Estimated difficulty: 💜🤍🤍🤍🤍
Recently I was studying for CRT. To help myself and others revise, I thought I would make this blog post on management protocols and some of their common weaknesses and vulnerabilities. This is a high-level overview of some of these protocols and how to exploit them. We will cover the following:
- SSH
- SNMP
- TFTP
- Telnet
- NTP
A remote management protocol is something that specifies how to manage the connection between a remote server and a computer. An example of this would be where you might want to access a server hosted on AWS infrastructure. From the comfort of your new home desk/office setup, you could use a protocol such as SSH to access that said server.

SSH
SSH stands for Secure SHell, usually running on TCP port 22. Commonly you will use SSH using the command line on your host. This will work on Unix, Mac and Windows computers. Alternatively, other software is available to use, such as Putty, which will create a graphical user interface (GUI) to provide a friendly way for users to interact with the protocol. It creates an encrypted communication channel to the server, which allows you to pass commands to the host. A command can be in the format of the below example, however, check out the ssh manual for more information.
ssh username@server_name
There are multiple ways to authenticate using this protocol. Password, public key, host-based, keyboard, challenge-response and GSSAPI authentication are all valid methods. Public key authentication using strong cryptographic algorithms is an extremely secure way to implement authentication! Below is an example of how the SSH handshake works behind the scenes.
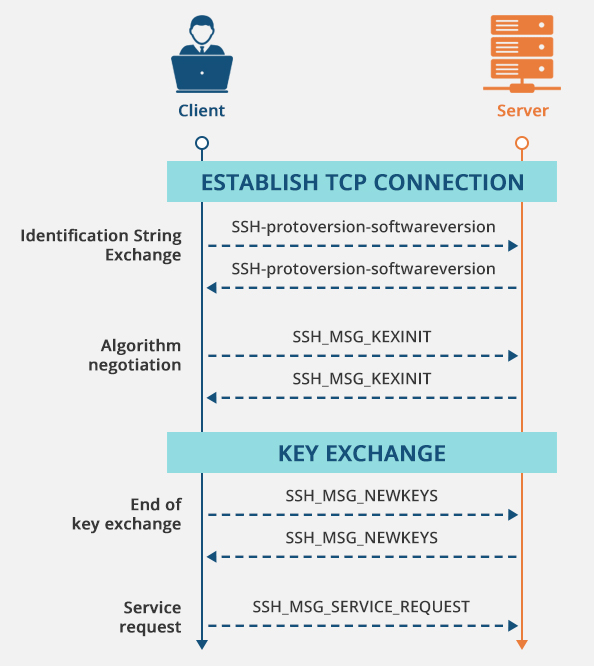
Security Weaknesses
As I previously mentioned, you can introduce security weaknesses with the use of SSH, if you only support using a password as a way to authenticate. This method is liable to brute-force attacks, and if the host is exposed then likely an attacker… With all the time in the world… Could crack a basic and short password. Ensure protective measures, such as implementing Fail2Ban or IP blocking in general, are in place. Other weaknesses for SSH have been listed in the below table, along with any relevant exploits. Other CVEs also exist relevant to SSH.
| Weakness | Description | Exploit |
| Weak SSH keys. | Shorter key lengths are weaker, as they are therefore more vulnerable to being cracked. If an attacker can intercept the private key and crack the value, then the communication is no longer secure. | You can use tools such as john-the-ripper to brute force values from keys. See a tutorial here. |
| Key exchange with unsafe groups and elliptic curves. | A handshake is used to perform key exchange, authentication and the selection of algorithms. Exploits of SSH can stem from weak algorithms (such as SHA1) being supported. | You can enumerate the algorithms using a Nmap script. |
| Old versions of SSH. | Arbitrary code execution, denial of service, directory traversal (for instances of SSH copy scp) and other vulnerabilities exist for older versions of SSH and protocols that implement SSH, such as scp and sftp. | You can fingerprint the version of SSH by connecting to the service using telnet.root > telnet <IP> 22Relevant CVEs may then apply to the version. |
| Passwords authentication enabled | As previously described, if password authentication is enabled an attacker can brute force the login to an account to gain access to the system. | A password list or username list may be passed into a tool such as Metasploit and each combination tested until a successful one is reached. |
| Default Credentials | If default creds are used, it would be easy for an attacker to guess and authenticate to the server. There are different combinations for different types of machines. | Try to authenticate to the machine using the different combinations. See Hack Tricks for more information. The Metasploit Module ssh-login can be used to enumerate these valid creds. |
SNMP
SNMP stands for Simple Network Management Protocol. This service is commonly run on managed switches, routers and servers for monitoring. These devices are called SNMP agents. SNMP often runs on UDP port 161. You can access the SNMP Management Information Base (MIB) by providing a valid community string.
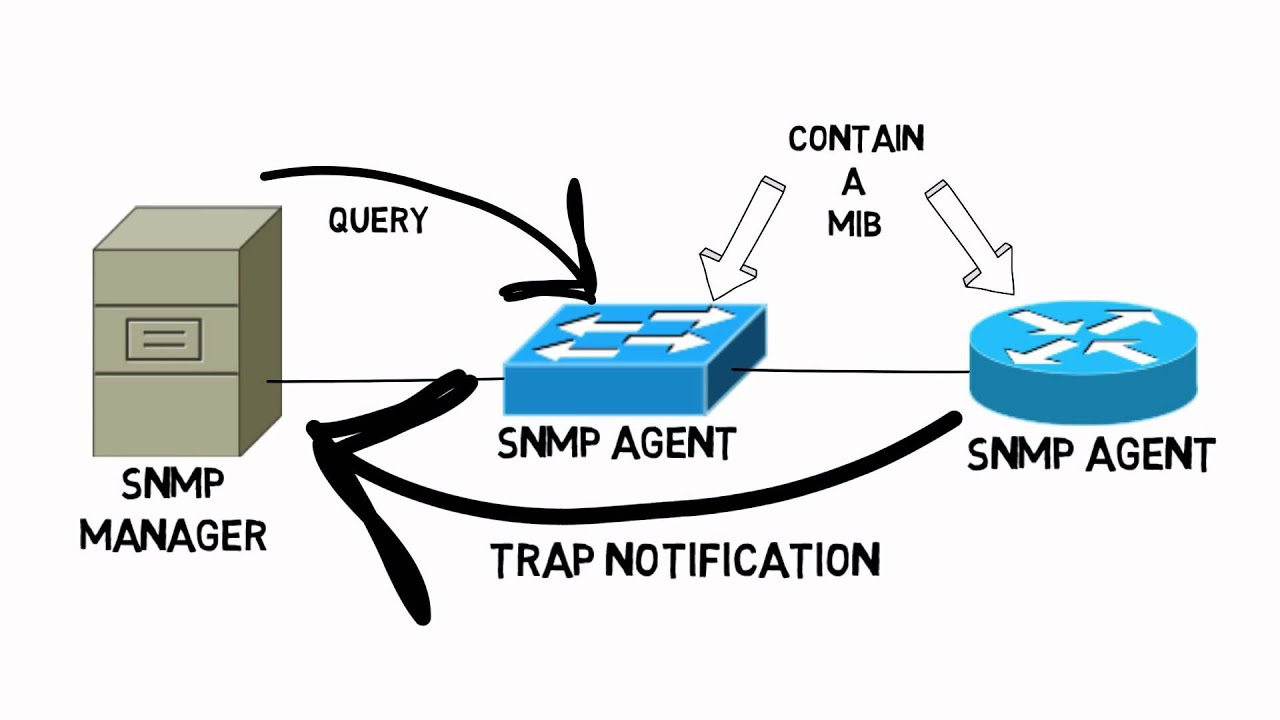
The MIB holds several Object Identifier (OID) values. These define the information that can be queried on an SNMP agent/managed device. Different OID values can bring back different information. See the below table for more details.
| OID | Information Retreived |
| .1.3.6.1.2.1.1.5 | Hostname |
| .1.3.6.1.4.1.77.1.4.2 | Domain Name |
| .1.3.6.1.4.1.77.1.2.25 | Usernames |
| .1.3.6.1.4.1.77.1.2.3.1.1 | Running Services |
| .1.3.6.1.4.1.77.1.2.27 | Share Information |
Trap notifications can be sent from an SNMP agent to the SNMP manager to tell the manager what, for example, their utilization is.
Security Weaknesses
The different versions of SNMP (versions 1, 2 and 3) have different vulnerabilities.
- Version 1: Community strings are used. There are read-only and read-write SNMP strings, meaning information can be queried if the read community string is known or information can be read or written if the read-write community string is known. The problem here is that default and the same community strings were set (public = read-only and private = read-write), meaning they were widely known.
- Version 2: Hard to set up and not widely used, even though security was tighter.
- Version 2C: A lot of information from MIB can be retrieved with a single command. However, security was rolled back to using community strings the same as in Version 1.
- Version 3: Encryption, integrity checking and authentication services are used making it a lot more secure, however exploits were still present, such as user enumeration.
The vulnerabilities have been summarised in the below table.
| Weakness | Description | Exploit |
| Default community strings set. | If default community strings are set, then it would be possible for an attacker to easily gain access to the MIB. All an attacker would need to do is use public or private when running a command to access a remote host running SNMP. | The below snmpwalk command can be used to retrieve MIB information.root > snmpwalk -v 1 -c public <IP>The default community string is public. |
| User enumeration. | Information stored on an SNMP agent can contain user details. Tools can be used to directly query this information. | SNMP-check is a great tool to use to query information of the SNMP agent. Tools such as snmpv3enum.rb can be used to determine valid users. root > ./snmpv3enum.rb -i <IP> -u <username>The Metasploit module snmp_enumusers can be used. |
| Brute-force of community strings and user passwords. | SNMP may use credentials to authenticate to the service. These can be brute-forced by a number of tools to gain access to and query useful information from the service. Similar goes for the community string. These may be set to default or weak values which can be easily brute-forced. | You can brute force the community string by interchanging the string value in the below command.root > snmp-check <IP> -c <string>You can brute force valid user accounts using hydra. root > hydra -U snmp |
| Useful information leakage. | Useful information may contain listening network services, usernames, internal IPs and running processes. Certain OID values may disclose certain bits of information, such as usernames. | you can use snmpwalk to query certain OID values.root > snmpwalk -c <string> <IP> <OID value> |
| Writing data to exploit the system. | If you can write to the SNMP agent then you may be able to overwrite values of the MIB to attempt a file upload or download, given that the TFTP service is accessible to the target host. | Two Metasploit modules allow file upload in Cisco devices if SNMP write access is achieved. These are cisco_config_tftp and cisco_upload_file. |
| SNMP server vulnerabilities. | Different versions of SNMP have existing vulnerabilities. | Some of these vulnerabilities can be found in the CVE details site. |
TFTP
This is a UDP based management protocol, often running on port 69. TFTP stands for Trivial File Transfer Protocol. The protocol is usually used in internal networks to transfer a file to or from one server to another. These files can be config files or ROM images to VoIP handsets and other devices.
The client sends a write request to the server it wants to send a file to. When the server acknowledges the communication bytes of the file are then sent to the server until all of the bytes have been received.
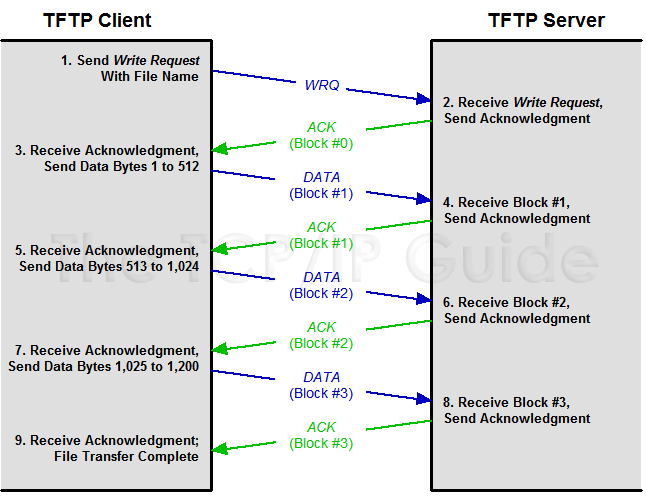
Security Weaknesses
When the file transfer occurs there is no authentication and no encryption of the data being sent. This means that any host with access to the server running TFTP can enumerate the stored files. They can download these files and they can also arbitrarily upload files. Other TFTP server flaws exist and many CVEs have been recorded.
| Weakness | Description | Exploit |
| No authentication is required. | Anyone with access to the server running TFTP and hosting files can then access these files without needing a username or password. | The Nmap script, tftp-enum, can be used to enumerate files on the TFTP server. A Metasploit module also exists to enumerate these files. |
| No transport security. | The protocol does not encrypt data when in transit. If the client-server communication can be intercepted, these (often configuration) files can be retrieved. | Tools such as Wireshark can be used to eavesdrop on networks. |
| Arbitrary file upload capabilities. | Anyone with access to the TFTP server can upload any file. | Ensure your host is running TFTP. Connect to the server running tftp root > tftp <IP> |
| TFTP directory traversal. | In some different vendor TFTP servers, such as Cisco and NetMachanica, it was possible to carry out a directory traversal attack. | Metasploit modules exist, such as netdecision_tftp_traversal. There are Nessus plugins to detect these vulnerabilities. Other exploits also exist and CVEs can be searched. |
Telnet
This protocol is commonly found on TCP port 23. The purpose of telnet is to allow command-line access to servers. This can be used to test connectivity to remote machines and issue remote commands.
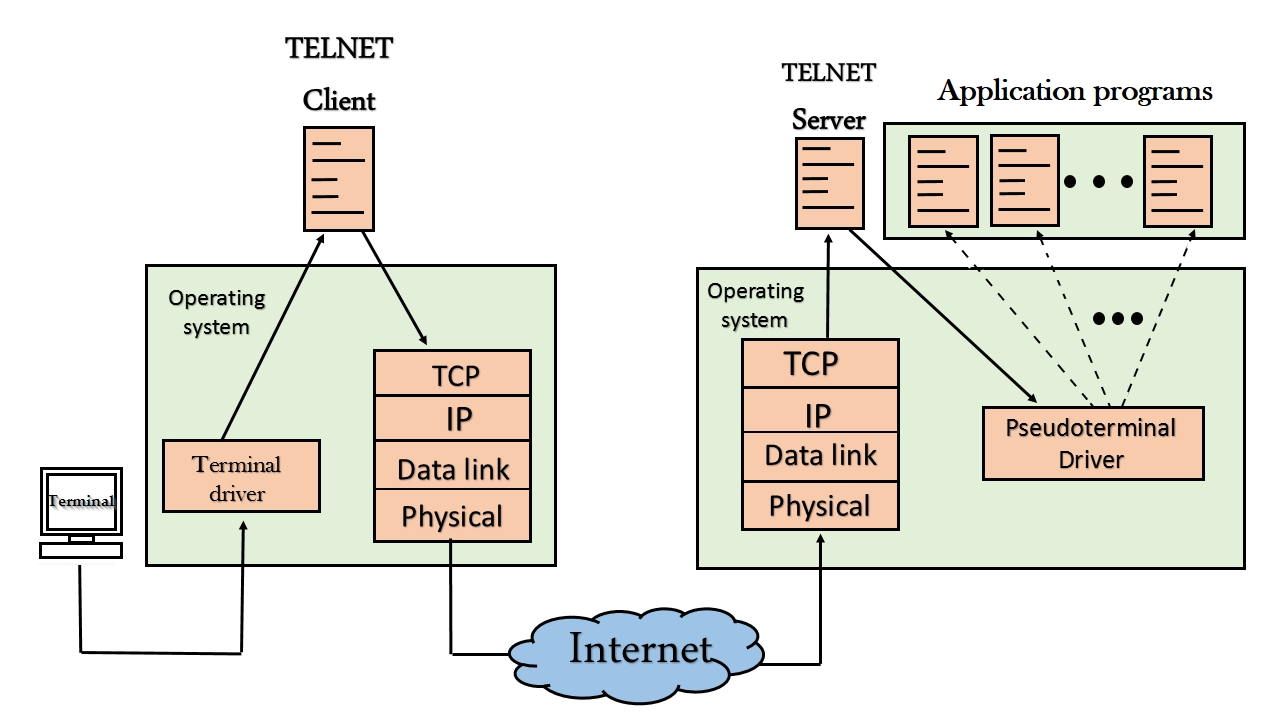
If you get lucky then Telnet may allow access to a shell through the use of default credentials. To authenticate to the server you can run the below commands.
root > telnet <Remote Server IP> login: <username> password: <password> (this will be blank) C:\Users\<username>
When connected, you may be able to enumerate that user’s files, and depending on the access level of that user, achieve other mischief and malicious activities.
Security Weaknesses
There is no transport security meaning that data is transmitted in plaintext.
| Weakness | Description | Exploit |
| Unencrypted communications. | It can be possible to intercept a user logging into the server running telnet, the commands issued and other information that may be sensitive. | Tools such as Wireshark can be used to eavesdrop on networks. |
| Default credentials. | Default credentials can provide shell access to the server. The shell is used for interactive communication with another host. | You can use a Metasploit module to enumerate valid credentials to the service. This being telnet_login. Default credentials can be specified. You can also use Nmap’s telnet-brute script to brute force passwords against telnet servers. |
| Fingerprinting other exposed telnet services. | Versions of Telnet services may be exposed when if they have not already been picked up by Nmap scans. This may reveal or allow a connection to these services. | You can state the service port to try and fingerprint the version.root > telnet <IP> <service port> |
NTP
The Network Time Protocol is used for clock synchronization between computer systems. The protocol usually runs on UDP port 123 on network devices and UNIX systems.
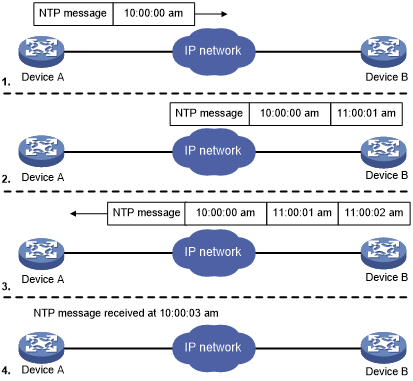
The NTP service can be queried by using the below commands. Each command may reveal different information about the service and potentially IP address information of peers of that service. These were sourced from HackTricks.
ntpq -c readlist <IP_ADDRESS> ntpq -c readvar <IP_ADDRESS> ntpq -c peers <IP_ADDRESS> ntpq -c associations <IP_ADDRESS> ntpdc -c monlist <IP_ADDRESS> ntpdc -c listpeers <IP_ADDRESS> ntpdc -c sysinfo <IP_ADDRESS>
Security Weaknesses
NTP is commonly found on network devices. This will often run on external hosts also. If the protocol is not configured correctly, remote commands can be sent to query this service. Some of the actions can allow version and other network host information to be disclosed.
| Weakness | Description | Exploit |
| Easily query server software version. | Certain versions of the software are vulnerable to a number of CVEs. These CVEs can be used to perform DoS, execution code overflow, etc; allowing an attacker to gain a more privileged position on the network or disrupt the running of a system. | CVEs and their relevant details can be found in CVE details. The below command can be used to gather the software version. root > ntpd -version |
| May leak OS version. | This can allow the attacker to tailor or find an existing attack to that accessible client. Certain OS versions have existing exploits that may allow remote code execution. | You can use Nmap ntp* scripts to enumerate information from NTP. You can use Unix tools such as ntp-fingerprint to enumerate the OS versions. |
| May leak NTP configuration. | If the NTP configuration is leaked then IP addresses of peers may also be leaked in that configuration. This may allow attackers to more easily map out the target’s network. | You can query NTP services in Nmap using ntp-info and ntp-monlist scripts. |
| NTP DDoS attack | NTP uses UDP, meaning packets are just sent to the server without integrity checking or verification. A packet can be crafted to spoof the sender and then send to the target. the response may contain a large amount of data. The get monlist request is sent repeatedly (spammed) making the server reply and causing a DoS. | You can use the below command to test if the server responds to the vulnerable get monlist command.root > ntpdc -n -c monlist |
Revision Sources
- 💜 Book: O’Reilly Network Security Assessment by Chris McNab (latest edition).
- 💜 Google all the things. HackTricks is particularly helpful.
—
Thank you for reading, you made it! If you are about to partake in CPSA/CRT then good luck to you! I hope that this has helped you at least a little bit.
Leave a comment if there were any protocols I have missed that you may want more information on and I will try my best to help where I can. This post has but only scratched the surface of what is a wonderful ‘web’ of protocols.
Sarah <3

What are some common weaknesses and vulnerabilities found in management protocols, and how can they be exploited, as discussed in your blog post?
Hi!
Let’s pick an example from the protocol and go through that 🙂 Trivial File Transport Protocol (TFTP) is a management protocol, as it allows the user to add, delete and transport files (to name a few functions), and in general you could call this file management. The biggest weakness is that it transports data in plaintext, so anyone with access to the network may be able to use a tool called Wireshark to view the data packets and therefore see what data is contained in the file. This could be sensitive data if used inside of an organisation and could lead to data leaks if said data was to be shared to unauthorised parties.
Other exploits could just be CVEs for certain protocols and versions of that protocol. Check out the CVE database for info on specific exploits, depending on what ones you are interested in – https://cve.mitre.org/.
I hope that answers your question!