Estimated difficulty: 💜💜💜💜💜
For the folks that follow me on Twitter, you may remember me exclaiming for help a few months back for information on the security within the aviation industry for my Information Assurance (IA) assignment. Firstly, a huge thank you to everyone that reached out – applying professional knowledge to my research resulted in an excellent 87/100! I really enjoyed looking into the security challenges within aviation, and following the hours (and hours, and HOURS) of work I put into that assignment – it only seems right to write a follow-up blog on it.
The following blog will be analysing the security posture of the aviation industry from a high-level, information assurance perspective – looking into the following factors within aviation: external factor analyses (PESTLE + SWOT), risk assessment, mitigation plans and business continuity plan speculation. This will provide the “tip of the iceberg” of security challenges within aviation, to give context – we were supposed to include the above all on an A1 poster! Ergo, the analyses may be a little on the compressed side.
As part of the assignment, we were to chose a “case study” from one of the following hospitality sectors to analyse from an IA perspective: Accommodation and Lodging, Food and Beverage or Travel and Tourism. I wanted to challenge myself, and following my interests on automotive hacking – decided to proceed looking into another transportation sector, aviation, as my case study sub-sector.
We haven’t had an embedded song-blog in a while – and since IA can be quite dry for some folks, in an attempt to keep y’all engaged I’ll embed a few “aviation” songs throughout the blog for that perfect background music.
TLDR; An Intro to Travel & Tourism (+ Aviation)
Travel and tourism are an integral part of the modern-day hospitality industry. Components of this industry range from transport, such as the use of aviation or coach travel, to “all-inclusive” package holiday deals. The combination of these components produces masses of personally identifiable information and sensitive consumer data. With the implementation of the General Data Protection Act in 2018, this data must be protected and processed correctly to remain in line with regulations and laws and to preserve the confidentiality, integrity and availability of this information to both customers and businesses alike.
Alternative to customer information assets, the travel and tourism sector also has the opportunity for more drastic attacks on information assurance which inflicts damage more business oriented rather than customer centric. Attack on enterprise data, such as plans for business strategy or confidential trade information, can affect the market forces within the sector and fluctuate competitive advantage between competing brands.
Particular to hospitality, the industry also processes payment information and data from customers when purchases are made for holidays and services. This may force PCI DSS (Payment Card Industry Data Security Standard) upon relevant companies that use such services and provides a further asset to protect in terms of information assurance.
Linking these different types of informational assets provides a large attack surface for malicious actors to compromise. It is important to assess the risk specific to each asset within travel and tourism and adjust risk management techniques accordingly to ensure that this sector is adequately protected against cybercrime against information and data.
Keeping up so far? To help understand the area of travel and tourism I created this rich picture to visualise the different assets within the industry, including information assets and relevant informational regulations and legislation.
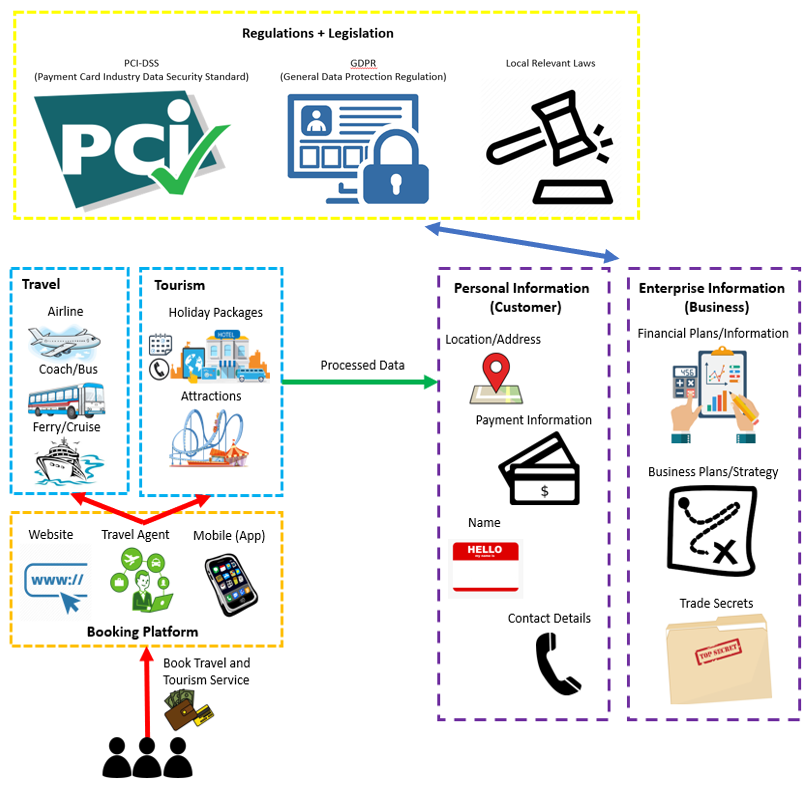
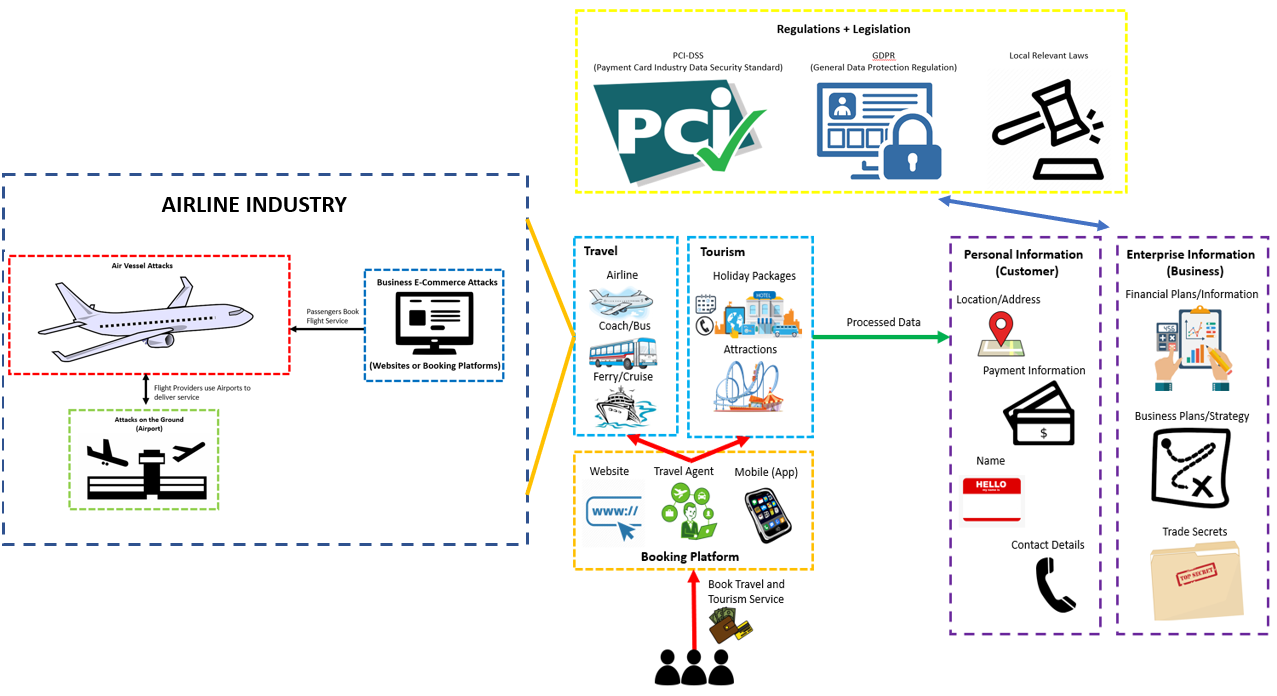
Now understanding the components of travel and tourism, it was important to analyse the different assets with aviation. The more I researched aviation, and the more feedback I received from seasoned aviation security experts – I soon realised that the aviation and airline industry was a complex industry made-up of a plethora of different components, systems and assets.
For the purpose of the assignment I divided the industry into three main areas vulnerable to attacks. These areas were identified to be of most importance, with the greatest risk and consequence should they be attacked: Air Vessel, E-Commerce and “On the Ground”.
Using our original rich picture, we can then attach the aviation industry to complete the “bigger picture” of travel and tourism – with a focus on airline.
SWOT’s Up, Doc?
It wouldn’t be a “Sophia” blog without at least one pun right? And this terrible pun is the start of our IA analysis on aviation and airline – completing PESTLE and SWOT analyses to identify external factors that may affect security-relevant issues within the sector.
What is PESTLE?
A PESTLE analysis is commonly used as part of business analysis, developed to map the external environment of a business. The PESTLE acronym represents Political, Economical, Social, Technological, Legal and Environmental – denoting a variety of factors that can affect the operation of a business. Although primarily a business tool, PESTLE analyses can be applied to achieve high-level security awareness by analysing factors that may create security challenges to a business and/or industry. PESTLE analyses go hand-in-hand with a SWOT analysis, which examines the factors in further detail.
What is SWOT?
Similar to PESTLE, SWOT analyses are typically used as a business analysis tool. A SWOT analysis will help identify the Strengths, Weaknesses, Opportunities and Threats to a business and/or sector. Using a SWOT analysis from an IA perspective can help identify the “SWOT” factors that are relevant to security aspects.
PESTLE Analysis
A PESTLE analysis helped identify factors to aviation that may impact security within aviation:
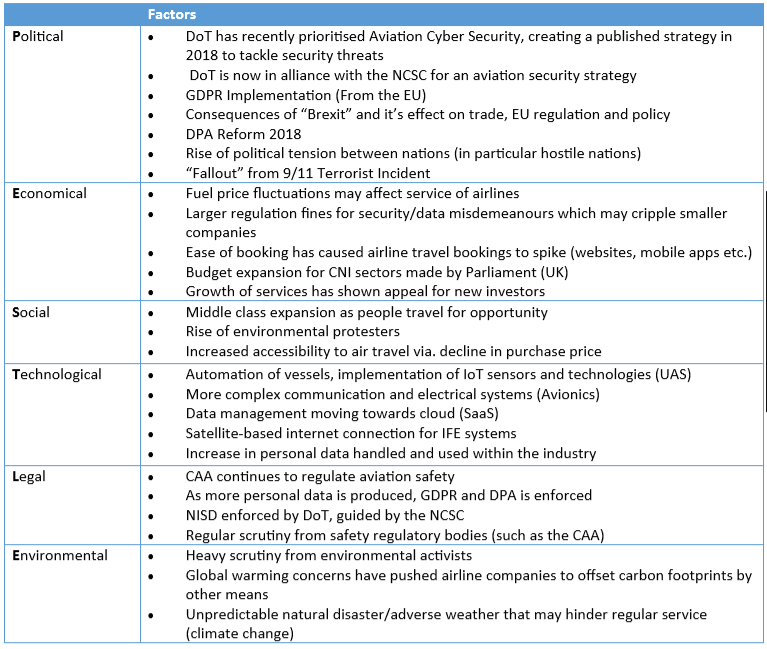
Glossary
- CAA = Civil Aviation Authority
- DoT = Department of Transport
- UAS = Unmanned Aerial Systems
- IoT = Internet of Things
- NCSC = National Cyber Security Centre
- GDPR = General Data Protection Regulation
- EU = European Union
- CNI = Critical National Infrastructure
- DPA = Data Protection Act
- SaaS = Software as a Service
- IFE = In-Flight Entertainment
- ICO = Information Commissioner’s Office
- NISD = Network Information Systems Directive
SWOT Analysis
A SWOT analysis was then completed, linking the “SWOT” factors to the previously identified PESTLE factors. This was represented by bracketed acronyms (P = Political, Ec. = Economical, S = Social, T = Technological, L = Legal, En. = Environmental).
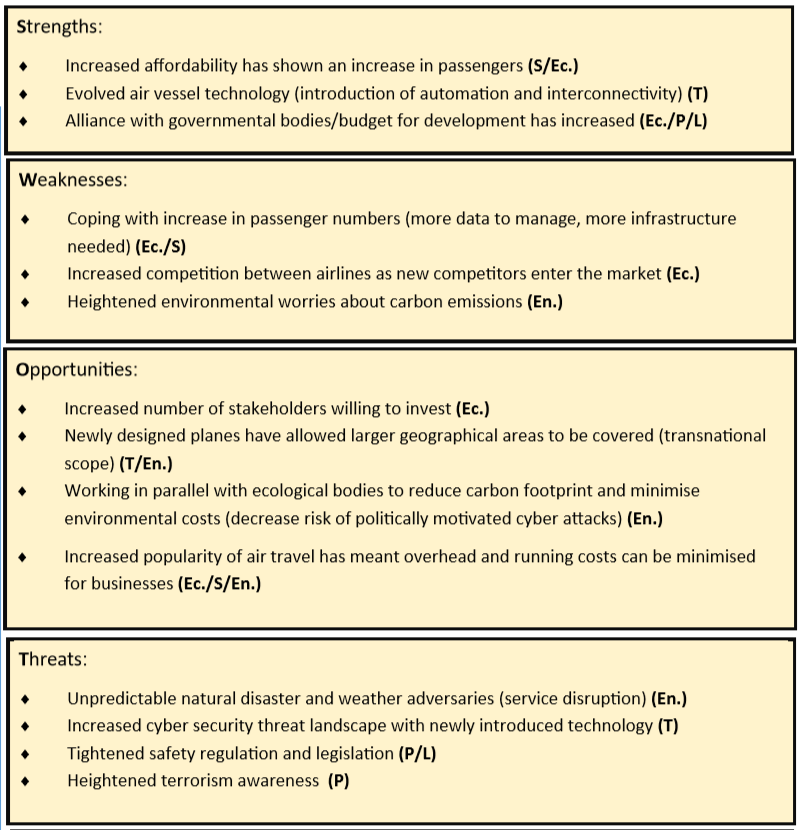
These external factor analyses combined highlights a variety of factors and issues that may affect IA within aviation. Understanding the environmental factors that may affect aviation can help us interpret the complexity of security challenges that may arise.
Right! Hopefully I haven’t lost you quite yet… Cue the next aviation tune!
Would You Risk It For a Chocolate Biscuit?
Or rather, what wouldn’t you risk?
Now we move onto the “nitty-gritty” of risk analysis. As I mentioned earlier, the aviation industry is extremely complex – and therefore for this project I divided the risk into three sections: Air Vessel, E-Commerce and “On the Ground”.
A risk analysis was completed for each section ( to the best of my ability!) including the vulnerabilities exploited, the potential threat agents and an approximate risk rating (1= Low, 7 = Critical). Please note that this risk analysis won’t be everything that can go wrong – but rather a small selection of what could go wrong.
NB: You may notice the identification of the type of data affected by the threat (if applicable!)
Air Vessel
The air vessel risk analysis identified items that could potentially go wrong relating to the actual plane itself.
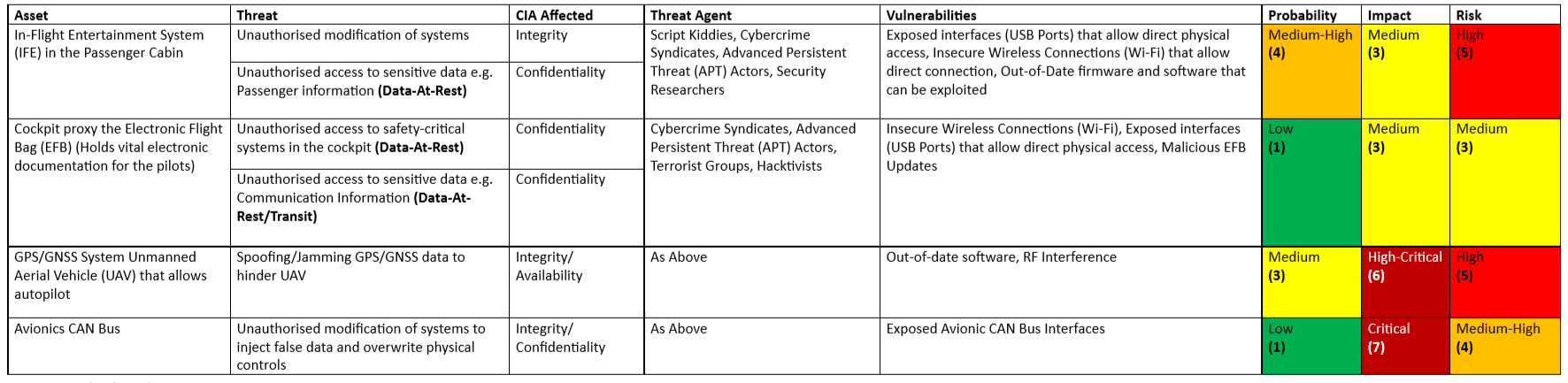
Assessing the risks in air vessels was complex and deeply technical. Ranging from items such as the IFEs to the GPS systems and avionics components – the risk analysis could have gone into much deeper technical detail. Although this table only highlights a select few assets that can be attacked, this was an area that was really interesting for me – and definitely a topic for future blog posts and research 🙂
E-Commerce (Websites)
A common factor of e-commerce, the following risk table focuses primarily on the common security risks and threats relevant to websites.
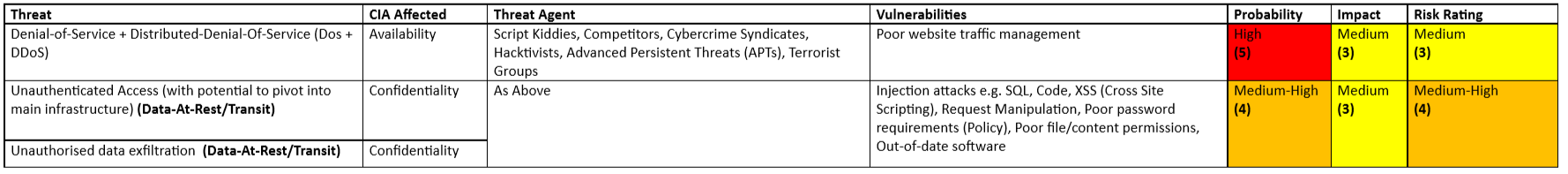
You could probably apply the OWASP Top 10 to e-commerce websites, check it out here.
“On the Ground”
“On the Ground” refers to anything logistically relevant to aviation from “the ground”. This can range from airport assets to ground transportation, primarily this table focuses on air traffic management, airport infrastructure and baggage handling assets.
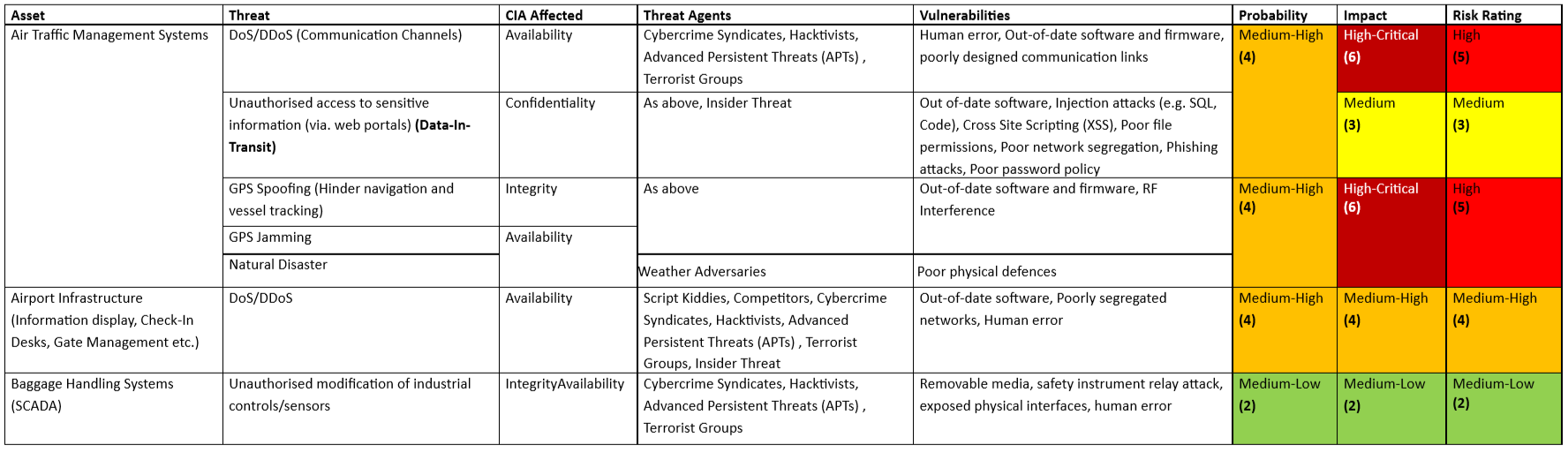
Likewise to the risks relevant to air vessels, this area was pretty complex too and expands out into different domains such as supply chain processes. Similar to identifying risks in air vessels, “On the Ground” risk research is definitely on the cards for another blog post 🙂
I Got 99 Problems, But an Attacker Ain’t One
So we’ve identified (some of) the things that can go wrong… Now we can speculate on some of the mitigation plans to minimise these risks! Mitigations were chosen to prioritise those with the most common vulnerabilities and utilised aspects of McCumber’s cube using both detective and preventative measures – ensuring that the mitigations were varied across human factor, policy and technology.
| Vulnerability | Type of Mitigation | Recommendation |
| Out-of-date Firmware/Software | Technology | Regularly schedule software/firmware updates |
| Removable Media | Policy | Implement strict removable media control policies |
| SCADA Relay Attack | Technology | Protect instrument relays within SCADA systems |
| Human Error | Human Factor | Deliver staff training to minimise human error |
| Poorly Segregated Networks | Technology | Implement proper network segregation and configuration |
| Radio Frequency (RF) Interference | Technology | Use encrypted communication channels, have backup timing sensors that can determine GPS whilst system is restored, software to help distinguish false and detect jamming attemp information, install blocking antennas |
| Phishing Attack | Human Factor | Staff security awareness training |
| Poor password requirements | Policy | Implement hardened password policies (e.g. include special characters, numbers, capitalisation) |
| Injection attacks (e.g. SQL, Code) | Technology | Deploy input filtering |
| Cross-Site Scripting (XSS) | Technology | Enable XSS filtering |
| Poor File Permissions | Technology | Review content permission and access controls |
| Exposed Physical Interfaces (USB+CAN) | Technology | Disabling unnecessary physical interfaces/minimise access |
| Poor website traffic management | Technology | Server-side installation of flood prevention tools, Installation of detection tools to identify attacks, Set up Web Application Firewall (WAF) Rules to help filter traffic and re-route traffic, Ensure backups of content are continually made |
Some of the mitigations can be used across different components and vulnerable assets within the threat map of aviation. For example “Exposed Physical Interfaces” can apply to both interfaces within an air vessel, or those found in SCADA baggage handling systems.
This obviously isn’t the “end all, be all” of mitigation plans for aviation – but provides a sneak peek into what can be implemented to reduce risks relevant to the airline industry.
It’s *that* time again…. Next tune, please!
Business As Usual
So, this is turning out to be a pretty beefy blog post. If you’re still with me, thank you and congrats! Next up for our IA analysis on the aviation industry, is the creation of potential business continuity plans for critical incidents identified from our risk matrices.

These incidents were selected from the completed risk matrices as those that would have a substantial affect if attacked and/or compromised. As well as identifying these incidents, the most critical incident response stages for that incident were selected as well as business continuity metrics and potential disaster recovery processes.
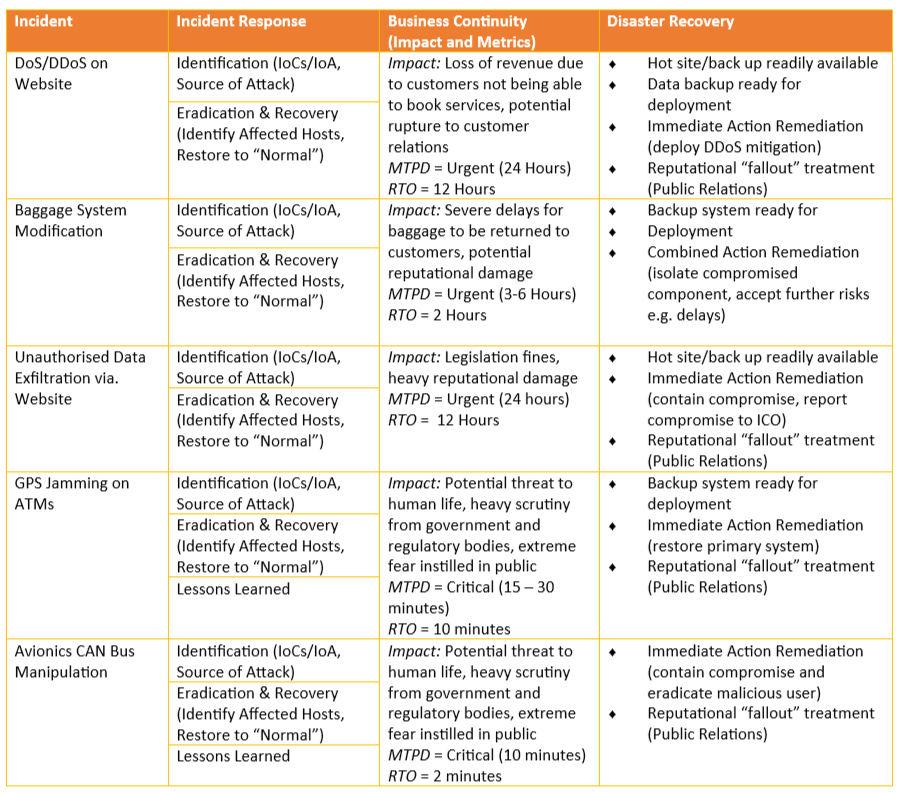
Glossary
- IoC = Indicators of Compromise
- IoA = Indicators of Attack
- MTPD = Most Tolerable Period of Disruption
- RTO = Recovery Time Objective4
- DoS = Denial-of-Service
- DDoS = Distributed Denial-of-Service
- GPS = Global Positioning System
- ATM = Air Traffic Management
- CAN = Controller Area Network
The above table primarily focused on business continuity objectives, including the main impact and relevant metrics such as the MTPD/RTO for each incident. Disaster recovery steps were also speculated, chosen as potential “steps forward” to achieve business-as-usual after an incident.
Business Continuity Metric Definitions
Most Tolerable Period of Disruption
This is defined as the maximum time period allowed of disruption or unavailability of a service before the impact is deemed as unacceptable. This metric is used to gauge the level of disruption accepted before it may cause harm to an organisation.
Recovery Time Objective
This is defined as an identified time period that a service must be restored after an incident or a disaster. This metric is used to avoid severe organisational consequences related to breaks in business continuity.
Morgan will be writing a post about the how-to’s of Business Continuity soon – when it’s posted I’ll link it here!
Final Boarding Call
Wowza, in this post we’ve been through a lot in quite a short space of time – and I hope I didn’t lose you! To recap we have covered the following: initial research, external analyses (PESTLE & SWOT), risk assessment, mitigation assessment and business continuity and disaster recovery plan speculation. And now we are here, at the final phase of the blog – closing thoughts!
The aviation industry is a growing enterprise; with the introduction of thousands of complex systems and new-age sensors that generate physical data of vessels – it is expected that by 2026 the aviation industry will generate 98 billion gigabytes of data. With legislation such as the General Data Protection Act, the data produced in aviation must also be protected and processed correctly to remain in line with regulations and laws to avoid monumental fines and protect customer relations.
Alternative to customer information assets, the aviation industry also has the opportunity for more drastic attacks on information more business oriented rather than customer centric. Attack on enterprise data, such as plans for business strategy or confidential trade information, can affect the market forces within the sector and fluctuate competitive advantage between competing brands.
Linking these different types of assets provides a large attack surface for malicious actors to compromise. It is important to assess the risk specific to each asset in aviation and adjust risk management techniques accordingly to ensure that this sector is adequately protected against cybercrime against information and data. In addition to this, efficient business continuity plans and disaster recovery strategies must be implemented to ensure in the case of a cyber-disaster operations continue as normal as soon as they can.
One of the most important objectives is to conserve organisational integrity of participating enterprises and safeguard the industry as a whole to avoid safety-critical consequences and vast disruption across global services. This blog only provides a preview into the security challenges the aviation industry faces, and I’m sure they’ll be more aviation blog posts from me in the future 🙂
I hope you enjoyed this slightly lengthy and academic blog, it’s something a little different – so hopefully you now have an insight into aviation security from an information assurance perspective.
– Sophia x
References
- Air Electro, n.d. In Flight Entertainment—What Will the Leaders do to prevent Cyber Attacks. [Online]
Available at: http://www.airelectro.com/blog/industry/in-flight-entertainment-what-will-the-leaders-do-to-prevent-cyber-attacks/ - BusinessWire, 2019. Global Online Airline Booking Market 2019: Air Travel Bookings Via Mobile Apps Becoming More Popular – ResearchAndMarkets.com. [Online]
Available at: https://www.businesswire.com/news/home/20191218005620/en/Global-Online-Airline-Booking-Market-2019-Air - Chabrow, E., 2011. Flaws Found in Air Traffic Control Systems. [Online]
Available at: https://www.govinfosecurity.com/flaws-found-in-air-traffic-control-systems-a-3569 - Cyber Israel, n.d. Civil Aviation Cyber Security. [Online]
Available at: https://www.first.org/resources/papers/telaviv2019/INCD-Tom-Alexandrovich-Civil-aviation-cyber-security-threats.pdf - Department of Transport, 2018. Aviation Cyber Security Strategy. [Online]
Available at: https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/726561/aviation-cyber-security-strategy.pdf - House of Lords, House of Commons, 2018. Cyber Security of the UK’s Critical National Infrastructue. [Online]
Available at: https://publications.parliament.uk/pa/jt201719/jtselect/jtnatsec/1708/1708.pdf - Houston, J., 2019. Why air travel is so cheap. [Online]
Available at: https://www.businessinsider.com/why-air-travel-is-so-cheap-2019-11?international=true&r=US&IR=T - Juneja, P., n.d. PESTLE Analysis of the Global Aviation Industry. [Online]
Available at: https://www.managementstudyguide.com/pestle-analysis-of-global-aviation-industry.htm - Korolov, M., 2019. What is GPS spoofing? And how you can defend against it. [Online]
Available at: https://www.csoonline.com/article/3393462/what-is-gps-spoofing-and-how-you-can-defend-against-it.html - NASA, 2018. Cyber- Threat Assessment for the Air Traffic Management System: A Network Controls Approach. [Online]
Available at: https://ntrs.nasa.gov/archive/nasa/casi.ntrs.nasa.gov/20180000393.pdf - NCC Group, n.d. Aerospace. [Online]
Available at: https://www.nccgroup.trust/us/our-solutions/your-sectors/transport/aerospace/ - O’Mara, J., 2019. Aviation Industry Leaders Report 2019: Tackling Headwinds. [Online]
Available at: https://assets.kpmg/content/dam/kpmg/ie/pdf/2019/01/ie-aviation-industry-leaders-report-2019.pdf - Rosen, E., 2017. As Billions More Fly, Here’s How Aviation Could Evolve. [Online]
Available at: https://www.nationalgeographic.com/environment/urban-expeditions/transportation/air-travel-fuel-emissions-environment/ - Santamarta, R., 2016. In Flight Hacking System. [Online]
Available at: https://ioactive.com/in-flight-hacking-system/ - UKEssays, 2017. Airline Industry SWOT Analysis. [Online]
Available at: https://www.ukessays.com/essays/tourism/a-swot-analysis-of-the-aviation-industry-tourism-essay.php - Wyman, O., 2017. The Data Science Revolution That’s Transforming Aviation. [Online]
Available at: https://www.forbes.com/sites/oliverwyman/2017/06/16/the-data-science-revolution-transforming-aviation/#47c8ba0a7f6c