Estimated difficulty: 💚💚🤍
It’s a wonder what is up in those clouds, clouds can mean many different things in this day and age. Clouds live in the sky, there is something called cloud computing and more importantly, (for this article) clouds can represent the internet – especially in a network diagram! But what actually is the internet, how does it work and is there really a castle up in the clouds? This post is going to talk about what the internet is, what the world wide web is and how we can protect ourselves as a part of this network.
What is the internet?
You like many other humans are connected to the internet through your mobile phone, laptop, desktop, tablet, smartwatch and so many different devices! The internet is a gigantic web of computers and devices connected together. For this post, I am going to refer to these devices as computers.
A “large system of connected computers around the world that allows people to share information and communicate with each other“.
Cambridge Dictionary
The main idea behind the internet was for one computer to be able to communicate with another computer. Originally called ARPANET the first recorded communication between two computers was in 1969. Academic researchers wanted to connect these computers so they could share research and other similar documents. Since then, the internet has evolved into what we know it to be like now. However, I am sure a handful of us still hear the war stories of websites taking minutes to load, or worse yet, life without a computer!
Protocols
Computers use something called protocols to communicate with each other. A protocol is a defined way of how these computers should “talk” to one another. The Transmission Control Protocol/ Internet Protocol (TCP/IP) protocol suite was created at the early development of the internet. Protocols have been added to this suite as years have gone by and as the functionality of the internet has changed. To explain this, let’s have a look at what protocols might be involved in you sending a message to your friend next door. This shows the communication at a high level.
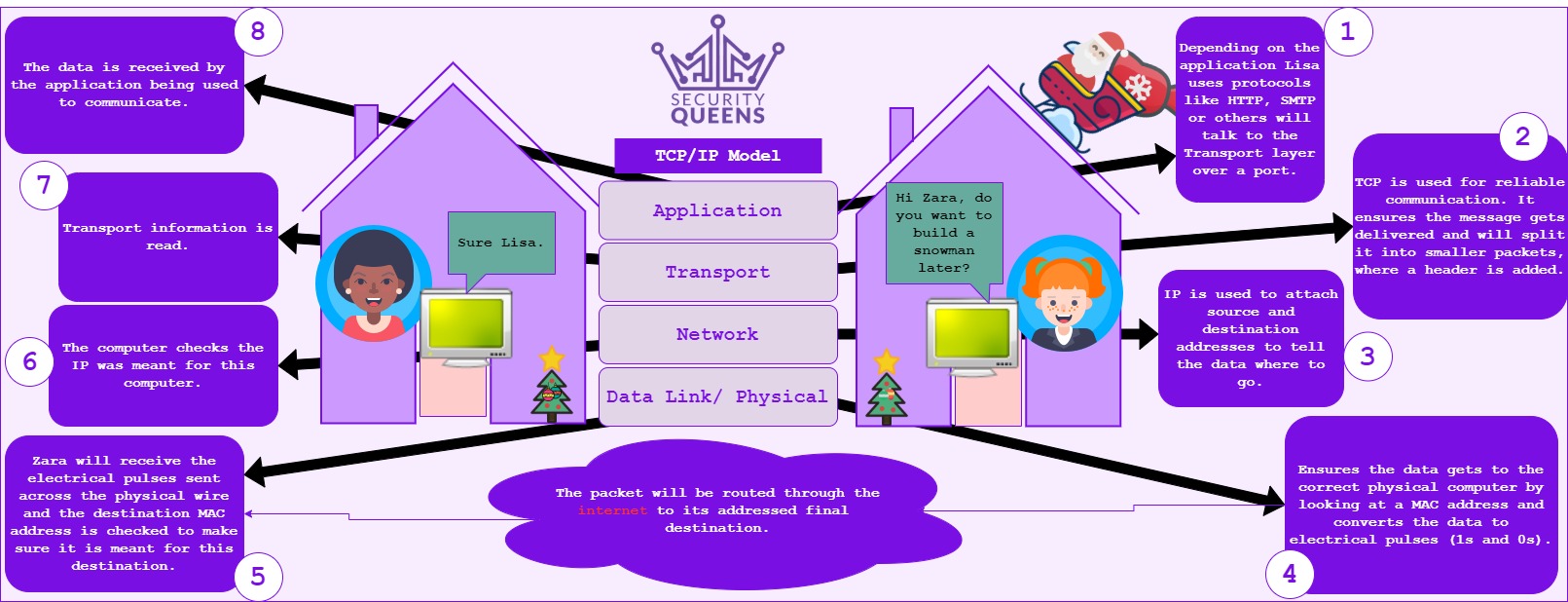
Tech Quickie on YouTube explains TCP/IP well. The message is sent from Lisa’s machine, that data is encapsulated as it goes top-down each layer of the TCP/IP model and then when Zara receives the message the data is decapsulated and going bottom-up each layer of the TCP/IP model.
How do we use the internet?

We can use the internet for many different types of things. Communicating with each other like we talked about earlier; social media, watching videos and learning things! You are using the internet to learn something by reading this blog post right now! But what actually happens when we visit a website like this blog?
URL
First things first we open up our browsers and navigate to something called a URL. Our browser is an application that is used to retrieve and display content from a website. A URL – standing for Uniform Resource Locator – is the address for that website you want to go to. Your computer needs to find the IP of this URL so it knows where to send your request to access the website. The URL is separated by a “.” (full stop) to break the URL down into different sections.
https://securityqueens.co.uk
.uk – This is a country code Top Level Domain (ccTLD). Other TLD’s may look like: .com, .org and .net, but really there are many different TLD’s and ccTLD’s out there. This signifies that a domain is from a particular place.
.co. – This is a second-level domain of the ccTLD. You might often see .co.uk or even .gov.uk. .co.uk normally means that the website you are going to a commercial UK website and .gov.uk can mean you are navigating to a government UK website.
securityqueens – This is the domain name. You can buy your own domain to set up your own website if you really wanted to! You can purchase a domain through a registrar who will manage different domain names that have been registered.
https:// – HyperText Transfer Protocol Secure. It encrypts and handles the transmission of web pages. There are other protocols for different things.
The entire URL / address is unique to the website you want to visit. Top tip: Sometimes malicious websites will try to look like the URL you want to visit, but often have a typo in it to trick you into trusting their site. Look out for these mistakes to avoid going on a potentially dangerous website.
How does it work?
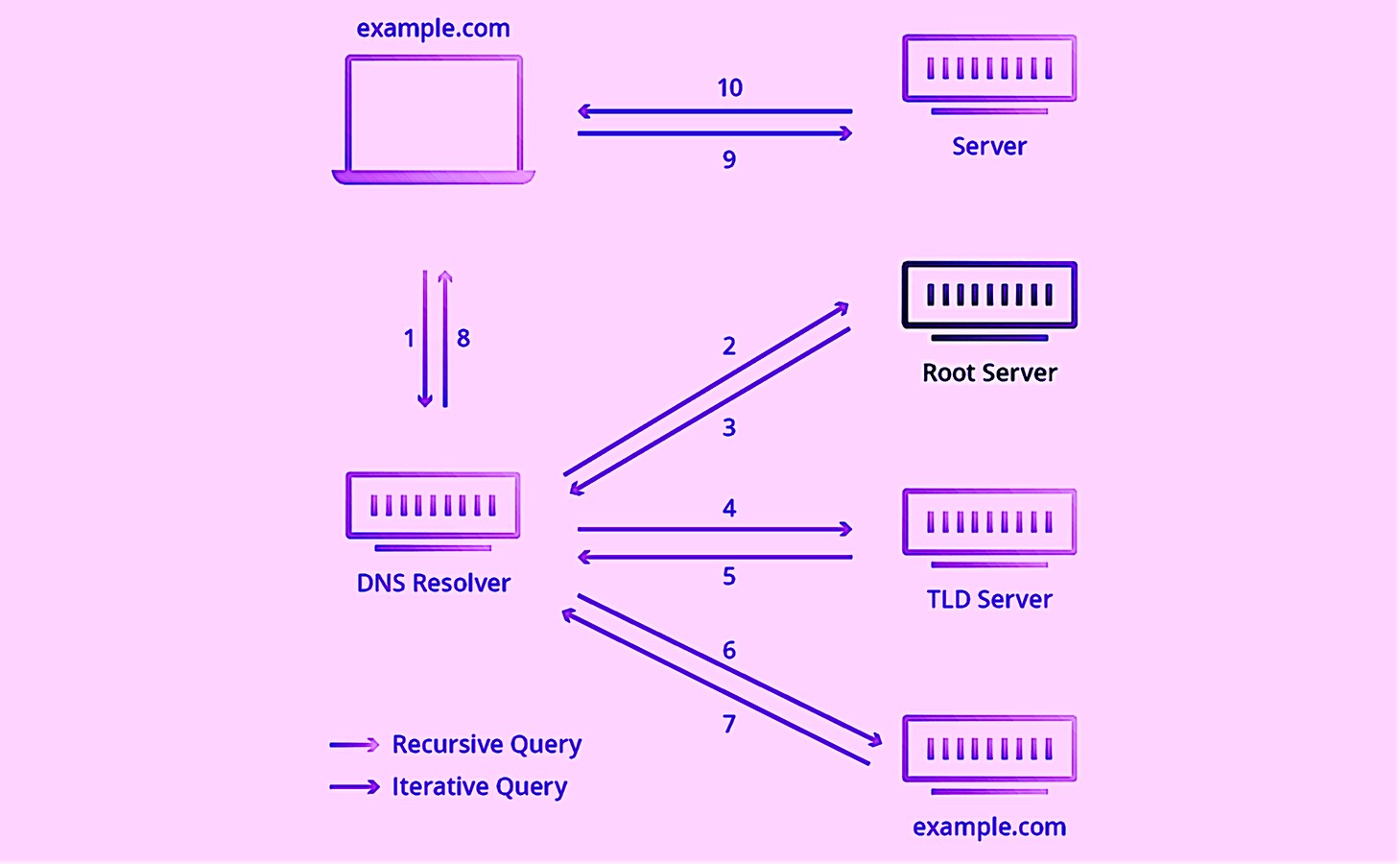
To put it into words, you will enter in the address https://securityqueens.co.ul into your browsers URL address bar. That request if not found already in the cache of a router, will be routed to a root name server, this server will look at the URL and depending on the TLD send it to the appropriate TLD server. In our case, another request would be sent to a ccTLD name server for .co.uk domains. A third request is sent to the authoritative name server which should contain the record of the correct IP for our URL.
World Wide Web
The world wide web is a crucial part of the internet. Instead of connecting physical computers, the world wide web connects information. Documents and different types of information are identified by URLs (like we mentioned earlier) and these URLs can be embedded or linked through a hyperlink in these web resources like a document or web page. You can see an example of this in this very blog post. I have added hyperlinks to this page to allow you to click the link and check out another webpage to read more on the topic or know my source for this information.
Game On!
So now we know more about the internet and the world wide web, let’s test the theory! When I was younger in our ICT lessons we used to play a game. This game involved a friend and I racing get from one webpage to another in the shortest time. In Wikipedia, many of the pages are linked through hyperlinks, what we learnt about earlier. The rules were you had to go from one Wikipedia page to another agreed Wikipedia page by only clicking on hyperlinks within your starting Wikipedia webpage. Try it yourself or with your mates (albeit when we are allowed to see friends again).
- Try going from the Wikipedia page Internet to the Wikipedia page Phishing, by only clicking the hyperlinks within the page.
My answer:
- You can click on the links in the following order:
- Internet
- Blogging
- Hackers
- Exploit
- Vulnerabilities
- Social Engineering
- Phishing
Leave a comment below if you managed to get from Internet to Phishing in fewer clicks!
How to surf safely
There are many different things we can do to make sure that we are safe when we are searching the web. I have created a checklist of things to look out for to make sure you are safe when surfing the web and when you are connected to the internet.
| Danger | How to stay safe |
|---|---|
| Un-encrypted website | You can tell when your data is being transmitted over plaintext when the website is not using encryption. Check to see if there is a padlock on the left-hand side of the URL or make sure the website is using the HTTPS protocol to ensure this is being used. |
| Spoofed website | As explained earlier, sometimes an attacker might create a website with a similar URL to a legitimate website. Look out for spelling mistakes, or “.” (full stops) separating the domain names in the wrong places. |
| Hyperlinks | Check what website you might be going to by either hovering over the link (if on a computer) or holding down the hyperlink (if on a mobile device). If you don’t trust the link then don’t click it. Sometimes you can check to see if a website is safe by analysing it through sites like VirusTotal. |
| Personal Information and sensitive data | Don’t submit any sensitive information about yourself to a website that you don’t trust. Make sure that if you do submit sensitive information that the website is using encryption, to further protect your data. |
| Scams | It is more common than ever to shop online and there are millions of shopping sites to choose from. Make sure that when you purchase something off a website that you once again trust the website. You wouldn’t want to buy something and never have it turn up! |
From my computer to your computer, I hope you have enjoyed reading this post and do let us know what you think!
Sarah <3

What is the internet, how does it work, and what is the relationship between the internet and the world wide web? Additionally, how can individuals protect themselves while being part of this interconnected network?
Hi! Thanks for your comment. To address your points, I will break each one down as best I can:
* What is the internet?
The Internet started out as a way of files to be shared. The education sector was the first to utilise the Internet. It was defined as the Internet, as it standardised the way that computers were able to “speak” to each other. Bring in the Transmission Control Protocol (TCP) over Internet Protocol (IP). IP are addresses all internet connected devices have, like how you would have a unique address on your street and it tells another computer where to send the message. The TCP Protocol operates on the Transport layer of the OSI Model (worth Googling) and helps with reliably sending the data to its destination IP/target computer.
* What is the relationship between the Internet and the World Wide Web?
Your browse lets you visit websites, and these websites are hosted on a computer/server. The World Wide Web connects these websites together using the Internet. For example, you are accessing our website right now, which is hosted on a server, and our website is public to you. The fact that you can access these resources on our server encompasses the meaning of the world wide web. Furthermore, we have external links in this blog alone, that when clicked will take you to another server hosted by someone else that could exist all the way over in the US for example, so the world wide web is a web of computers all over the world that are able to present information and data to you.
* How can individuals protect themselves while being part of this interconnected network?
When you are online and browsing websites, you make use of a browser. This could be Chrome, Edge, Firefox, etc. Make sure that you are using a trusted browser and visiting websites that you know to be legitimate. Browsers have their own built in filtering lists, so I would say it is safe to assume that some of the most popular browsers will implement a decent check on sites such as phishing. If however you are not sure, check that the URL you are visiting is correct and not misspelt as that could be a fake website and lead to your data being stolen. You can also enable the AdBlock plugins in your browser to prevent annoying adverts or harmful links loading on your website. All in all, I would advise not to click links you don’t trust or expect, including ads that pop up, no matter how tempting.
I hope this helps!
Castle is good as internet