Estimated difficulty: 💜🤍🤍🤍🤍
This post is in collaboration with the infamous OSINT (Open Source INTelligence) hacker @thecyberviking. “Google knows everything… – Part 1” is but one post in a series of OSINT related topics created with the help of that spooky dude! This post on Google Dorking will focus on the use of queries to find sensitive information within files. Later posts will go in depth about the use of Google Dorking for things, such as finding live cameras, vulnerable servers and footholds. These posts only cover a tiny amount of what you can otherwise do with Google Dorking so it will be up to you to explore! However, please feel free to contact me or post your questions if you would like to know anything.
** With some of these techniques you may find sensitive information… Make sure you stay compliant with the law. It is important you do not attempt to authenticate yourself with discovered credentials or misuse this information. **
Google Dorking
Google Dorking is a means of searching through Google’s search engine in a very specific way… there are certain commands that can be used to help us find what is hidden or un-obvious in the depths of this browser. There is a Google Hacking Database treasure trove you can use to help with getting to know how to dork, but I have listed my favourite searches when trying to find information.
Useful commands
| Google Operator | Effect |
| site: | Using the search term “site:”, you are searching for all indexed URLs related to the domain you are listing. For example, “site:securityqueens.co.uk” will bring up all results for securityqueens.co.uk. |
| intext: | “intext:” is used to search for specific keywords in the content of web pages. This is useful to use in conjunction with the “site:” command. For example, “site:securityqueens.co.uk intext:Digispark” searches the Securityqueens.co.uk website for all pages mentioning the word Digispark. |
| inurl: | Similar to when you use “site:” to find all URLs indexed with the specified domain, “inurl:” searches for all URLs indexed containing the specific search term. For example, “inurl:admin“, will search all URLs containing the word admin. |
| filetype: | “filetype:” is used in conjunction with keywords to bring up specific files on the internet. For example “admin password filetype:log” searches for web pages including the key words admin and password that is a log file. |
| intitle: | It will ask Google to show pages that have this term in their html title. |
| cache: | This will show you each cached version of any website. For example “cache:securityqueens.co.uk“ |
| * | This acts as a wildcard. For example, “How to *” will bring up all the “How to” sites. |
Further techniques and commands have been discussed on the Security Trails blog.
Authentication, Authorisation and Accounts
When it comes to building up your password lists for projects or reasons we probably do not want to know about, there are stand out sites that you can scrape such credentials from. These include: pastebin.com, trello.com, github.com.
Alternatively we can specify specific file types to search for credentials in other places, such as log and configuration files. Leaked account information is also sensitive data people may want to look out for to signify security flaws in systems, as well as API keys!
Pastebin.com, Trello.com and Bonus!
Pastebin is commonly used to share credentials. Anonymous users are able to paste lists of credentials on the site with an expiry date of Never! The below query used in Google helps us to find such information.
Pastebin – Credentials
Insite:pastebin.com “password” “username”
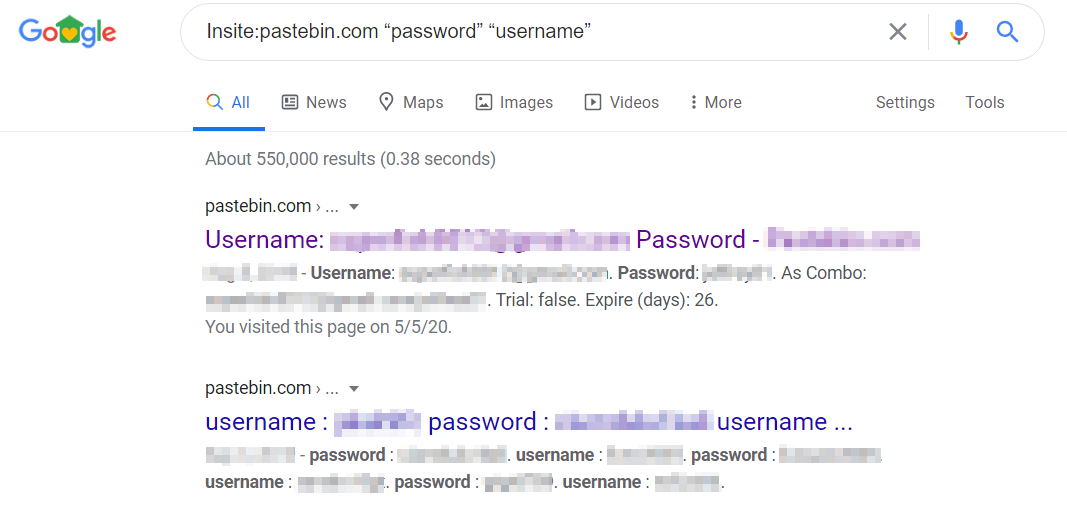
Even such simple search terms can lead to you finding your first set of credentials! You can modify the search terms to include your username, allowing you to check if your creds have been leaked or take usernames and passwords from the results to build your own word-lists.
Trello – Account Information
site:trello.com insite:paypal password
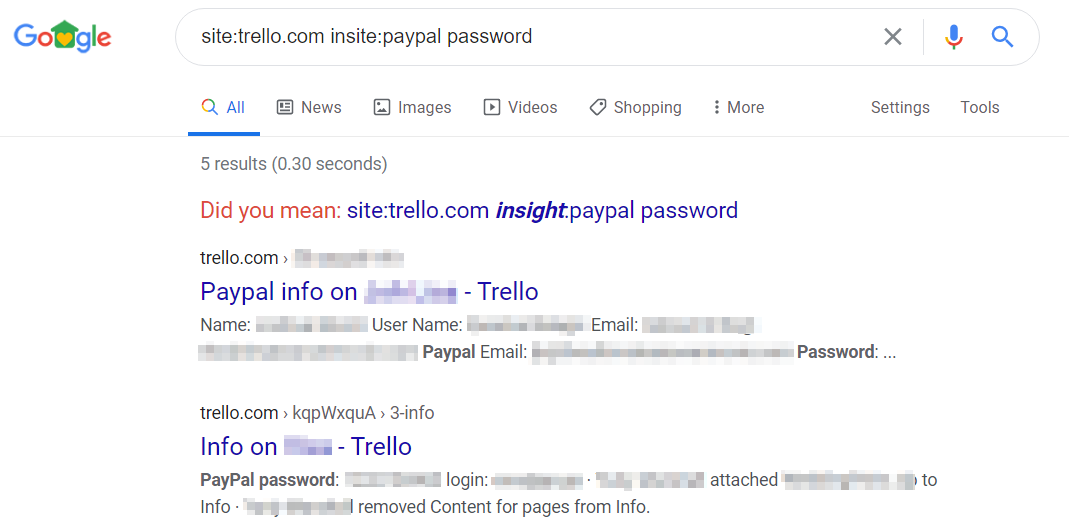
This example, provided by the lovely fellow queen Sophia, specifically searches the website “trello.com” for any webpage with the content or words “paypal password” included. By changing the keyword we can search for other content like credentials, bank account information and other information you may be interested in finding.
Cevisozluk – Fun Extra (Bonus)
"cevirsozluk.com" CVV number

This website has historical translations from Google Translate. By searching with a given query we can see contents of a translated email stored on this website, in some cases people may be sending banking information across which can be seen in the image. The search term listed, helps us find such banking information. I will let your mind wonder what these can be used for. Medium wrote more on this, so if you are interested please see their blog!
Github
On the odd occasion, developers will leave sensitive information in repositories or builds. Github can be searched to find such leaked information. These queries are not used as a Google Dork, but searched from within the Github website in the search bar. The queries contain similarities to a Google Dork, where you can use quotations to specify key words in your searches.
Github – Api key search
"API Key"
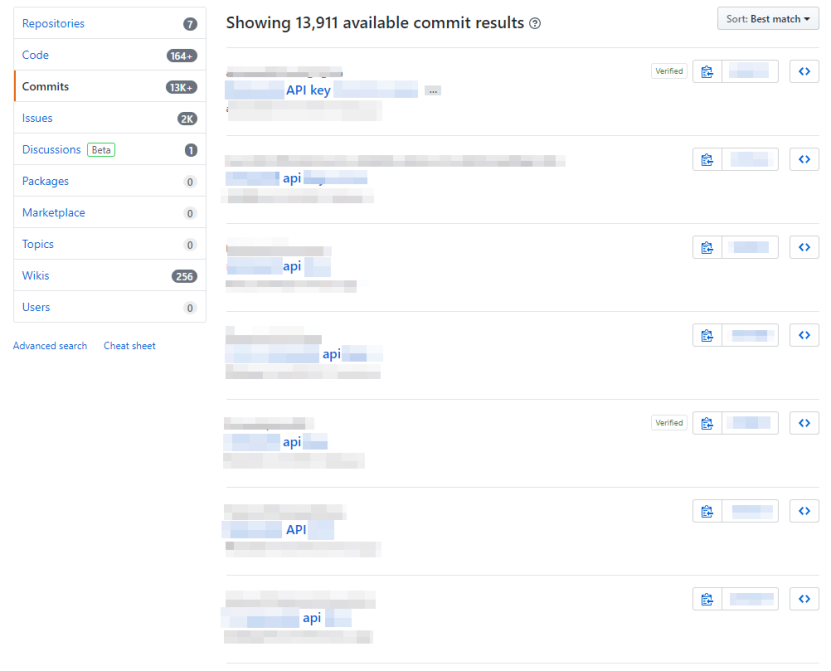
Results from the above search term show a list of potentially leaked API keys from public repos in GitHub. Github keeps all changes made to files even after they are deleted. Leaked API keys may provide unintended people access to an organisations services or authentication to servers.
Github – Credentials
"removed password"

When you are looking through changes made to Git repositories you are able to see what has been added and removed based on the colour. Green = added and is currently there, Red = removed what was there. This may lead you to see updated credentials or passwords that were previously used, similar to what you will find when using this search term.
Example 3 – Filetypes
Alternative methods of finding sensitive information can be used by searching through leaked or available configuration files.
Log and Config Files – Credentials
password ext:cfg OR ext:log -git
This query searched for a “cfg” file, with the contents containging a comment with the word password after it “x password”. Passwords are stored in many types of forms, they can be commented into configuration files and source code. It is worth taking some time to understand what sort of files you want to pull information on and the ways in which passwords are stored within them. Please see the useful commands section on how to build your own queries.
Protections
- When registering to a platform; ensure you have adjusted the security and privacy settings to a level you feel comfortable. For example, make sure your repo on GitHub is private before sharing sensitive information.
- Double check you are allowed to share the information that you are posting.
- Never share Account Details on the internet.