Estimated difficulty: 💜💜🤍🤍🤍
Authentication. A familiar “buzzword” we see that is parroted in all things security, a selling point for many vendors, and a well-known term written (quite a lot) by pen-testers in their final reports.
But what exactly is authentication? Well, in reality authentication is a complex and sizeable topic, but to get you started the following blog will detail the nitty-gritty essentials for authentication basics. First thing’s first, authentication in short? Basically…

The Triple A (AAA)
Nope, this isn’t referring to tiny batteries. Rather, it’s a security comparison that stands for “Authentication, Authorisation, Access Control”. Most of us would have heard of the almighty CIA triad (Confidentiality, Integrity, Availability), the power triangle of security principle, but using “The Triple A” can also help you understand the complete process of mediating access.
What’s the difference between the three?
Authentication: Verifying the identity of a user to ensure they are “who they say they are” e.g. using credentials

Authorisation: A process which specifies what and where an authenticated user can access e.g. specifying rights to access admin areas

Access Control: Restricting access of a user based on the authentication and authorisation processes

Authentication Factors
As previously mentioned, authentication is the verification process to ensure the identity of a user. Usually the process will require something unique to the user to complete the verification, such as credentials or biometric data. This “something” can be based on one of three different authentication factors: Something You Know, Something You Have or Something You Are.
Something You Know
Probably the most common of the three, this is usually something that you mentally possess i.e. “you know”
Examples:
- Passwords/credentials
- Secret words (known by both the user and the authentication party)
- PINs (Personal Identification Numbers)
Unfortunately, this type of authentication is also the easiest to beat. But there’s more on password authentication attacks and threats later on in the blog…
Something You Are
This factor is pretty self-explanatory, and usually attributes to physical or biological characteristics of an individual.
Examples:
- Fingerprint scanning
- Iris scanning
- Voice analysis
- Facial recognition
- Hand geometry analysis
Traditionally biometric authentication, although not impossible, is one of the harder authentication factors to “break”.
Something You Have
This type of authentication may be issued or self-acquired, and refers to something that you may physically or electronically possess.
Examples:
- ID cards
- Key fobs
- Electronic tokens (e.g. OTP (One-Time Password) generators)
- Smart cards
- Electronic forms of cards (e.g. CryptoCard, Activcard)
“Something You Have” Authentication is commonly used as part of multi-factor authentication and/or 2FA (two-factor authentication).

Multi-Factor & Two-Factor Authentication
To improve the security behind authentication, some processes may use two or more factors to authenticate a user. Two-Factor Authentication (2FA) or Multi-Factor Authentication (MFA) are used to strengthen authentication processes. The factors must be different types from each other, and provides a layered defence against authentication attacks.
For Example…
Bob would like to login to his email, and has 2FA set up using an authentication app which provides tokens that change regularly.
First, he is prompted with the login screen – he types in his credentials.
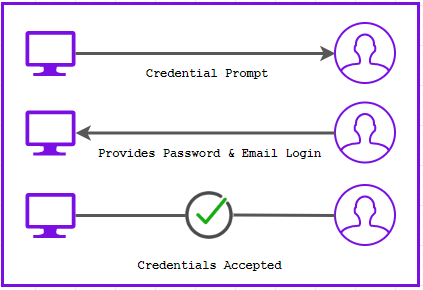
Following this, he is prompted for his token from his authentication app.
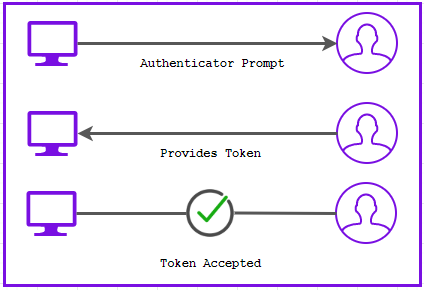
Given that the credentials are correct, and the token from his authentication app matches the token produced by the authentication server linked to the app – he successfully logs in.
Using multi-factor authentication such as in this example can help users that have been affected by password breaches/dumps, or credential phishing emails – where their password i.e. “Something they know” has been compromised. By adding an additional layer of authentication, this challenges attackers that may only know one of the factors in multi-factor authentication.
Non-Repudiable v Repudiable
Authentication can be broken down into two basic types: non-repudiable and repudiable. There are other types of authentication, such as session authentication, however these are the two most common types.
Non-Repudiable: This type of authentication has factors of which cannot be changed and/or the source cannot be challenged. Commonly this includes characteristics such as biometrics e.g. fingerprints and iris scans.
Repudiable: This type of authentication has factors of which may be deemed unreliable, such as items that can be forgotten, duplicated or imitated. Commonly this type of authentication can be things such as passwords.
Common Authentication Methods
There are plenty of different authentication methods, listed below are some of the most common authentication methods used…
Passwords: Either text-based or graphical, this is the most “traditional” form of authentication
Public Key: Each user of this authentication scheme must generate a pair of keys between 1024 and 2048 bits in length. These public-private key pairs are typically created using a key generation tool, the server will know the public key (as it is publicly published) – however only the user will have the private key.
Anonymous: Anonymous authentication can be implemented by creating an “anonymous” account that anyone can use. Anonymous accounts should have restricted access to sensitive files and areas of the system.
Biometric: Using physical and biological attributes such as fingerprints to grant access to users.
Digital Signature-Based: Commonly used in emails, this method doesn’t require credentials but rather utilises an electronic signature that relies on public-key infrastructure (PKI) to verify identities.
Password Authentication: The Basics
Password authentication is one of the most common ways to authenticate a user. A few weeks ago, fellow Security Queen Sarah wrote about password practices, you can find the blog post here. But how does password authentication actually work? And what are the threats and security challenges do we face using password authentication?
How Does It Work?
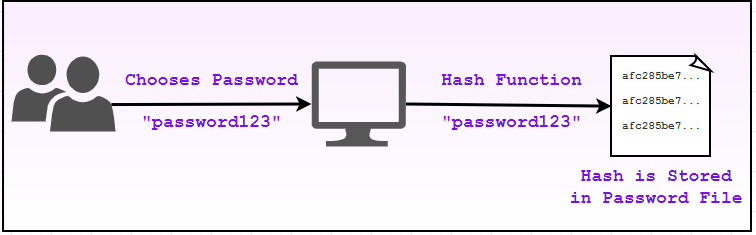
Step #1 – Setup
During the setup of an account, the user is prompted to create a password of their choosing to use with their username/credential. Once this password is created, the password is hashed and stored into a password file (of some sort).
Step #2 – Authentication
If a user wishes to access a system or an account, their credentials and password are requested via. a prompt. The user supplies the password, of which the system will then hash the supplied password to then compare to the password file.
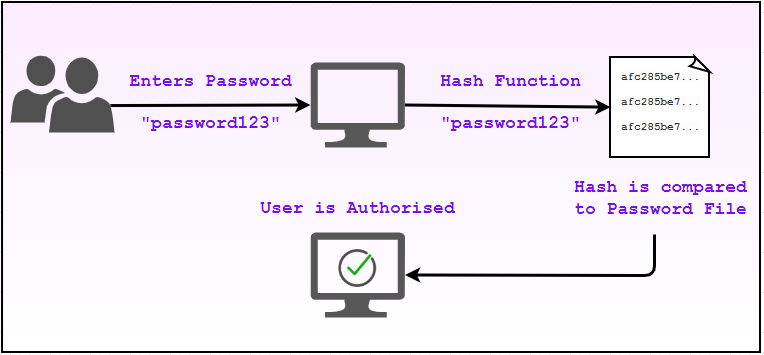
If the hash matches the one in the password file, the user can be authorised – Ta-da!
Password Authentication Threats
As one of the most used authentication methods, unfortunately there are also a number of authentication threats specific to password authentication. This can range from anything from disclosure to cracking, a few are detailed below…
Disclosure: The user may willingly disclose their password to people of whom they think they can trust, or store the password inadequately e.g. post-it notes stuck on desks
Loss: Forgetting passwords, or the susceptibility to forget a password
Breaches/Exposure: Passwords may be leaked as part of a system and/or database breach. Sometimes these passwords are sold illegally online in the cybercrime space e.g. dark web and deep web selling forums and sites
Snooping/Eavesdropping: Attackers may install keyloggers on compromised systems to log keystrokes to obtain passwords, or intercept network communications in an attempt to capture passwords
Guessing: Attackers may attempt to guess passwords by using common passwords or conducting Open-Source Intelligence (OSINT) to find out more information on the individual to conduct educated guesses e.g. pet names
Reuse: If a password is compromised from one user account, attackers can attempt to reuse this password across different accounts of the victim.
Finito.
If you have made it this far – well done! I reward you with this adorable pupper…

This blog was based on my “Enterprise Security & Privacy” unit from my undergraduate degree. As always, constructive criticisms are welcome.
– Sophia x