little hard to follow, so I have broken it down into steps.
Step 1 – Installing Frida-tools
Install Frida tools on your laptop. This can be done via pip. I used the below command:
pip3 install frida-tools
Step 2 – Selecting your Frida-server software
You need to make sure that you have the frida-server installed on your rooted Android device. The frida-server software can be installed from their GitHub. Once installed on the device it will act as a daemon, exposing frida-core which opens up a connection on default localhost:27402.
When picking the frida-server software, make sure that it matches the architecture of your device. You can check this by running the below adb command:
adb shell getprop ro.product.cpu.abi
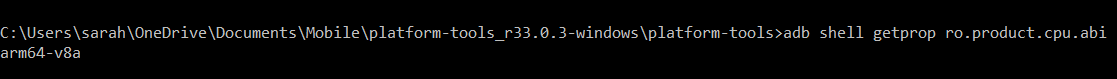
Now I know that I am running arm64-v8a, I can pick frida-server-16.0.8-android-arm64.xz.
Step 3 – Installing the Frida-server software
Once you have downloaded the correct Frida-server software, decompress the file, wherever it is saved on your laptop. From here you can find the Frida-server file inside the un-zipped folder.
Using adb (Android Debugging Bridge), push the frida-server file onto your Android device in the data/local/tmp directory. The command will look like the below:
adb push frida-server-16.0.8-android-arm64 /data/local/tmp
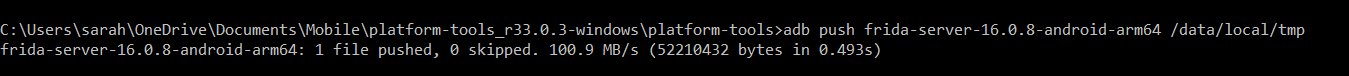
The server is not installed on your device and ready to be started!
Step 4 – Starting the Frida-Server on your Android device
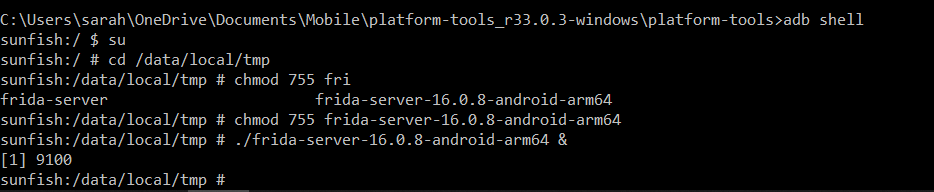
Now you have the file installed, you can start the Frida-server, so it opens up the connection and you can start hooking into your target app (we will get to that!). Using adb we want to drop into a shell:
adb shell
Since your device is rooted, and because we want to modify files and start processes, give yourself root, here we are just using the switch user (su) command:
su
Once in the root shell use the below command to switch into the directory with the Frida-server file:
cd /data/local/tmp
Before we can start the server, we need to change the modification of the file so we have permission to start it:
chmod 755 frida-server-16.0.8-android-arm64
Now we can start the server, I append an ampersand to background the process:
./frida-server-16.0.8-android-arm64 &
And there we have it, a started frida server!
Downloading your Target App
Since Frida is good to go on your device, we need to install our target app! There are a number of apps that have been developed, which can enable us to practice. However, I decided to write a basic app to help you practice your new 1337 skills for the first time. The APK can be pulled from my GitHub repo. The frida script solution can also be found there. If you want to try this on your own… Read no further! Else, please continue on…
To install the application use the below command:
adb install frida_v1.apk
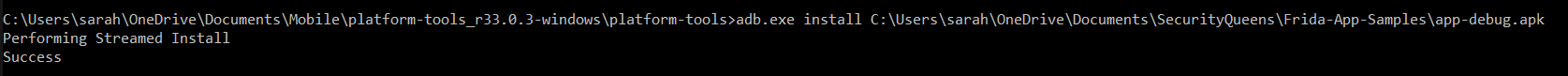
Once you see the cmd prompt says success, you have successfully installed the APK. Now we can have a play and launch the application. Note: please ignore my apk being called app-debug.apk, this was not renamed when testing.
Reviewing frida_v1.apk
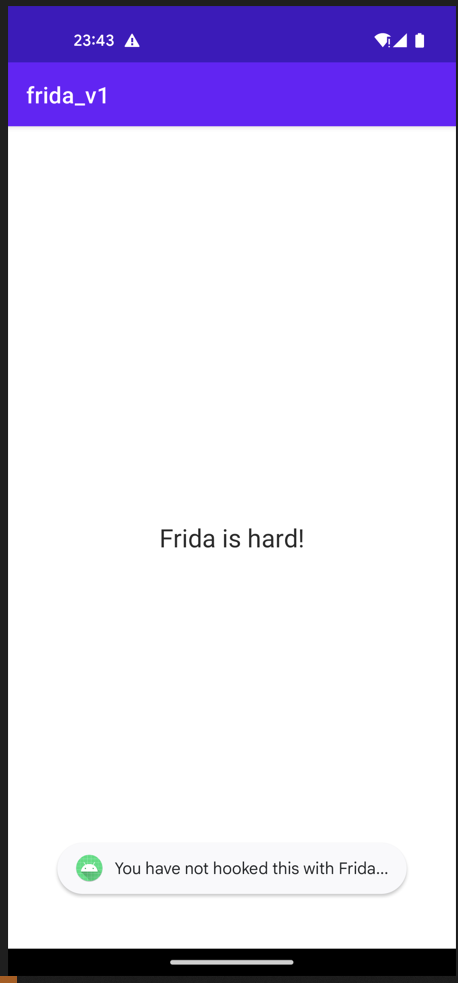
Now we have the app installed, we might as well try to run it. Immediately we are presented with a screen that states “Frida is hard!”.
We may need to check the application code to see how it is showing us that… I am using my beloved Jadx-Gui in order to decompile the APK visually. Since this screen appears on launch of the application, I wanted to find out what the Main Launcher class was for the application. To find this out, we can go to the AndroidManifest.xml file. This did not decompile correctly in Jadx-GUI, however, I have taken a screenshot of the dev environment. Normally it would look like the below image:
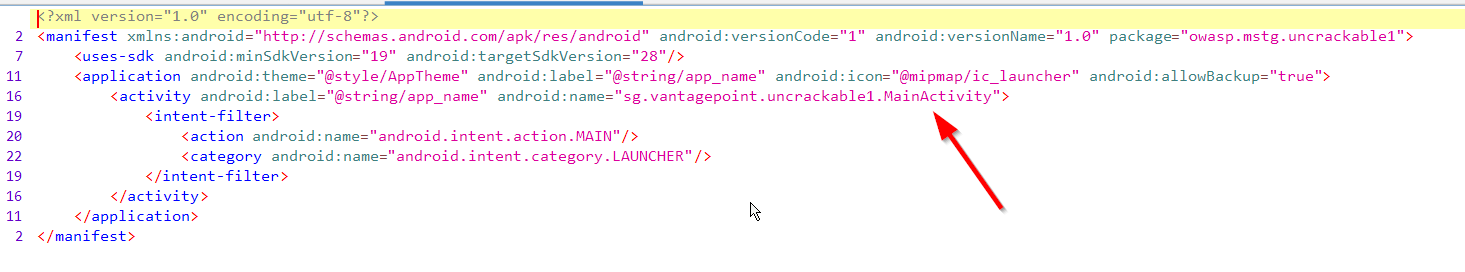
This is what the frida_v1.apk AndroidManifest.xml file looks like:
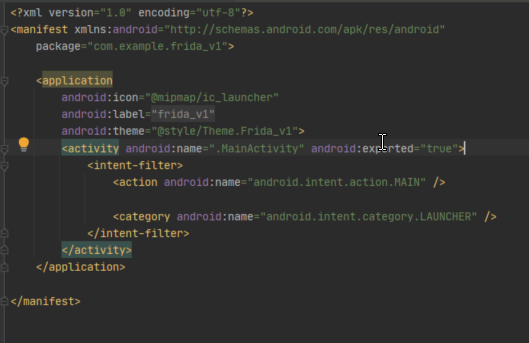
Here we can see the MainActivity class is the main launcher class, and therefore, worth taking a look at first. If the Manifest does not decompile correctly for you first time, then check the classes linked to the package name.
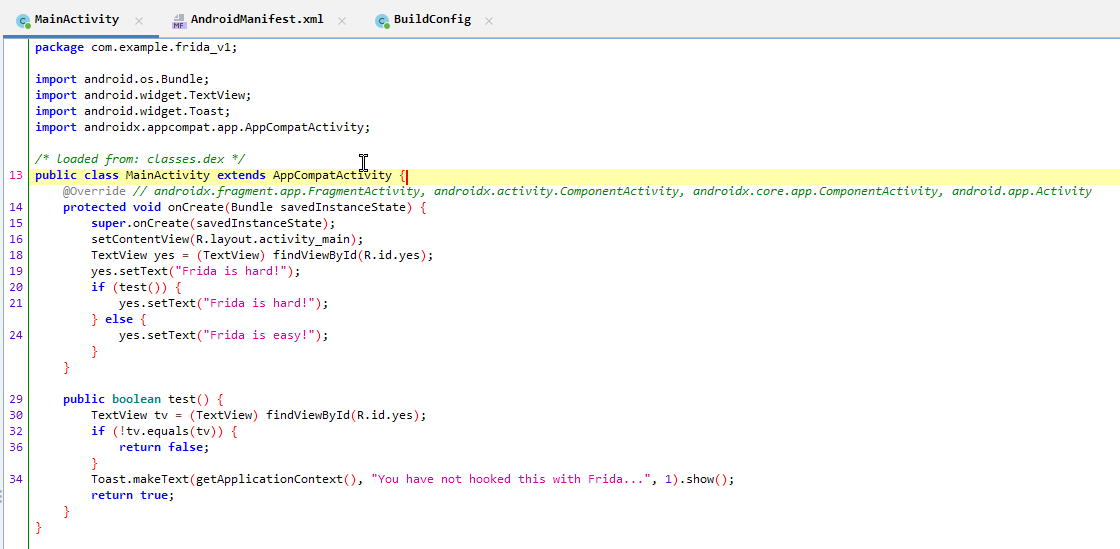
The onCreate function is the one initially called, and we can already see a couple of interesting strings “Frida is hard!” and “Frida is easy!”. The different strings are called depending on the output of the test method.
Here the code defines a TextView and sets the text to “Frida is hard!”. then the test() method is called. If the method test() is true then say Frida will always output “Frida is hard!”. So let’s check out the test() method in more detail.
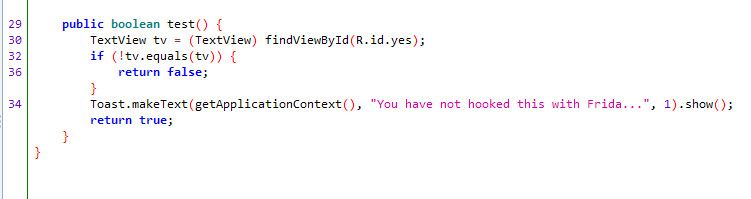
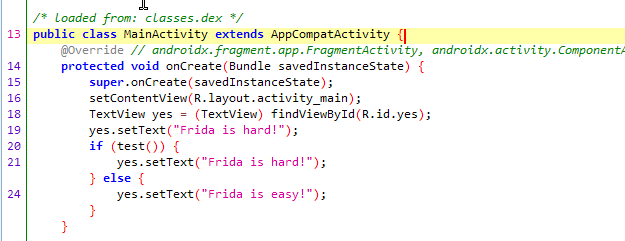
Here we can see that a TextView called “tv” has been defined, and then there is an if statement.
if (!tv.equals(tv)){
In the if statement we can see that it checks – if the TextView does not equal the TextView object then return false. In this case the TextView will always equal the TextView object, as we have not made any changes to it, so it will always return true.
Now we have a challenge!
Challenge
The challenge for this app, is to try and make set the text of the TextView, to say “Frida is easy!”. We really want to show them that Frida will not defeat us…
To do this, we need to make the test() method return false, so the contents of the else statement are triggered:

Writing our Frida Script
Now we know we need to make function test() return false we can weire a Frida script to do this! Psydo code can help us when code is a little more complicated, however, all we need to do with this Frida script, is to change the return value of test() to false. See my sample Frida script below:
console.log("Script loaded successfully ");
function test() {
console.log("Hooking");
var myClass = Java.use("com.example.frida_v1.MainActivity");
myClass.test.implementation = hooked;
}
function hooked() {
console.log("Hooked into test()...");
return false;
};
Java.perform(test);
Firstly, I created a log, so we could see in the terminal if our script was running.
Secondly I defined a function called test. This function logged another message to show we had loaded the script, defined the class we cared about – com.example.frida_v1.MainActivity – and then created an implementation of the function hooked.
The hooked() function returned the false value, so by assigning that to our implementation of the test method, we would be hooking into that function when called and then returning false to change the string.
The Java.perform(test); line, passes in the test() function to trigger this hooking behaviour. the Java.perform function is a part of Frida’s Java API, as a part of the Android Instrumentation capabilities.
When we run this script, we see the below output on the command line:
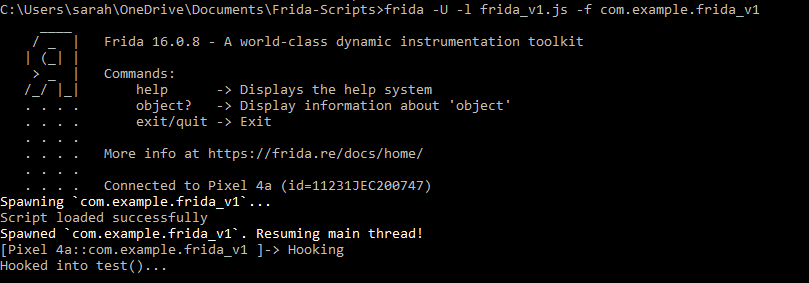
After running the below command:
frida -U -l frida_v1.js -f com.example.frida_v1
And on the screen we were presented with the “Frida is easy!” method 😀
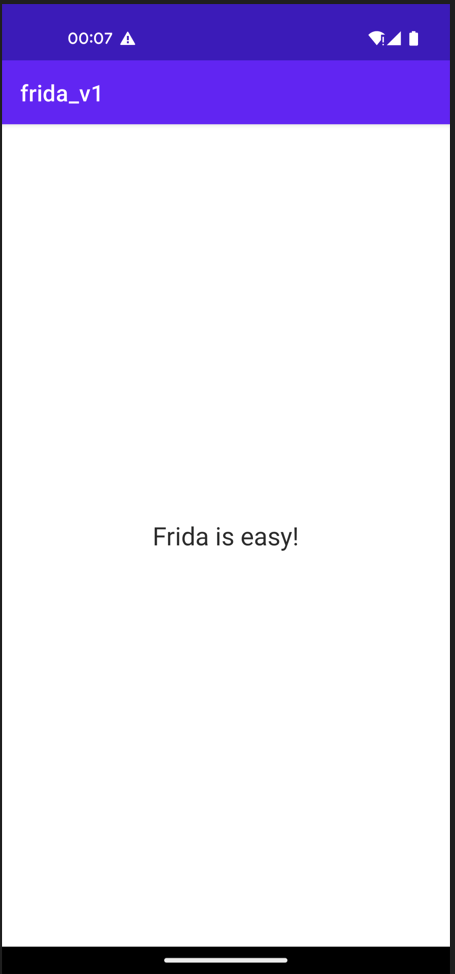
And that pretty much wraps up my first demo with Frida! There are tons of other things you can do with Frida, however, changing the logic of an Android app, is a pretty cool first start!
Thank you so much for reading this post! I am keen to learn more about this tool myself and will aim to bring you more related posts like this one. If you liked it, please let me know, and I also always welcome suggestions or improvements! And as usual, happy Fri-yay!
Sarah <3
