Estimated difficulty: 💜🤍🤍🤍🤍
Passwords have been a form of securing your accounts for years. They are your key to unlock the door to your account for want of a better metaphor. You are the only person that should know your password, as the creator and keeper of this information. My post will try to help you understand the importance of creating a strong password and why. This is not aimed at people well adept in security, but for those that have never even heard of security before! There are many elements to this topic that can be covered, so I apologise in advance if there is anything I might have missed! Let me know your thoughts. 🙂
Creating a Strong Password
Passwords have evolved massively through time. A password that might have been considered strong years ago, will most likely not be strong today. If you are still using a password from years ago then I highly recommend changing it as soon as possible! By increasing the strength of your password, you are increasing the time it can take an attacker to crack it!
DO’S
Yonks ago I remember listening to Freaky Clown present a talk on Social Engineering and passwords. One thing that he said, that has always stuck with me, is that you should make your password a memorable phrase. Other blog posts written to inform people on password practices have said that three well-chosen random words are the way to go when creating a strong password. With such information, it became clear to me that passwords do not have to be complex, such as the ones that can be generated for you by platforms such as password managers and other online platforms. Certain password policies will require you to use a symbol, number, capital letter and have a minimum length, so by working these in alongside your pass-phrase, you are making one super secure password! Symbols, letters and capitals are not always the be-all and end-all… White space can increase the entropy of a password by making it harder to guess by increasing the randomness of the password. It is, therefore, less likely to be in common password lists, unless leaked.
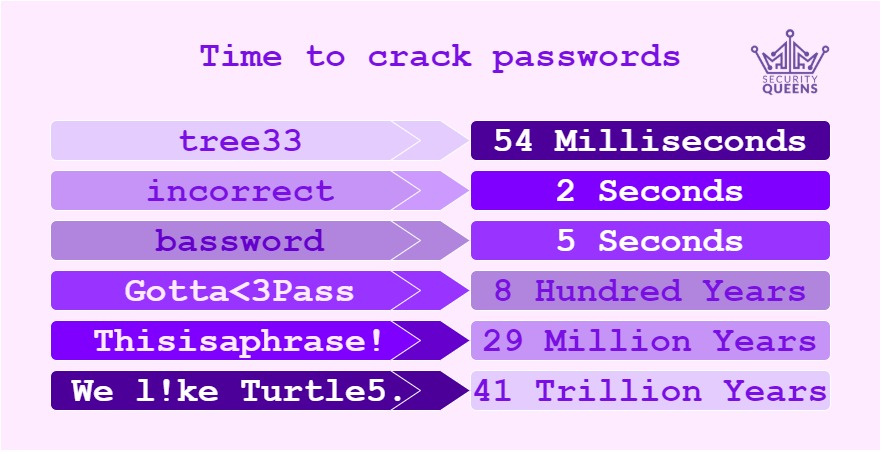
The graphic showing how long it takes to crack a password gives some examples of what your passwords should be looking like, however, I have also included an example for you to help clarify what can be considered a strong password:
We l!ke Turtle5.
The above example includes capital letters, a number, symbols, white space and is pretty lengthy! Overall I would say it is a pretty good password, and by the online tool How Secure is my password‘s standards, it would take 41 Trillion Years to crack. It is difficult to accurately estimate the time taken to crack a password as this will vary on the compute power of the attacker and their resources. (Disclaimer, we do not recommend you start entering the passwords you use in the wild into random online applications. )
DON’TS
Most websites or applications should not allow passwords that are too short and simple. Policies are generally in place to prevent users from creating accounts with insecure passwords. However, from testing this theory recently, this is not always the case. One popular website allowed passwords as simple as “bassword” to be created and used for an account. Overall, this just means we cannot trust the application we are using to guide us in making the right password decisions! Thank goodness you are reading this post then aye. 😉
I took the premise of the bad password “bassword” and tested it against a Have I been Pwned website. It was safe to say that this password had been leaked over 300 times in previous data breaches and would take 5 seconds to crack. I have included another example of what a password shouldn’t look like:
tree33
Even with the numbers added the length is still too short and does not have the complexity required to make it hard for an attacker to crack, even if the password was not leaked, as it is easy to brute force by an attacker. This password would take 54 milliseconds to crack in comparison to our strong password example!
Password Checklist!
I have included a simple checklist of everything that has been discussed in how to create a secure password:
| Description | Tick |
| Password contains at least one capital letter. | |
| Password contains at least one number. | |
| Password contains at least one symbol. | |
| Password contains white space. | |
| Password is longer than 14 characters. | |
| Password is unique to the account being created. | |
| Password contains at least three different words. |
Basically avoid what this guy did in the meme! :’D

Why?
As mentioned previously in this post, I have used the term cracking to justify why we should create a strong password. But what really is cracking a password, and how would an unauthorised person gain access to my password? Well, you are asking the right questions!
Unauthorised Access
There are many different ways an attacker can gain access to your passwords. There may have been a data breach in which thousands of credentials, personal information and financial data would have been leaked or stolen. One of the most recent breaches I know of has been the EasyJet data breach, which you can read more about here. Other ways in which unauthorised access can be obtained is remotely by bypassing security appliances in an organisations network and by exploiting vulnerable systems. Phishing is another method of attack, in which an attacker can send a deceptive email to you, which will redirect you to a malicious website prompting you to input your credentials through some kind of form or could install malware. Keystroke logging malware could be installed to capture your sensitive information, such as passwords and credentials; or they may take your credentials through the form you were redirected via the website link. There is much more detail to go into here, however, this would need to be covered more in-depth in a separate post.
There are steps that you can take to protect yourself against an attacker if they have obtained your credentials, such as multi-factor authentication, but that will be covered in an upcoming post by Sophia.
Password Cracking
In essence, once you create an account you are trusting that service provider with your information and credentials. There are many different types of applications you can create an account for, some being: banking, email, social media accounts, etc. For the companies storing your data, they have a duty of care to protect your data by law. However, breaches do still happen and storage is not always as secure as we like it to be. When passwords are stored for a website they are usually added to a large database of other credentials. Years ago we were in the dire situation of such credentials being stored in plain text or just with some level of encryption, a video by Computerphile explains this well. This meant that if an attacker did gain access to the system they could a) easily know your username and password, if in plain text or b) reverse the encryption used to store the credentials. However, the main focus of this post is looking at the hashing algorithm.
Hashing algorithms can be applied to passwords to compute a unique string of numbers and letters that is extremely difficult to reverse. Different types of algorithms can be used and some less secure than others. More complex algorithms can take more time to compute, but with an up-side of more time to crack also. A hash computed for one word will be the same if the same algorithm is applied. If even a single letter changes to that word and the algorithm is applied again the hash will be completely different. The downfall to just hashing is that it is then easier for an attacker to calculate hashes of wordlist and compare them to the hashes of a leaked database of hashes for example. To combat this flaw, salt, usually a unique string of letters and numbers, should be applied to hashing algorithms to compute a hash that is different to what would have been computed for the word alone. This means that an attacker would also need to know the exact salt used in the hashing algorithm to calculate the correct hash of the password.
To crack these hashes different methods can be used. These being brute-forcing and dictionary attack mainly. Brute-forcing password hashes will require the combinations of set parameters to be hashed and compared against an attackers hash list to find certain matches. For example, passwords containing just lowercase letters or passwords that have a short length combined with symbols, numbers will have fewer combinations. Dictionary attacks are more efficient as a word list is used instead of having to calculate the many different combinations of random characters. Words from the wordlist can be manipulated or combined increasing the scope of a password match. The time taken to crack these passwords is dependent on the compute power the attacker has. If a breach does occur and you are aware of it, make sure to change your password immediately. Another measure to protect yourself is to create unique passwords for each new account, so if a breach does occur it will not allow access to other accounts.
Password Cracking Tools
Tools have been created to crack passwords. I have listed a few below, but have only used a couple myself. Many other tools have been created to crack passwords:
- Hashcat
- RainbowCrack
- JohnTheRipper
- Cain and Able
- Ophcrack
- L0phtCrack
Managing your Passwords
Now it might be all well and good that you have now created a strong password, but we need to make sure you create many secure passwords for each different application! Password managers are a great way of keeping track of your credentials for many different applications. You must choose a password manager you trust. Personally, I use LastPass to manage my password. I like it because I can use it on my phone as well as my browser and it can just auto-fill everything in for me (this is not a sponsored post). It helps me to generate strong and unique passwords for each account, which is not always easy to think of. There is so much more to be said about password managers, however, that would need a whole new post altogether as there is so much to cover.
If you still feel skeptical about using a password manager, which is a valid response considering you are trusting one application with such sensitive information, there are guidelines on the National Cyber Security Centre (NCSC) website explaining why it is useful to use a password manager.
I hope this has been helpful to you and if you have anything to suggest or add please let me know 🙂
Sarah <3
This is a really cool post! I’ve been trying to find something to give to my friends who have struggled with password managers and I’ve found it difficult to explain to them what to do. This post does that really well, thanks!
I’m glad you enjoyed it Dan! Thanks for your feedback 😀