Estimated Difficulty: 💜💜💜🤍🤍
Recon, Recon, Recon
One of the most important phases of an attack, is the reconnaissance phase. Often abbreviated to recon, this phase usually consists of a variety of process and techniques to collect information about a target system. This phase may also be known as “Information Gathering” as the main goal is usually to attempt to gather as much information about a target as possible.
The recon phase is also the first step of the Cyber Kill Chain. The Cyber Kill Chain, developed by Lockheed Martin, is a framework to help identify and visualise the phases of an attack.
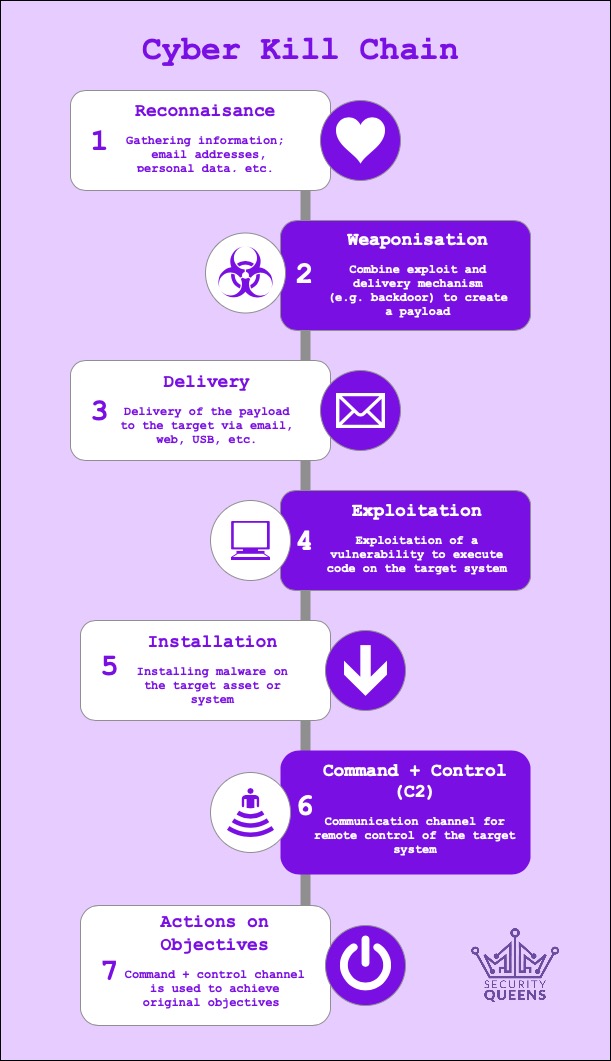
A huge thanks to Morgan for whipping up this excellent graphic!
Techniques that may be used during recon include: Footprinting, Host Discovery, Scanning and Enumeration. Using these techniques in cohesion helps an attacker enrich their understanding of the target, using this knowledge to help tailor their attack to be successful and “silent” to avoid detection.
This blog will primarily focus on the Scanning technique, walking through the basics of the tool Nmap.
What is Nmap?
Network Mapper (shortened to Nmap) is a port scanner used for both host discovery and target enumeration. Often the “go-to” for the first step in either an attack or a pen-test, Nmap helps you get a feel of the type of system you are attacking – identifying the types of services running with the capability to also identify potential vulnerabilities.
Nmap can be used against an entire network, to identify and scan multiple hosts, or against a single target. By default, Nmap will scan for the top 1000 most popular ports and services.
What is Port Scanning?
Port scanners are applications/tools that allow you to identify the types of ports open and running services on a system. To put it bluntly, it’s identifying the “open doors” and potential entry points into a system.
Using a port scanner is a form of active recon, as traffic/packets will be sent to the target in an attempt to identify ports and services. This is important to understand, as aggressive scanning can potentially create noise that may alert the target.
Types of Port States
Scanners help identify port states during a scan, and there are several states a port can be in. The states that Nmap recognises are: open, closed, filtered, unfiltered, open|filtered and closed|filtered.
Open: The port is actively running a service and is listening and accepting connections
Closed: The port has no application listening on it and is not accepting connections
Filtered: The port is being block and/or protected by a firewall, filter or something similar – Nmap will return a “filtered” port if it cannot determine what state the port is in
Unfiltered: The port can be accessed, but Nmap cannot determine what type of port it is
Open|Filtered: If an port does not give a response, Nmap may class it as open|filtered as it is unsure if it is open or filtered
Closed|Filtered: This state is used when Nmap cannot determine if a port is closed or filtered
For more information on port states, have a look here.
Using Nmap
The following section will detail basic syntax and options used to carry out a simple Nmap scan through a Linux command prompt/terminal using Command Line Interface (CLI). Nmap can also be used on Windows, and you can also use Nmap as a GUI by downloading ZenMap (checkout ZenMap here).
Basic Syntax
nmap <target>
Useful Flags
Flags can be used to help specify the type of scans you want the scan to complete. This can range from identifying versions and banner grabbing to identifying the port scanning range – and so much more! Below are the flags that I have used the most in the past:
Detect Service Version
This scan will attempt to detect the version of services running on a port.
nmap -sV <target>
UDP Scan
This scan will check the UDP ports on a system.
nmap -sU <target>
OS Detection
This scan will attempt to identify the operating system (OS) running on a system.
nmap -O <target>
Full TCP Scan
This scan will complete a full TCP handshake (SYN, SYN/ACK, ACK) connection to identify ports and services.
nmap -sT <target>
SYN Scan
This scan will terminate the connection mid-TCP handshake (SYN, SYN/ACK, RST).You may want to use this scan if you would prefer to make less “noise” during your scanning phase. By terminating the connection early, sometimes the connection is not registered by the target. Sometimes this scan is dubbed a “Stealth Scan”.
nmap -sS <target>
All Ports
By default, Nmap will scan for the top 1000 most popular ports and services. Using this scan will scan for all the ports.
nmap -p- <target>
Ping Scan
Ping scans can be used to scan an entire network to identify hosts. This scan will send out pings, and list the machines that respond.
nmap -sP <target>
Aggressive Detection Scan
An aggressive detection scan will complete the following all-in-one scan: OS detection (-O), version detection (-sV), script scan (-sC), and traceroute (–traceroute).
nmap -A <target>
Using Scripts
Nmap has a huge amount of scripts that you can run along side the port scanning function. These scripts range from brute forcing credentials on a service, to further service-specific enumeration. To have a look at all the scripts Nmap has to offer, go to here.
To use a script, use the following syntax:
nmap --script=<yourchosenscript> <target>
Types of Output
You can specify the type of output from a Nmap scan by using flags. If you do not specify an output, by default Nmap will just display the output in the terminal.
XML Format
nmap <target> -oX myFile
Nmap Format
This format will be identical to the output generated by Nmap by default in the terminal. This will create a .nmap file.
nmap <target> -oN myFile
Grepable Format
This format will create a file that can grep can be used on to search for specific text. This will create a .gnmap file.
nmap <target> -oG myFile
All Format
Using this flag will create an XML, Nmap and Grepable Nmap output at the same time.
nmap <target> -oA myFile
Timing
You can set different timing settings to control the aggressiveness of the scan. Nmap has six different options, ranging from 0 to 5.
T0: Paranoid
T1: Sneaky
T2: Polite
T3: Normal
T4: Aggressive
T5: Insane
To use the timing options, use the T value as a flag (-T<option>)
Common Ports and Vulnerabilities
Here’s a quick rundown of some common ports (and their vulnerabilities) that you may come across in a scan – including further enumeration steps that you can take to find out more about the service.
FYI: This isn’t a complete list, there are loads other vulnerabilities/further enumeration steps that can be included in this table!
| Port | TCP/UDP | Service | Vulnerabilities/Further Enumeration Steps |
| 21 | TCP | FTP | Anonymous Login Upload/Download Files Unencrypted |
| 22 | TCP | SSH | Brute Forcing File Transfer (SCP) |
| 23 | TCP | TELNET | Banner Grabbing Cleartext Brute Forcing |
| 25 | TCP | SMTP | Enumerate User Accounts (VRFY, EXPN, RCPTTO) Unencrypted Send Emails |
| 53 | TCP | DNS | Enumerate DNS (Lookup) Zone Transfers (Host + Dig) DNS Spoofing |
| 69 | UDP | TFTP | File Transfer Unauthenticated (But you may not be able to list files) Upload/Download files Paired with SNMP |
| 80 | TCP | HTTP | Not Secure/Encrypted Web Vulnerabilities Enumerate Web Server: Nikto, Dirb(uster), Metasploit Scanners |
| 88 | TCP | KERBEROS | Signposts DC (Domain Controller) Purpose Compromise = Potential to Generate Tickets Ticket Attacks (e.g. Kerberoasting) |
| 139 | TCP | SMB | Enumerate Machine (Enum4Linux) RID Cycling (Enumerate Users) Null Sessions Access Open Shares |
| 143 | TCP | IMAP | Transmits Messages in Plaintext |
| 161 | UDP | SNMP | Use of Default Community Strings (public/private) Enumerate MIB/System/Network Information Enumerate Default Gateways/Router Addresses Enumeration: snmpwalk, snmpcheck, onesixtyone |
| 389 | TCP | LDAP/SSL | Enumerate LDAP Directories: JXplorer (GUI) |
| 443 | TCP | HTTPS | Web Vulnerabilities Enumerate Web Server: Nikto, Dirb(uster), Metasploit Scanners |
| 445 | TCP | NETBIOS | Enumerate Machine (Enum4Linux) Null Sessions Access Open Shares |
| 1433 | TCP | MSSQL | Potential Default Credentials to Database Pre-existing Exploits Enumeration: Metasploit, Squirrel |
| 3306 | TCP | MySQL | Default Credentials to Database Pre-existing Exploits Enumeration: Metasploit, Squirrel |
| 3389 | TCP | RDP | Remotely Access Systems Potentially Default Credentials (Guest Account) Rdesktop |
| 5800 | TCP | VNC | Remotely Access Systems No Authentication (Older Versions) VNCViewer |
| 5900 | TCP | VNC/HTTP | Remotely Access Systems No Authentication (Older Versions) VNCViewer |
| 8080 | TCP | HTTP | Similar to HTTP (80) Likely to be Tomcat Admin/Management Page |
Further Resources
Here are some other resources that I recommend that you can use to learn more about using Nmap:
Andy Gill/ZephrFish Nmap Guide – https://blog.zsec.uk/nmap-rtfm/
Official Nmap Documentation – https://nmap.org/docs.html
HighOn.Coffee Nmap Cheat Sheet – https://highon.coffee/blog/nmap-cheat-sheet/
I hope that this blog has been at least some sort of use – and that you can at least go out and start scanning all the things*

*please don’t scan all the things if you do not have written permission and/or it is a target that does not serve an educational purpose. If you wish to try your new-found scanning knowledge, Nmap has actually created a machine so people can test their Nmap – http://scanme.nmap.org/
Thanks for putting all this together it’s really helpful! Didn’t realise about the Nmap machine.
Really happy that you found the blog useful! Thanks for the great feedback 🙂
Another awesome blog post! Thanks!
Cheers Dan! 🙂
Those are *literally* the linux manpages
Thanks for your feedback, this post was created for absolute beginners to give context behind the basic commands of Nmap and it’s usage. Would you like us to add anything further to the post to make it more comprehensive? 🙂
Hi Queens. I found this website by accident.. I followed a tweet and led me here.
I am new into infosec, cybersecurity, pentesting. And the way you explain the basic stuff about pen test is incredible. You keep it simple and useful, with nice images etc.
Is there any materials,from Uni or your personal collections, like pdf etc you could share with me?
The areas I am focusing is : networking, Linux, priv esc and some very basic scripting stuff.. I think you can see my email..
My ultimate goal is the OSCP but unfortunately I can’t afford the cost atm.
Thank you in advance and keep on the good work :))
Hi there, welcome to our website! 🙂 I’m glad to hear that you’re enjoying our content so far. If you keep an eye on our website we are hoping to create a learning resources page where we will be sharing items such as pdfs, other blogs, labs etc. Thanks once again for your feedback, we hope that you enjoy our content in weeks to come!