Estimated difficulty: 💜🤍🤍🤍🤍
Content Warning: This post includes discussion of sensitive topics such as revenge porn and blackmail.
This week I’m primarily going to cover sextortion phishing campaigns, and a little about how to deal with these sorts of emails. I’ll also include some resources at the end of the post discussing general (non-phishing) sextortion, and organisations who can help if somebody tries to blackmail you with, or releases your personal content without your consent.
For a little background, one of my friends messaged me a while back about an email she’d received, asking for advice. 🤔
Here’s a screenshot of the email:
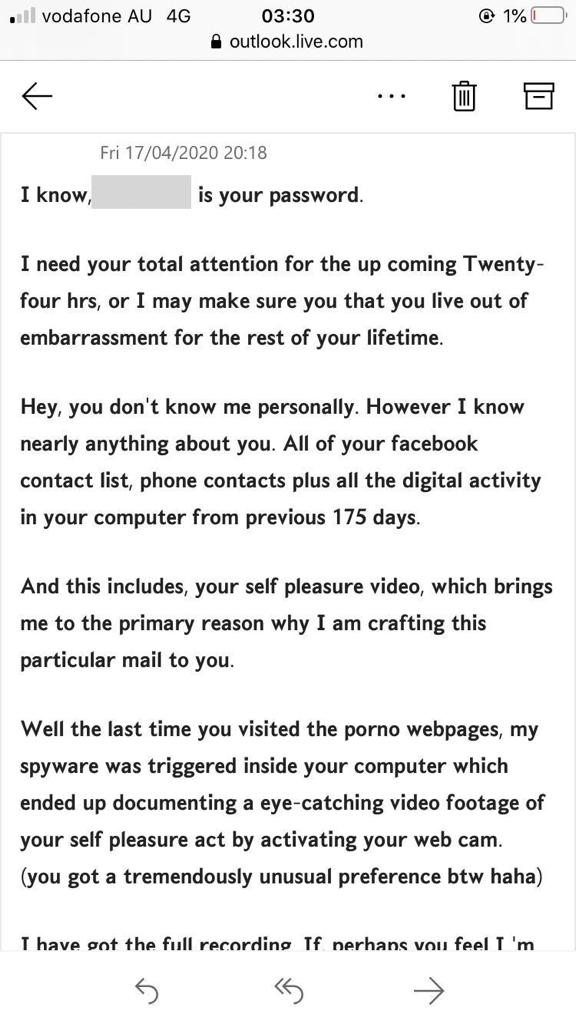
Sextortion emails are quite wicked, and the key reason they have more emotional impact than regular phishing emails is because in addition to the tone of urgency and sense of danger, the main area of focus (sex, pornography, and so on) is very taboo. They contain just enough personal information (like your username and password, harvested from a data breach) to convince you they’re real, and that someone really does have pictures or a video of you doing something private. Because the subject is so taboo, people might not immediately realise they’re basically just phishing emails, and a lot of people who receive sextortion attempts likely won’t have the technical knowledge to be confident that the sender doesn’t have the content they’re trying to blackmail them with.
Sextortion emails will usually have some of the standard hallmarks of a phishing email; they probably come from a spoofed domain (for non-technical readers, this is a technique used to make it look like an email came from someone you might trust), the grammar and spelling might be poor, and they’re using threatening language to try to force you to urgently take action – usually sending them money. 🤑
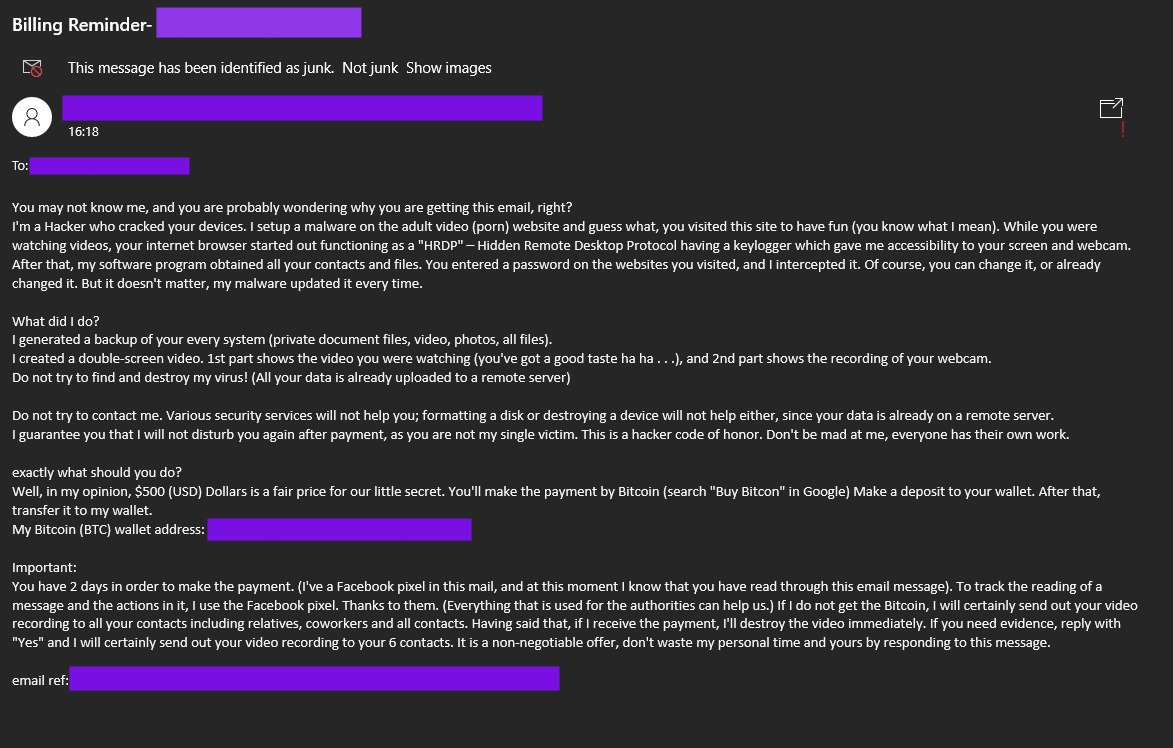
NB: A variation of these that you might see in a professional environment involves an attacker harvesting credentials from a public breach (usually something like the LinkedIn breach), and emailing an encrypted PDF containing the sextortion threat to corporate users. The PDF will typically be encrypted using the recipient’s password, which will be in the subject line. Encrypting the PDF helps the content bypass spam filters and other perimeter security measures. PDFs can often be used to spread malware too, if the PDF reader allows embedded code to be executed. Another recent variant on this sort of campaign involves the sender threatening to infect the recipient’s family with COVID-19 if they fail to pay a ransom (usually requested in cryptocurrency).
So what IS phishing? 🎣
Phishing (in case you don’t know) is the term used to describe malicious or fraudulent emails that look like they’re from a legitimate or trusted party, usually sent for the purpose of tricking someone into giving up information or money. Sometimes other channels are used for similar purposes, like vishing (voice – over the phone) or smishing (SMS – text message) – more on these in later posts.
Here’s a handy graphic that calls out how to spot red flags in suspicious emails:

Here’s what you can do to keep yourself safe:
Firstly, it’s super important that you don’t reuse your passwords across different platforms. It can be difficult to remember different passwords for every online account you have, but the big risk with using the same password for everything is that if one service has a breach and your password is stolen, it’s trivial for someone to use that password to access your other accounts.
If you want more information on setting strong passwords, check out Sarah’s post from last week on good password practices. She also talks a little about password managers – a password manager is basically a virtual safe on your device that saves your login details for different apps and websites, so that you can use different, strong passwords and not worry about forgetting them. Some password managers also suggest strong passwords for you. If you have an Apple device and you use Keychain, you’re using a password manager. 😊
Secondly, make sure you enable multi-factor authentication for things like online banking, your emails, the social media sites you use, etc. This might be the fingerprint scanner or FaceID on your phone, a push notification on an app, a specific authenticator app (like Google Authenticator or Authy), or a code sent via text message. (There’s a little debate about whether these are secure, but rest assured, even codes sent by text message offer more security than just having a password – Security Queens’ honour. 💅) Having a second factor in place means that it’s harder to compromise your account if someone finds out what your password is. Sophia will be covering this in more detail next week, if you’d like more information.
Something to keep an eye on (that Sarah also mentioned in her post) is HaveIBeenPwned. It’s a website developed to track data breaches and let you know if your account credentials or personal information has been made public – you can select “Notify me”, enter your email address, and you’ll get an email alert if your details are involved in a breach, so you know to change your passwords and be on the lookout for suspicious emails.
You can report phishing emails to the National Cyber Security Centre here, and you can also report them to Action Fraud here.
Optional extras:
I have two main email addresses – a clean (trusted) email and a dirty (untrusted) email. The clean one is only used for things like online banking, and sites and services I trust; the dirty email is one I’ve had for years, and it’s been in a few breaches, so that one gets much more spam (whereas my trusted email address hardly ever gets spam). This way, the services that are super important to me aren’t associated with an email address that’s been in breaches before.
Some people take this separation concept a bit further, and set up email aliases (Google accounts will let you set up to 30 aliases free of charge) – for example if you register with a new site, you might set your email as examplesitename@yourdomain.com. This way, if the site has a breach, it’s easy to attribute, because you’ll start getting spam addressed to examplesitename@yourdomain.com.
You can also pick up a webcam cover pretty easily – these are especially handy now remote working and video conferencing meetings are so common, for days you feel like working in your pyjamas and don’t want your colleagues to see. 💁♀️
🚨 Revenge Porn 🚨
Sometimes genuine sextortion attempts take place, or someone might legitimately have intimate media content of you – though this will usually be somebody you know. If someone tries to blackmail you with your private content, or shares this without your consent (which has been illegal in the UK since 2015 and carries the possibility of a prison sentence), there are organisations who can help. The UK Police also have specialist units who provide support with things like revenge porn and domestic violence – if you’re able to safely contact your local police, they can help.
Revenge Porn Helpline – Help for Victims Outside the UK
Check out Tia C’s blogs for advice on safely sharing personal content, and what to do if it goes wrong.
If you’re under 18, there are specialist organisations who can help:
Child Exploitation and Online Protection command
Thanks for sticking through this (delicate) post – I hope it’s helpful. 💜
If you have any questions, or other useful resources related to any of the topics above, leave a comment below. 😊
Morgan x
Morgan,
Top post. Critical points gotten across whilst handled delicately and a good selection of links for resources.
Loving all of yours, Sarah’s and Sophia’s work.
Thank you! 🥳
Appreciate the tips, see you and the other Cyber Griffins soon. 😊
Another awesome post, thanks. Explained really well with a lot of care when needed. Thanks for posting.
Thanks for the feedback, Dan. ☺️