Estimated difficulty: 💜💜🤍🤍🤍
Need to bruteforce directory names on a web application? Or perhaps you need to find unlisted files on a web server? Who ya gonna call? DIRBUSTER!
So first thing’s first, the boring pentesty theory bit before we do all the mad hax and walkthrough the basics of Dirbuster. Remember this neat little graphic from a few blog posts ago?
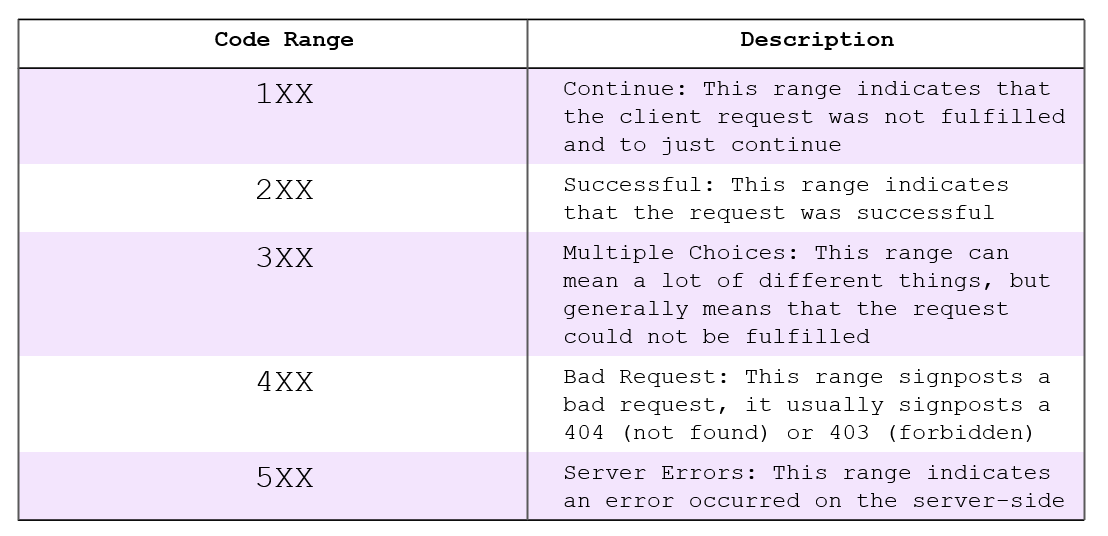
DirBuster was written by OWASP, the Open Web Application Security Project, as a tool specifically to brute force directories and filenames. Using DirBuster is a great tool to use in the reconnaissance phase of your attack and/or test. DirBuster (and other similar tools) allows you to enumerate the web application or server to help identify and map accessible directories and files. By bruteforcing a list of directory and file names, DirBuster helps identify present directories and files by listening for positive responses (any response in the 200 range). If DirBuster establishes a 403 (Forbidden) code, you can assume that a file or directory is there – but it is not accessible and is private.
DirBuster helps automate an otherwise laborious process of trying to map out the structure of a website, could you imagine manually trying hundreds (or thousands) or URL paths to see if a resource is there?
So let’s have a quick chat about how websites work and the structure of a web server…
Remember this graphic from Stop! In the Name of Web: Intercepting Traffic With BurpSuite (A Beginner’s Guide)?
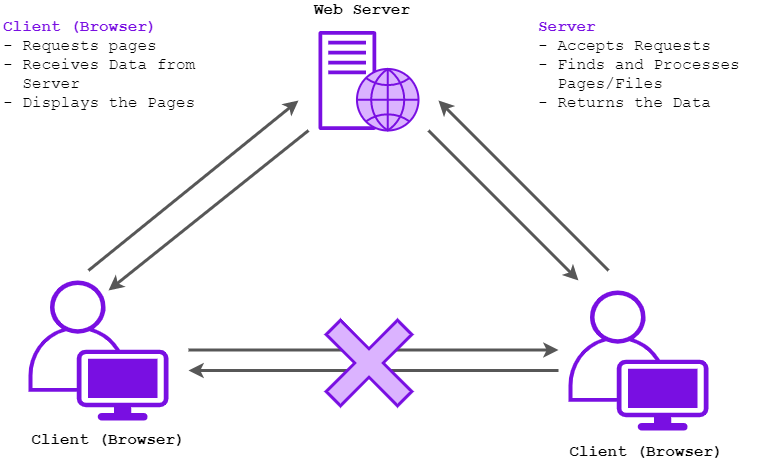
Clients are used to request web pages from the web server. The web server accepts requests and returns the correct page to the client, displaying it on the browser. Browser don’t usually directly communicate with each other over the internet but rather act as a gateway between the user and the web server.
On the web server, there could be two types of resources: static and dynamic. Static resources are those such as stored HTML pages or images and scripts, dynamic resources are a combination of static resources and things like databases and backend applications. Commonly web servers are dynamic, that hold a selection of static resources but also use an application to retrieve information from a database.
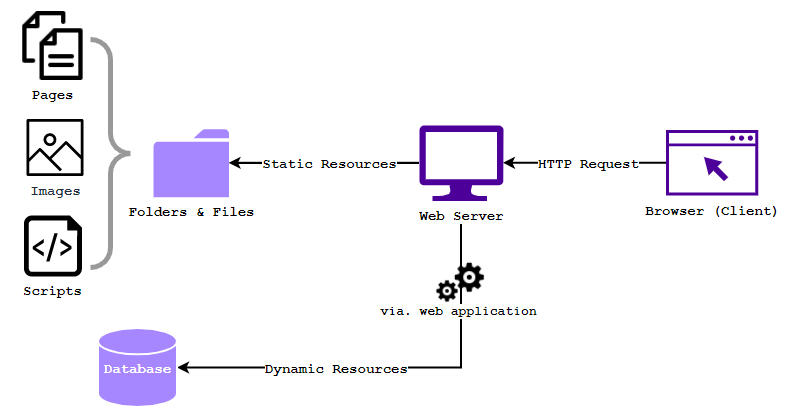
The way tools like Dirbuster work, will make hundreds of requests to the web server searching for files and directories that may be there. Dirbuster will attempt to bruteforce and check for directories and files based on a wordlist set by the attacker. It may also attempt to use a method called directory traversal to navigate out of the root or default directory on the web server, to try retrieve other directories deeper into the server itself. Using tools like Dirbuster helps us understand the attack surface of a website, and we can begin to map hidden or confidential directories that should not be accessible by the public.
Using DirBuster: The Basics
If you have a Kali instance, DirBuster is installed by default. Simply open a terminal, and type “dirbuster” to launch it, or you can manually search for it in the applications GUI menu.
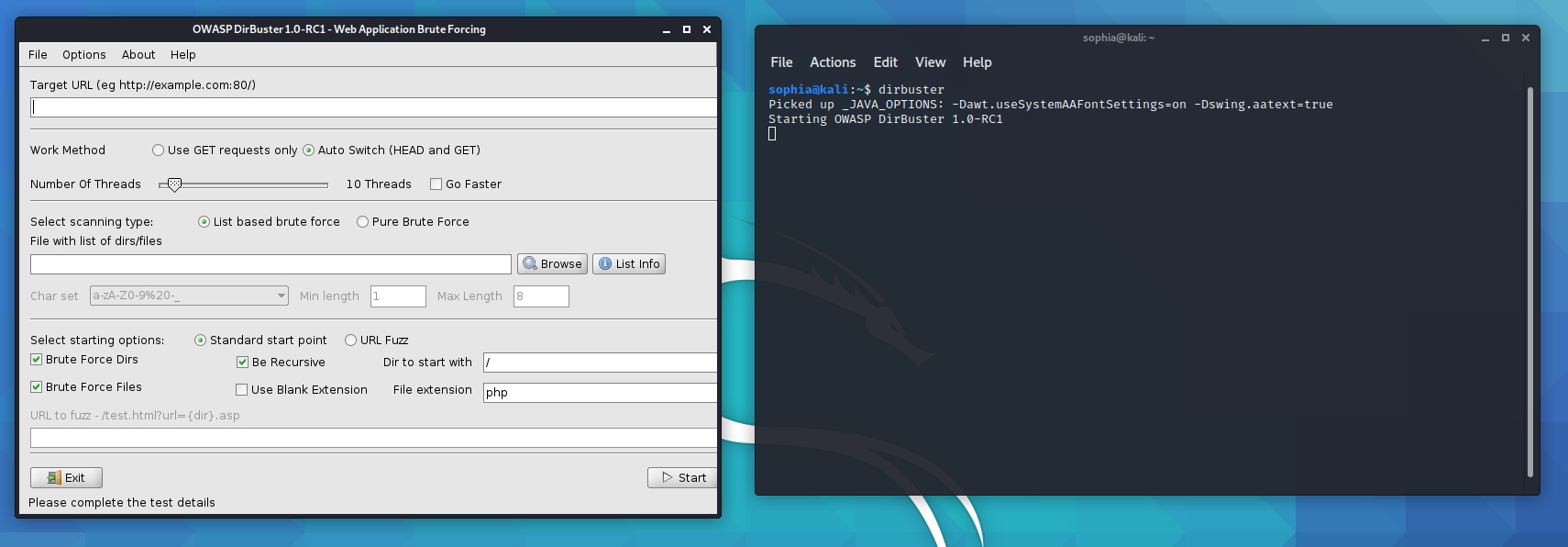
The first thing we want to do is set a target URL, for this walkthrough I will be using DirBuster against a DVWA instance. DVWA stands for “Damn Vulnerable Web Application” and is an application that was designed to be deliberately vulnerable! Created by dijininja, the aim of DVWA was to host a space where you can practice attacks against common web vulnerabilities, such as cross site scripting and SQL injection. You can find more information about DVWA here.
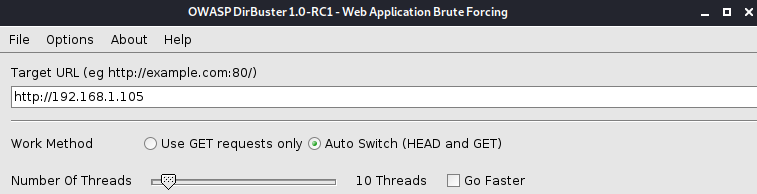
Simply type your URL in the text box, remember to add ports if necessary! Don’t worry about the “Work Method” option or the “Number of Threads” option for now.
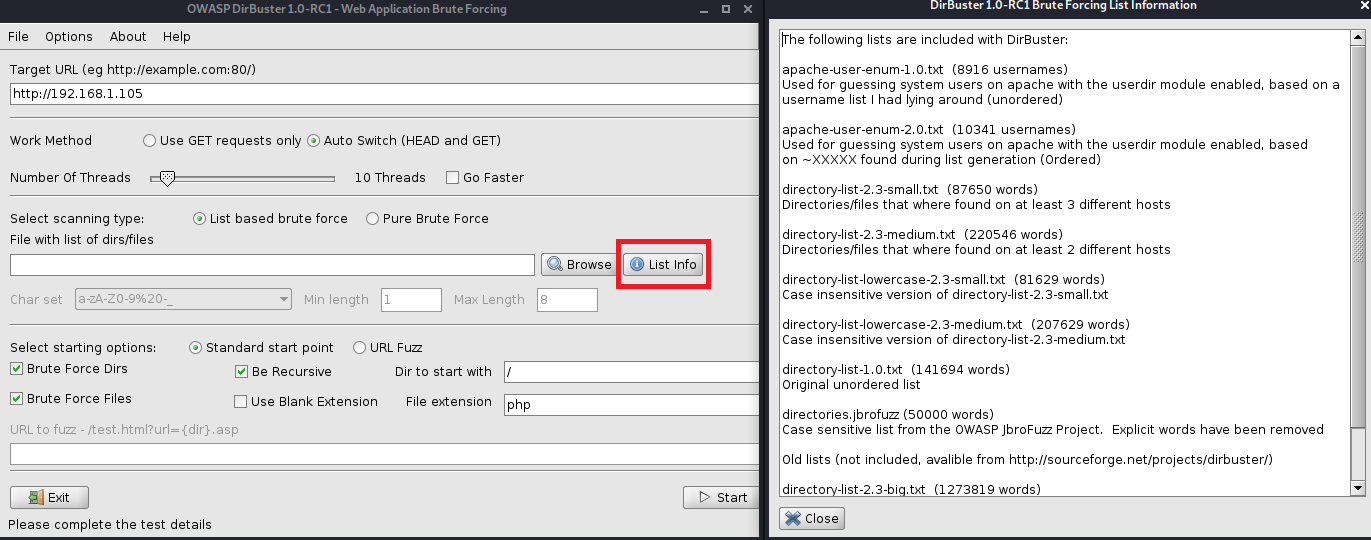
Next we need to choose a wordlist! Lucky for us, DirBuster has default wordlists built into the application. The word lists can be found at:
/usr/share/dirbuster/wordlists/*
Or you can click “List Info” on the GUI to view the available lists and their descriptions
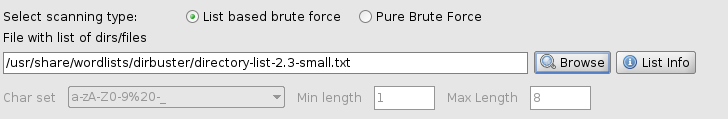
For this walkthrough I am choosing the “directory-list-2.3-small.txt” wordlist.
Simply type the full path to the wordlist in the text box, like below:
And press start! The DirBuster GUI will start to show you all the directories and files it finds. You can choose to see the results in a list, or in a directory tree view:
You can pause or stop the scan if you desire, or change the number of threads mid-scan (increasing the threads makes it “go faster” but can also give you a lot of false positives or break the scan). And voila! That’s a very basic introduction to how to use DirBuster!
A neat thing about DirBuster, is you can also use a CLI version (Dirb) in Kali as well. To use the CLI version simply type the following in a terminal:
dirb <target URL>
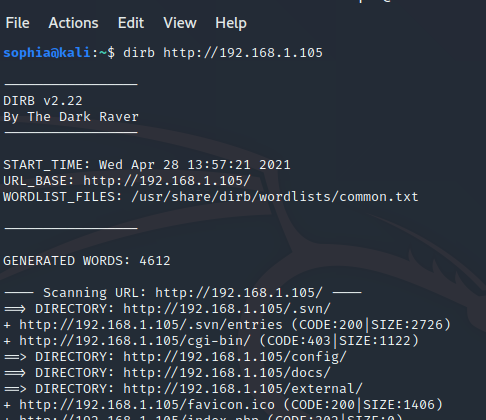
Dirb will automatically opt to use the “common.txt” wordlist, but you also specify a wordlist by simply typing the full wordlist location after your URL:
dirb <target URL> <wordlist>
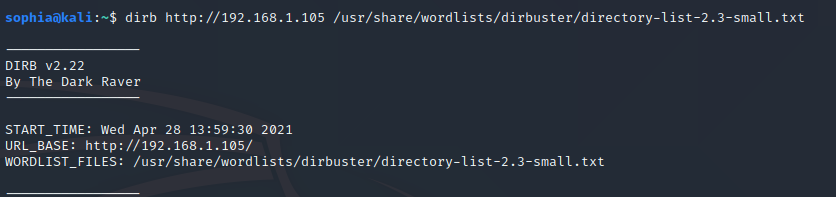
Even though the default wordlists are pretty good, I definitely recommend having a look at the SecLists git repository for all your wordlist needs. You can find the repo here, simply git clone it then specify your chosen wordlist when using Dirb/DirBuster or any other tool!
If you’re not too keen on DirBuster, there’s also a few other directory bruteforce tools you can use. I’ll list them below so you can have a gander:
Further Resources
Still a little stuck? Have no fear! Here are a few additional resources on DirBuster:
NullByte “How to Find Directories in Websites Using DirBuster”
“How to install DirBuster on Linux? Simple way of how you can install and use DirBuster”
I hope you enjoyed this “rapid read” intro to DirBuster, next time we’ll look a little into SQL injection!
– Sophia x