Estimated difficulty: 💜🤍🤍🤍🤍

Happy Friday and happy (continued) cybersecurity awareness month! For those of you that don’t know, October is renowned for being cybersecurity awareness month – a month dedicated by security professionals to raise awareness in cybersecurity, specifically to the everyday user of technology that may not be security-savvy.
Following on from Morgan’s last post about romance scams, this week I decided to write a blog post on how to be more aware with what you post on social media and how it can be used against you if you have poor OPSEC on your social media profiles.
What is OPSEC?
OPSEC aka. “operational security” was a term first used by the U.S. military to describe the process to strengthen defences and keep the knowledge of their strengths and weaknesses away from enemy forces. Adopted by the security industry, OPSEC is now similarly described as a process to protect sensitive information and deny the analysis of targets – which is usually done through tactics such as Open Source Intelligence (shortened to OSINT, this is the act of gathering information on a target through public and free resources e.g. Google) and doxxing (the act of finding private and identifying information and publishing it with malicious intent).
“How does this relate to me?” You might ask. Well, with an estimated 4.57 billion people (over half the world’s population) on social media, that’s a lot of public information that can be abused and potentially weaponised by malicious actors.
Let’s hypothesise and talk about an (unfortunately) common example of poor OPSEC practice.
– Bob has just had his 21st birthday, he’s super excited to reach the big 2-1. Everyone wishes him a massive happy birthday, and posts on his Facebook wall. Unknown to Bob, unfortunately his profile is completely public – which means anyone, even people that aren’t his friends, can see his profile and everything on it.
– Alice is a fraudster, and lives the life of crime. Her favourite pastime is to try to access bank accounts, but of course – she does not have anyone’s password to access them. Through OSINT she notices Bob’s bank only requires him to provide his birthday as a security answer to reset his online banking password…
– Alice visits Bob’s profile, and sees Bob just turned 21 recently. Doing a few quick maths calculations, she figures out that Bob must have been born on the 14th of July 1999.
– Alice visits Bob’s banking website, and using his birthday as a security question – is able to reset his password. Oh no!
Of course this is a pretty simplified version of how poor OPSEC can be used against you (I’d be very worried if banks only required a birthday to reset your password) but hopefully you get the gist. 🙂
So what can you do to improve your OPSEC on social media? Below I’ve compiled a quick list of things to avoid posting, and why – as well as some real-world examples (redacted of course, with sensitive information highlighted in red).
Disclaimer: How extremely you implement OPSEC, is of course personal preference. For example, I know that personally I’m quite forgetful/sloppy at times! The purpose of this post is to raise awareness around the subject, and guide individuals to make the right choices when it comes to their social media content.
Credit and Debit Card Numbers
This one is fairly obvious and quite straight forward to avoid. Simply put, if you post your credit card number online – fraudsters and cybercriminals can use your credit card to make their own purchases, or collect your credit card details to re-sell on the dark web for profit.
IRL Example
And as exciting as receiving a new credit/debit card is, don’t be this guy…

Work ID Cards
We all love a good selfie, especially after a long week at work – it’s great to talk a Fri-yay pic to share on our socials. But if you do, remember not to include any work ID badges in your picture – by showing the world your work ID card, criminals can get an insight into the cards used at your company to prove employee status. These cards can be copied by fraudsters and reproduced as an attempt to try unlawfully entering your work place, and more!
IRL Examples
#workselfie on Instagram shows a lot of selfies that include work ID cards:

House Photos (Street View)
Now this is one I can be quite forgetful about! If you follow me on Twitter you may see a few slip ups for this, because unfortunately the love for my zoomies clouds my judgement at times…
Some people love to share the work they’ve done on their house, or perhaps they’ve tidied up the front lawn. Maybe they’ve just moved house, or maybe (*ehem SOPHIA*) they want to show off their cars on their driveway. But by showing the exterior of your house, unfortunately this is potentially exposing to criminals where you live. Especially if you have shown a house number, or perhaps tagged your town as a location – criminals can use this information to use tools such as Google street view to find out your exact address.
Although your address could be used for happy surprises (like pizza deliveries), they can also be used by fraudsters as fake addresses – or abuse knowing the address to commit crimes such as burglary.
IRL Examples
#newhouse and #moveinday on Instagram can be used to track house photos – and sometimes people even include the exact neighbourhood…

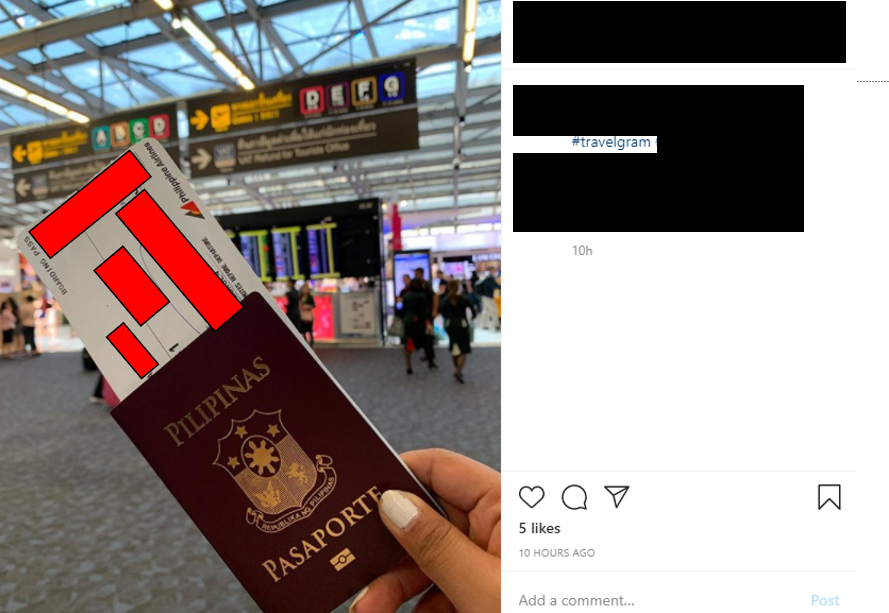
Boarding Passes
A lot of people post their boarding passes online, usually as a celebration that they’re about to embark on holiday. But did you know that the information on a boarding pass (like the barcode, booking reference etc.) can be used to expose personal information about you?
Recently an individual was able to obtain a former Australian PM’s passport number, personal telephone number and details about his flight from a boarding pass posted on Instagram. The TL;DR was that the individual was able to use the booking reference to login to the flight provider’s web platform and scour for further information. If you want to learn more about it, Alex has written a blog about his findings here. In addition to using references to login to web platforms, the barcode on a boarding pass can also expose the details about your flight and other personal information such as your full name.
IRL Examples
We return to Instagram! If you search #travelgram or anything to do with travel – it appears to be a treasure trove for boarding pass photos:
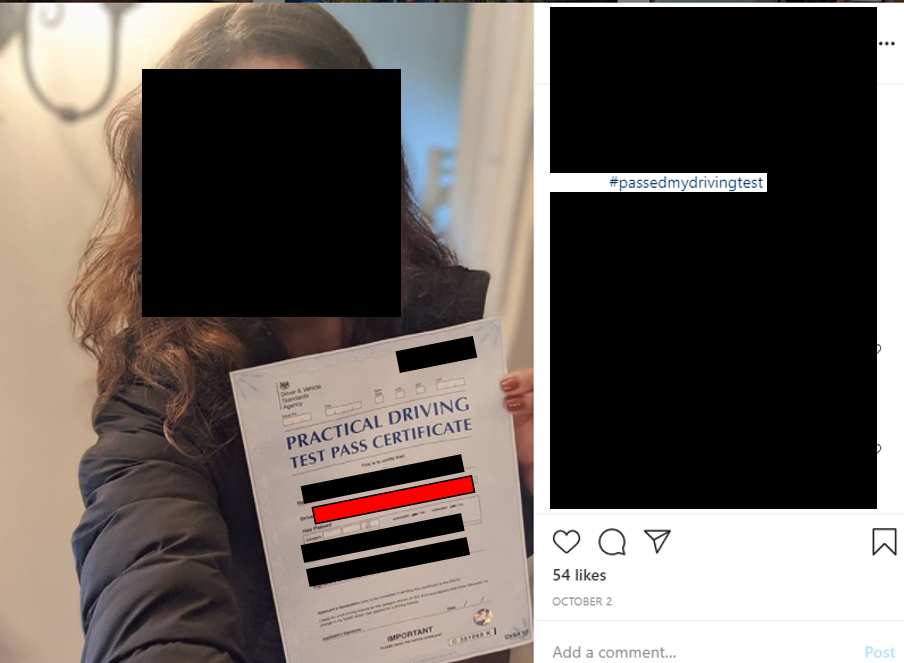
Personal IDs
This can be anything from drivers licenses, certificates, passports – basically anything that can be used to identify you. It’s important to keep information like this private as fraudsters can use information to commit identity theft, or use personally identifiable information (such as a passport number, or a birthday) to try bypass security mechanisms when accessing sensitive accounts. It’s fun to show off if you’ve passed your driving test, or maybe have a chuckle about how bad your passport photo turned out – but remember to keep any identifiable information redacted and secret!
IRL Examples
More hashtags, this time we have tried #passedmydrivingtest…
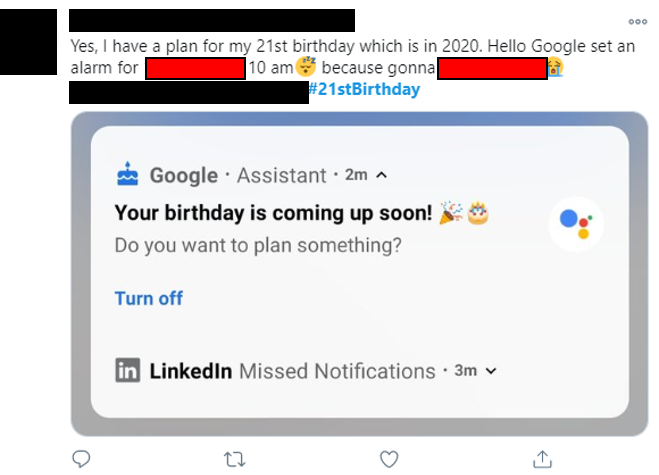
Birthdays
Now this is the big one! A lot of people love to celebrate their birthday, and hey – there’s nothing wrong with that! However birthdays can be used to identify you, usually as a form of verification (like trying to access accounts) or as part of the login process to online platforms (I’ve had this before!). This is why it can be worrying when strangers know your birthday, as criminals may use this to try access your accounts or commit identity theft and fraud.
IRL Examples
To Twitter! #21stBirthday reveals several users celebrating their birthday, or announcing when their birthday would be.
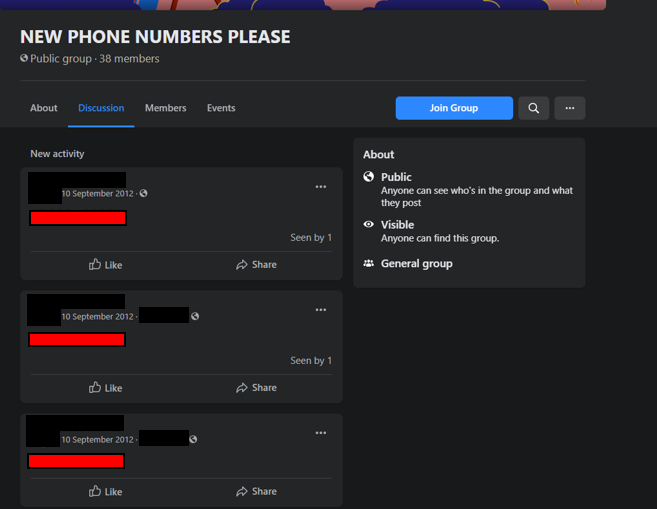
Phone Numbers
So thankfully I don’t see this one too often, but that doesn’t mean it doesn’t happen…
Fraudsters finding out your phone number can not only be super annoying (vishing and cold calls incoming!) but similar to other personal information, can be used as part of a verification process to access accounts (i.e. “Can you confirm the last 3 digits of your phone number please?”). Phone numbers are also a type of PII – Personally Identifiable Information, which means that attackers and individuals can use your phone number to confirm your identity. Having your phone number exposed can cause some serious privacy concerns, so be wary of where you post them – and ensure you trust those that you give your number to, too!
IRL Example
A group that I stumbled across on Facebook, that was completely public…
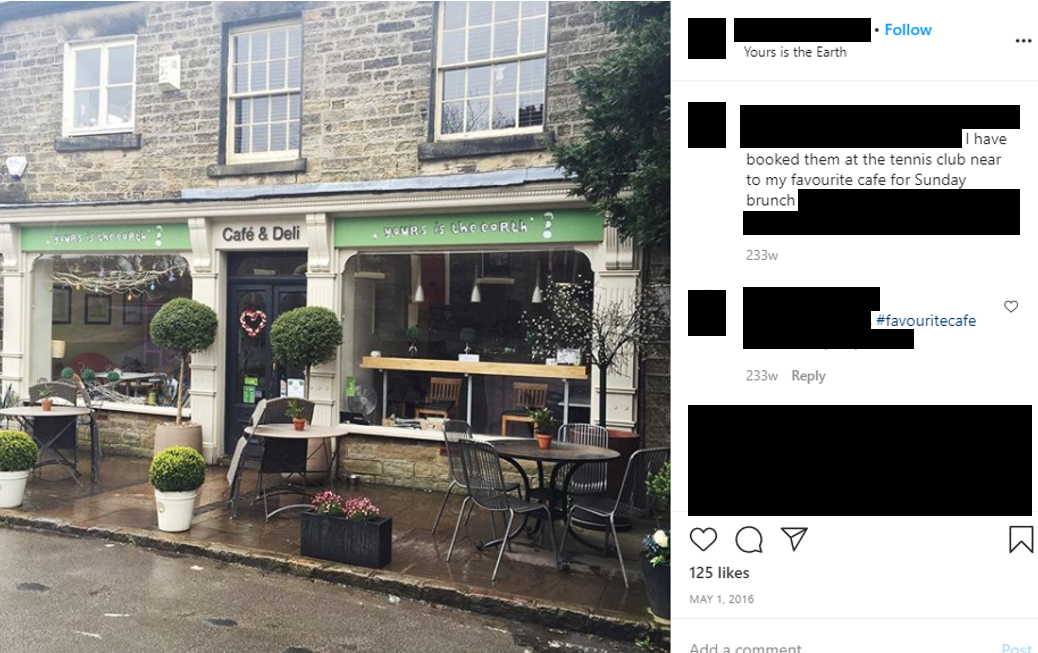
Location History
So, what do I mean by this? Anything from geo-tagging your pictures to “checking-in” on Facebook, location history can be used by attackers to identify your current or future location alongside daily-life patterns (such as visiting your favourite coffee store every morning and checking in). Why is this bad? Well, by identifying your location and your whereabouts – criminals can use this information to commit crimes such as breaking into your house (you’ve just checked in overseas, so that means your house is empty- no?), or even stalking (they know you visit the same café every morning…).
Similarly to previous items in this post, it all boils down to maintaining your personal privacy. It’s okay to boast about an amazing meal that you had at #<insertrestauranthere> – but be careful of who can see this, especially if it’s completely public.
IRL Example
More hashtags! This time a #favouritecafe shows a few posts on Instagram (both checking-in and tagging!)
General Tips
So I’ve gone through a few of the most common OPSEC slip-ups I can think of, but I’ll also talk through a few “top tips” that can help you lockdown your online life and protect your digital self:
– Check your privacy settings on your social media profiles – ask yourself, who can see this? Do I want them to see this?
– Never post any personal information on public-facing forums or profiles. This includes information that can be used to identify you such as IDs and phone numbers.
– Be wary of the content you post…. Is there anything in the background of a photo that you didn’t realise was there? Are you posting content that can be used to answer security questions (e.g. first pet’s name, mother’s maiden name)?
– Stranger danger! Be careful of who you accept friend + follow requests from on private profiles – do you actually know this person? Would you want this person to see the content you post on your profile?
And that’s a wrap!

I hope you enjoyed this mini-OPSEC-bootcamp, stay safe online and remember to be cautious of the interwebs…
– Sophia x