Estimated difficulty: 💜💜🤍🤍🤍
It’s been a while since I’ve written about zoom hax, if you’re new to Security Queens – you can find my last blog post on hacking cars via. the Control Area Network (CAN) here.
Instead of focusing on physical CAN bus hacking, this blog post will do a quick rundown of LiDAR and how attackers target this technology to compromise Connected and Autonomous Vehicles (CAVs).
What is LiDAR?
So first thing’s first, what is LiDAR?
LiDAR is short for “Light Detection and Ranging” which is a sensor method that uses pulsating light lasers to measure distances to help approximate three-dimensional data about surroundings. LiDAR systems often work by using a 360 degree rotating scanner which emits thousands (and thousands!) of laser pulses every second – once these pulses clash with objects in an environment, they “bounce” back to the scanner. These reflections are used to help plot a 3D map of the surroundings, measuring the distance and the speed of the which the laser pulses reflect from the objects they collide with.
LiDAR technology has an incredible accuracy of +/- 2cm and can detect objects up to 60m away allowing systems to generate large-scale maps of their surroundings, because of this LiDAR is commonly used in driverless vehicles.
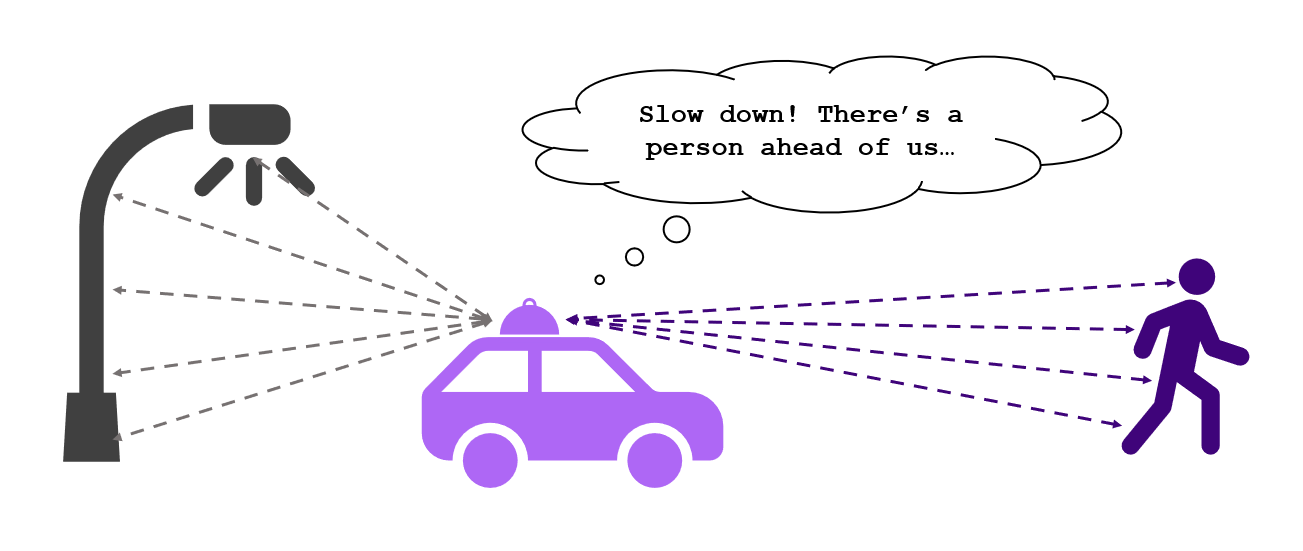
LiDAR is used by a huge variety of transportation, including aviation and automotive systems, and in recent years has been implemented to enable autonomy in transport. LiDAR also works in parallel with other technologies, such as GPS (Global Positional Systems) to help geographically map surroundings to aid navigation or emergency response systems.
LiDAR Usage in Connected and Autonomous Vehicles (CAVs)
As we move towards an autonomous future, LiDAR becomes increasingly popular in Connected and Autonomous Vehicles (CAVs) to assist with driverless capabilities as CAVs become the new social norm.
LiDAR helps vehicles achieve autonomy by detecting objects which is then relayed through other systems within the car such as an Advanced Driver Assistance System (ADAS). LiDAR data may also be processed by AI and machine learning decision-based components to allow efficient, and most importantly safe autonomy. The combination of all these systems allow the car to make safety-critical decisions for future automated movements that protect the driver and passengers of the vehicle whilst successfully achieving autonomy.
CAVs may also use other embedded technologies and sensors such as camera, radar, ultrasound and microelectromechanical systems (MEMS) to achieve complete automation that does not need driver input.
What are the Risks & Vulnerabilities?
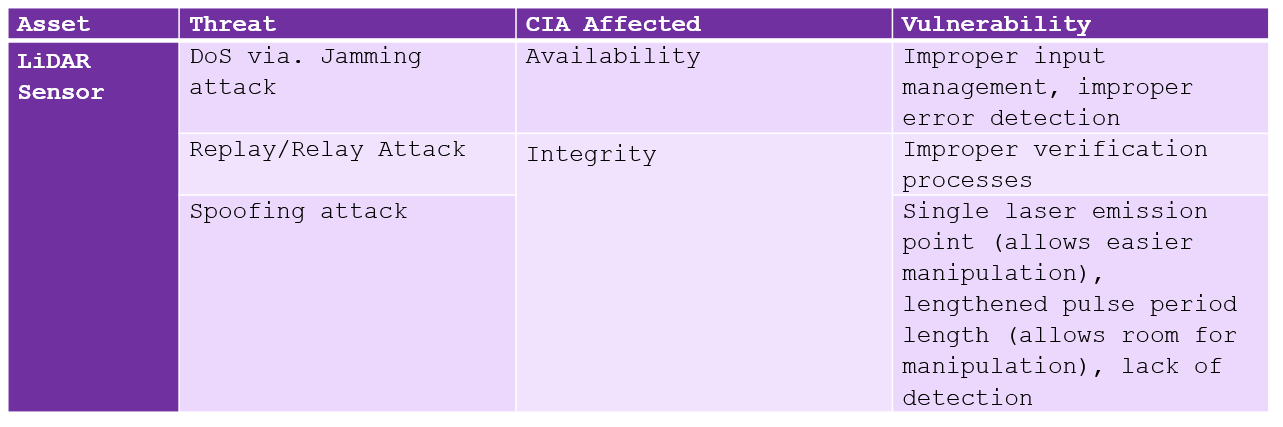
As with all technologies, LiDAR has various risks and vulnerabilities that could severely impact the safety of a driverless vehicle and those inside it.
Below you can find a risk table detailing the common attacks on LiDAR systems:
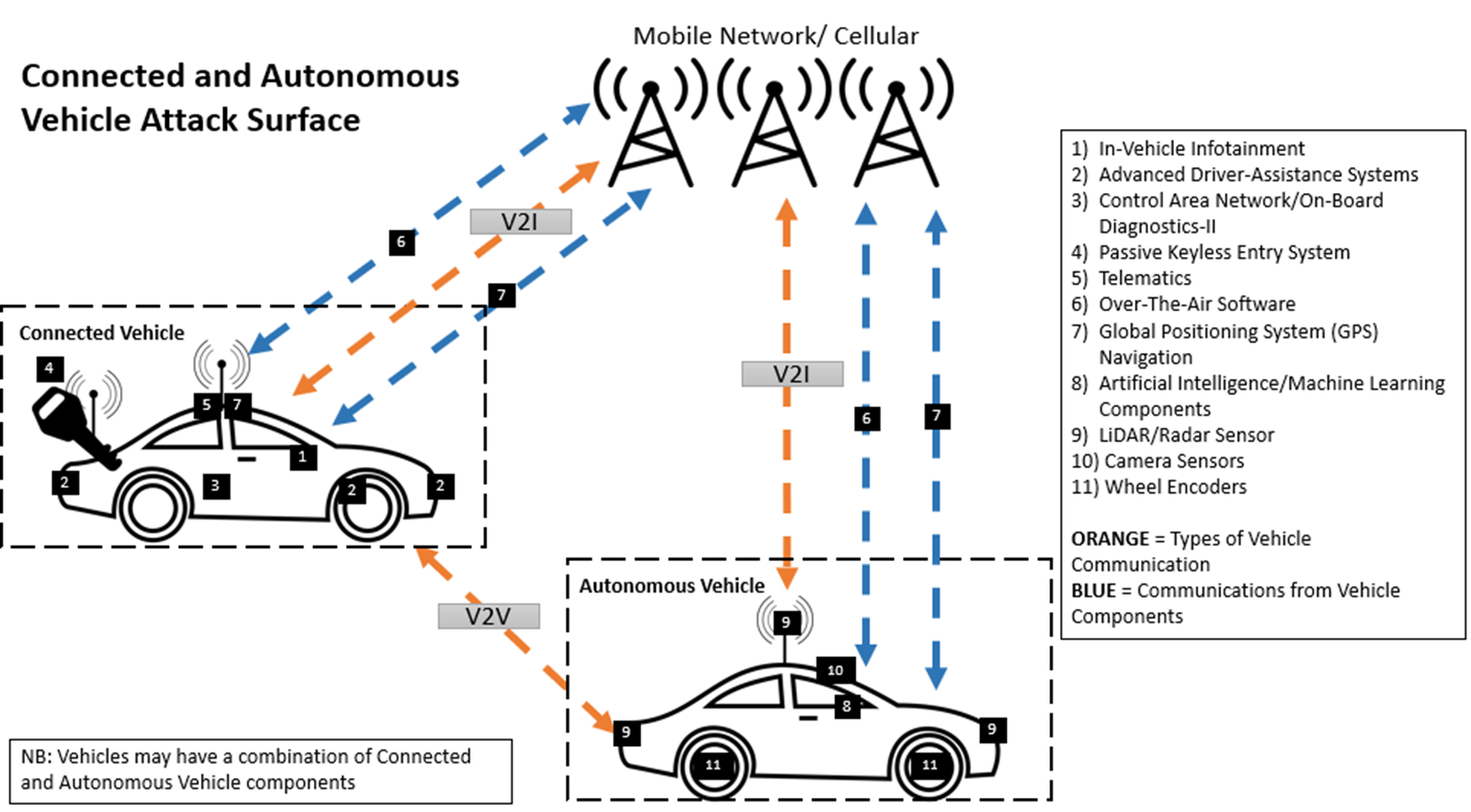
As CAVs become increasingly popular and normalised in the public market, and more embedded technologies are used, the threat landscape for a vehicle becomes larger as security-related risks and issues emerge. Below I have included a simplified attack surface diagram that combines both autonomous and connected capabilities:
Example Case Study:
Spoofing LiDAR with $60 and a Raspberry Pi
According to an IEEE blog post; Jonathan Petit, who is a principal scientist at Security Innovation, presented a paper at Blackhat 2015 that details his research whilst he was a fellow at the University of Cork’s Computer Security Group. During his time as a research fellow, Petit successfully designed a setup utilising a laser and a pulse generator, although claims that “you can easily do it with a Raspberry Pi or an Arduino”.
First he recorded pulses from a LiDAR unit, some of which reflected an obstruction, which he reports were not encoded or encrypted that could allow them to be replayed at a later point. The most difficult part of the experiment was to time the replay at the correct moment, so it was synchronised with the generated pulses of the LiDAR unit.
This technique could be easily replicated to create the illusion of fake objects and make multiple copies of obstacles and movements. Or even be used to perform a denial-of-service attack on the system by multiplying the spoofed pulses in the thousands!
On a slightly simpler note, you can also perform a denial-of-service attack by dazzling LiDAR sensors using a simple laser pointer…
You can find Petit’s Blackhat presentation here, and the full paper here.
And that’s a wrap! A nice little zoom hax rapid read to kick off our blog posts of 2022…
Until next time,
Sophia x